Keeping Event Data Backup on the Agent Side
To ensure the integrity of event data from the specified data source, you can create agent-side log backups. This helps protect data from being lost event if accidental or malicious log cleanup occurs on the target machine. Log backups can be created for the most frequently used data sources, including Windows Event logs.
Agent-side log backup uses a compression method similar to that used in InTrust repositories. On average, the contents of the event cache are compressed to 1/40th their original size. Nevertheless, consider that using this feature requires additional space on the agent side. So it is recommended that you specify a reasonable retention period for agent-side log backups.
Agent-side log backup is unavailable for gathering-only data sources such as Microsoft ISA Server logs and Microsoft Proxy Server logs.
To use agent-side log backup
- Select the data source under the gathering policy.
- Select Properties from the context menu, and select the Enable log backup and use it to gather events option on the General tab.
- Click OK to save your settings and close the dialog box.
- Commit the changes by clicking the Commit button in the InTrust toolbar.
|
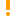
|
Caution: An agent-side log backup will be created if all of the following conditions are met:
- At least one gathering policy processing this log uses it with this option selected
- At least one task involving this policy has the task schedule enabled
- The gathering job in this task has the Use agents to execute this job on target computers checkbox selected.
|
To set the log backup retention period
- Select Configuration | Data Sources, and select the necessary data source.
- From its context menu, select Properties.
- On the General tab, specify the agent-side log backup retention period:
- Click OK to save your settings and close the dialog box.
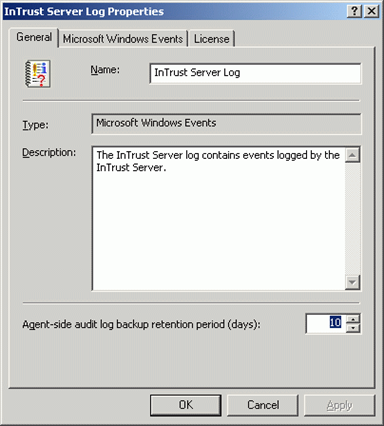
To change the location of agent log backup and temporary files
- From Configuration | InTrust Servers, select the InTrust server the the agent you need responds to.
- Expand the server node, and click Agents. The list of agents is displayed on the right.
- Right-click the required agent, and from its shortcut menu select Properties.
- On the General tab, specify agent temporary files location and agent log backup location you need.
|
|
Caution: These settings can be also specified for the whole list of agents responding to InTrust Server that InTrust Manager is connected to. Select all agents in the list, then right-click and select Properties. |
How to Gather User Session Data
You can collect user session data with InTrust from computers where InTrust agents are deployed. For a list of Windows versions supported by InTrust agents, see Microsoft Windows Events.
To configure gathering of event data with InTrust
- In InTrust Manager, select Configuration | Sites | Microsoft Windows Network, than select the All Windows servers in the domain site or some other site (such as All Windows workstations in the domain). Alternatively, create a new one.
- To automatically install agents on the site computers, clear the Prohibit automatic agent deployment on site computers option in the site's properties. For user session data, this is a requirement. Select Install Agents from the site’s context menu.
- Either select an existing task, or configure a new task as necessary, with a gathering job that involves the necessary gathering policy and site. The gathering policy must include the InTrust User Session Tracking data source.
|
IMPORTANT: The task that you use must have an active schedule. To prevent the task from actually running, you can set the schedule to a point in the past. |
- Configure a reporting job, if necessary.
How to Monitor for Critical Events
To monitor for critical events on Windows-based computers, InTrust agents are used on target sites. If the agents are not yet installed, they will be deployed automatically as soon as you activate a real-time monitoring policy.
To simplify the configuration of the real-time monitoring workflow, InTrust Knowledge Pack for Windows offers predefined monitoring rules and policies.
To configure monitoring for Windows events with InTrust
- In InTrust Manager, carry out the following:
- Enable the rule that will handle the events you need, for example, failed logons, or any other rule from Real-Time Monitoring | Rules | Windows/AD Security.
- Activate a monitoring policy that will bind this rule to your InTrust site, such as the Real-Time Monitoring | Policies | Windows/AD Security: Detecting Common Attacks policy, or any other policy you need.
- If you want to set notification upon alert generation, select the monitoring policy and from its context menu select Properties. Click E-mail or Net send tab to choose a notification method. Select Notify the following operators checkbox to specify recipients that will be notified. To add desired operators to the notification group in the Configuration | Personnel, select Notification Groups and add the recipient to a group.
|
|
Note: Make sure this notification method is also specified in the corresponding rule's properties. |
- Select the site you will monitor, and from its context menu, select Properties. Click Security, and make sure the list of accounts includes users you want to be able to work with the alerts (as alert readers or alert managers). Check the same for the rule group containing the rule you are using.
- In Monitoring Console, do the following:
- Open the profile you want to work with, or create a profile by running Monitoring Console Administration from the Start menu.
- Configure an alert view to display the necessary alerts.
For detailed information on configuring gathering and monitoring processes, refer to the Auditing Guide and Real-Time Monitoring Guide.
Gathering Windows DHCP Server Events
You can use InTrust to gather the following audit trails from Microsoft DHCP Server:
- Microsoft DHCP Server Audit log
- Windows System log (events generated by DHCP Server)
The DHCP server audit log stores information about events generated when IP addresses are assigned, revoked and so on.
|
|
Caution: The Microsoft DHCP Server Log data source type treats event times as local time. If you collect events for a period during which time was set back due to daylight saving time adjustments, the event times will be incorrect after the adjustment for the duration of the difference. |
To enable DHCP server logging
- Click Start | Settings | Control Panel, double-click Administrative Tools, and then double-click DHCP.
- In the console tree, click the applicable DHCP server. If working on a Windows 2008-based computer, select the applicable IP version.
- On the Action menu, click Properties.
- On the General tab, select Enable DHCP audit logging, and then click OK.
To collect data from Microsoft DHCP Server Audit Log
- Turn on DHCP server logging
- Use the Windows/AD: DHCP gathering policy provided with InTrust Knowledge Pack for Windows.
Rights and Permissions for Data Gathering Without Agent
The following is required to gather DHCP server audit data without agents:
- Access this computer from the network right. (Deny access to this computer from network right must be disabled.)
- Read permission to the HKLM\SYSTEM\CurrentControlSet\Services\ DHCPServer\Parameters registry key.
- Read permission to the HKLM\SYSTEM\CurrentControlSet\Control\ TimeZoneInformation registry key.
- Read permission to the HKLM\SYSTEM\CurrentControlSet\Control\Nls\Language registry key.
- Membership in the local Administrators group.
- Read and List Folder Contents permissions to log file folders; the Delete permission must also be granted if the Clear log files after gathering option is turned on for the data source.
Rights and Permissions for Data Gathering With Agent
The following is required to gather DHCP server audit data using agent:
- Read permission to the HKLM\SYSTEM\CurrentControlSet\Services\DHCPServer\Parameters registry key.
- Read permission to the SYSTEM\CurrentControlSet\Control\TimeZoneInformation registry key.
- Read and List Folder Contents permissions to log file folders; the Delete permission must also be granted if the Clear log files after gathering option is turned on for the data source.

