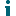InTrust Organization Configuration Overview
In the InTrust organization that you are going to set up in this scenario:
- InTrust servers are installed in each domain
- All InTrust servers are installed into one organization (this way it is possible to view all alerts in one central Monitoring Console)
- All InTrust servers share a single configuration database
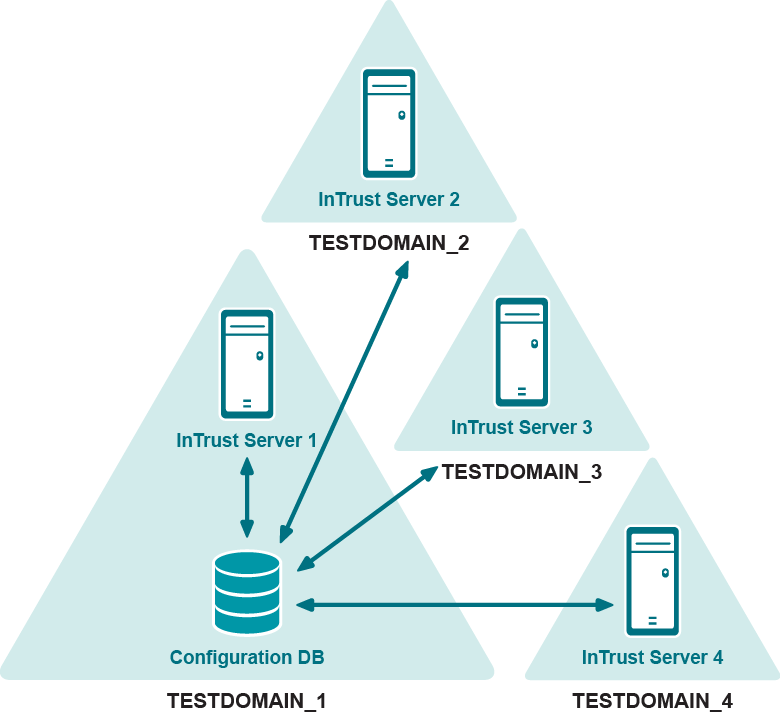
Gathering Configuration Overview
Gathering is configured as follows in this scenario:
- Audit data is collected into local repositories and audit databases in each domain.
- The central repository and central audit database stand for the local ones in TESTDOMAIN_1 (in a production environment, it would be reasonable to separate the central repository and audit database from the local ones in TESTDOMAIN_1 to speed up local report generation).
- Domain-level reports are generated and distributed in domains 2, 3, and 4.
- Local repositories from domains 2, 3 and 4 are consolidated into the central repository in TESTDOMAIN_1.
- Audit data is imported from the central repository into the central audit database.
- Consolidated reports and local reports for TESTDOMAIN_1 are generated using the central audit database.
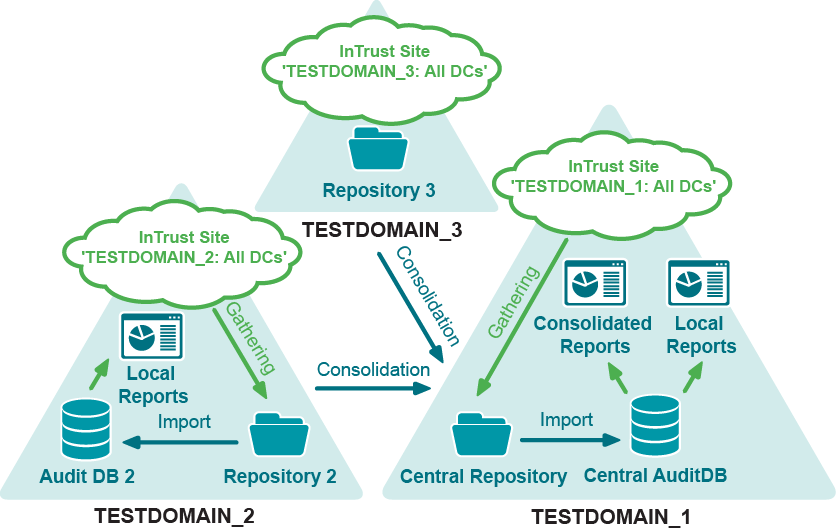
Real-Time Monitoring Configuration Overview
Real-time monitoring is configured as follows in this scenario:
- InTrust Monitoring Console is installed in TESTDOMAIN_1.
- InTrust servers send alerts to the central alert database.
- Users from all domains access Monitoring Console using their alerting profiles and get the alerts they are allowed to view (for an explanation of alerting profiles, see the Handling Alerts topic).
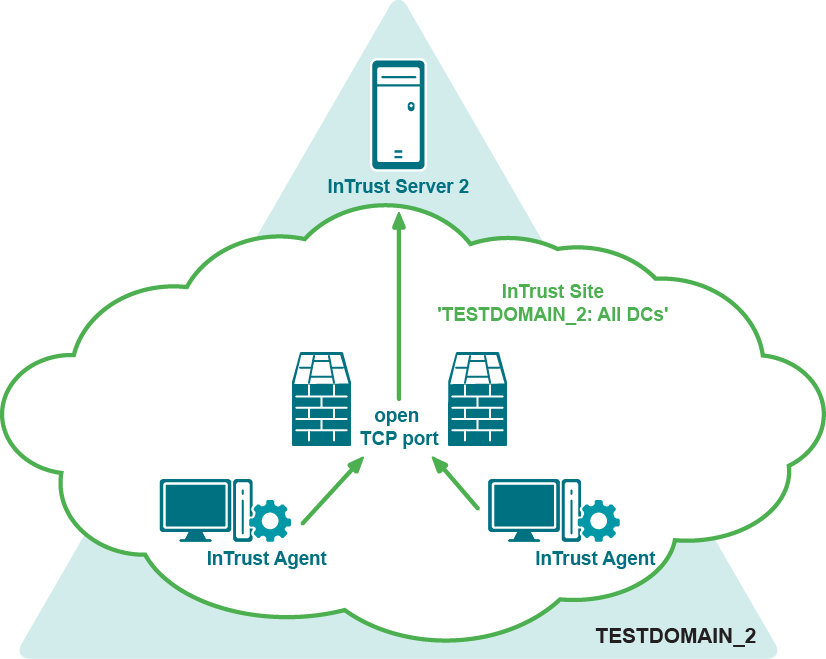
Gathering and Monitoring over the Firewall
To make InTrust agents operate over a firewall, you must open a port on the firewall to allow incoming traffic from outside to the address/port of the specific InTrust server (listening port). The listening port number that the InTrust server will use is specified during InTrust Server installation.
InTrust agents must be installed manually on computers behind the firewall; see Installing Agents Manually for details.
Installing Servers
To install InTrust servers, follow the setup steps, as described in the Performing AeCDSuiteLauncher (Extended Deployment of InTrust) topic. When installing the first server in the organization, you will need to specify a configuration database, and InTrust organization’s name and password. When installing servers into existing organization, you will have to supply this password.
|
|
Note: Do not perform server installations simultaneously—servers must be installed sequentially, one after another. |