Quest On Demand uses the Role-based Access Control (RBAC) security policy that restricts information system access to authorized users. Your Quest On Demand organization comes configured with a number of default roles which cannot be changed, but subscribers can create custom roles with the permissions to perform needed operations on the assets of the organization.
If you are the On Demand administrator or the owner of the subscription, you can add users to an existing organization and assign the required roles. If you are not the subscription owner or administrator, contact your On Demand administrator for access.
When you add a user to an organization, you also assign one or more roles. The role assignment determines what permission level a user has and ultimately, what tasks the user can perform. Assigning roles and setting user permissions is referred to as access control. For more information, see Adding users to an organization in the On Demand Global Settings User Guide.
Access control is a process by which users are granted access and certain privileges to systems, resources, or information. In On Demand, you can grant authenticated users access to specific resources based on your company policies and the permission level assigned to the user.
|
|
NOTE: Every user must be assigned to at least one role. You cannot remove all roles from a user. For information about the various roles that can be assigned to users, see Users and Roles in the On Demand Global Settings User Guide. |
The Security Guardian Administrator role gives users full access to Security Guardian, as well as the following permissions for On Demand global settings:
- Export data
- Read access control roles
- Read Activity Trails
The following default roles are available to help you manage your security and compliance auditing:
- Security Guardian Audit Administrator role allows full access to Audit.
- Security Guardian Audit Operator role allows users to manage searches and create alerts.
- Manage Security Guardian Audit Organization Private Alerts and Private Alert Plans allows users to manage Audit alert plans
Quest® Security Guardian is an integrated On Demand solution that helps you keep the Active Directory domains and Entra ID tenants in your organization secure.
You can:
-
Identify Tier Zero objects in Active Directory.
-
Identify Privileged objects in Entra ID.
-
Certify that objects are indeed Tier Zero or Privileged and, when Quest Change Auditor version 7.4 is integrated, protect Active Directory Tier Zero objects against unauthorized or accidental modification or deletion.
-
Run pre-defined Security Assessments to identify vulnerabilities in Active Directory and Entra ID and create your own Assessments.
-
Investigate Findings for Tier Zero and Privileged objects, vulnerabilities identified through Assessments, and Critical Activity from Audit.
-
Have Findings forwarded to a SIEM tool and alerts sent to selected email recipients.
-
Lock down critical Active Directory objects, preventing unauthorized or accidental changes using Sheilds Up. This feature enforces a highly restrictive, pre-configured lockdown on Tier Zero objects—such as users, groups, computers, and policies. While intended for temporary emergency use, Shields Up can also be deployed continuously as a proactive security measure.
-
Audit and monitor critical activities and real-time alerts on important changes across Microsoft 365 services, including Exchange Online, SharePoint Online, Teams, OneDrive for Business, and Microsoft Entra.
-
Integrate with Quest Change Auditor to search and correlate identities across both on premises and in the cloud to give a seamless view of activity in hybrid Microsoft environments. Specifically auditing enables:
- Fast and flexible searches for easy investigation and accurate results across tenants and on premises environments
- Interactive visualizations and dashboards to summarize audit activity
- Easy to use customizable alerts based on audit event searches
- Long term storage of audit events outside of Microsoft 365 and Change Auditor for a retention period of up to 10 years
-
Review service principals and their associated security posture within your Entra ID environment to identify risky permissions, assess sign-in status, and monitor compliance with security .
-
Monitor and analyze activity across both your on-premises and cloud-based Microsoft environments from a single, unified interface using Hybrid Audit.
-
Use Security Guardian Intelligence AI assistance to:
-
Help you ask focused questions tailored to your environment.
-
Gain valuable insights into the security posture of your organization’s Active Directory and Entra ID systems.
-
View critical vulnerabilities and issues identified during assessments and offers practical recommendations for remediation.
The diagrams below illustrate how Security Guardian functions for both Active Directory and Entra ID, including how additional components are integrated.
Functional Overview for Active Directory
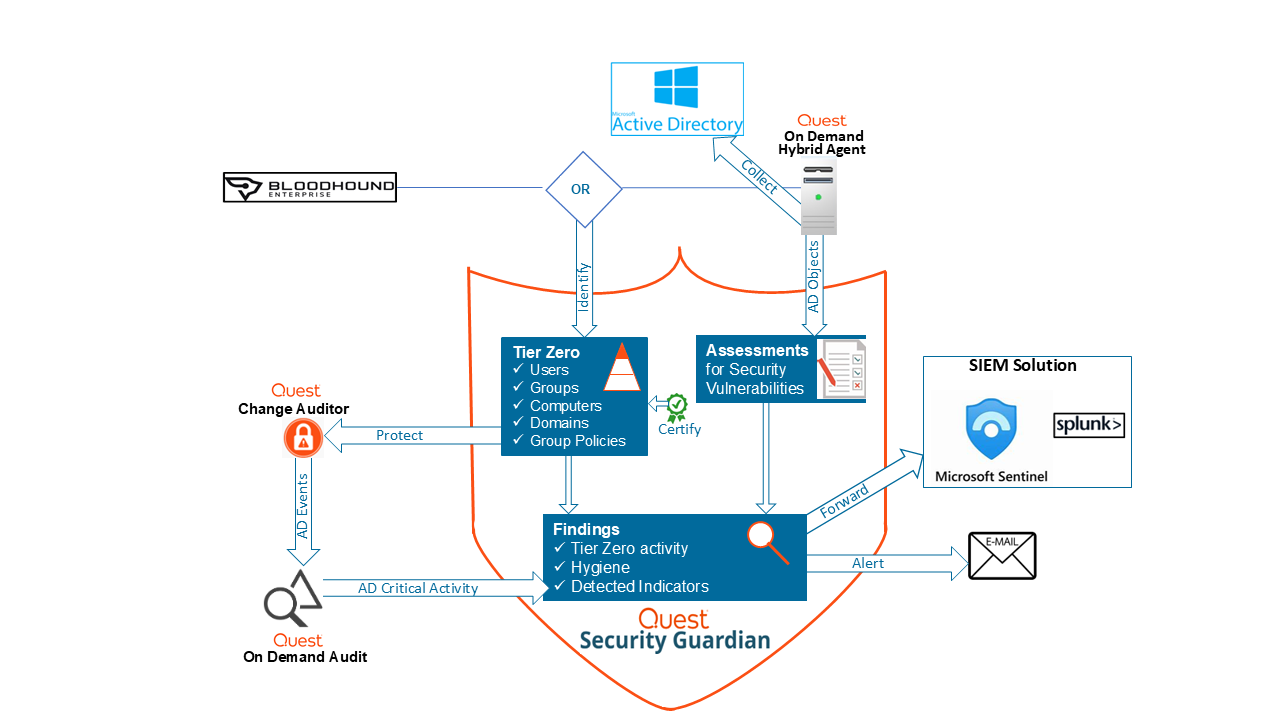 .
.
Functional Overview for Entra ID
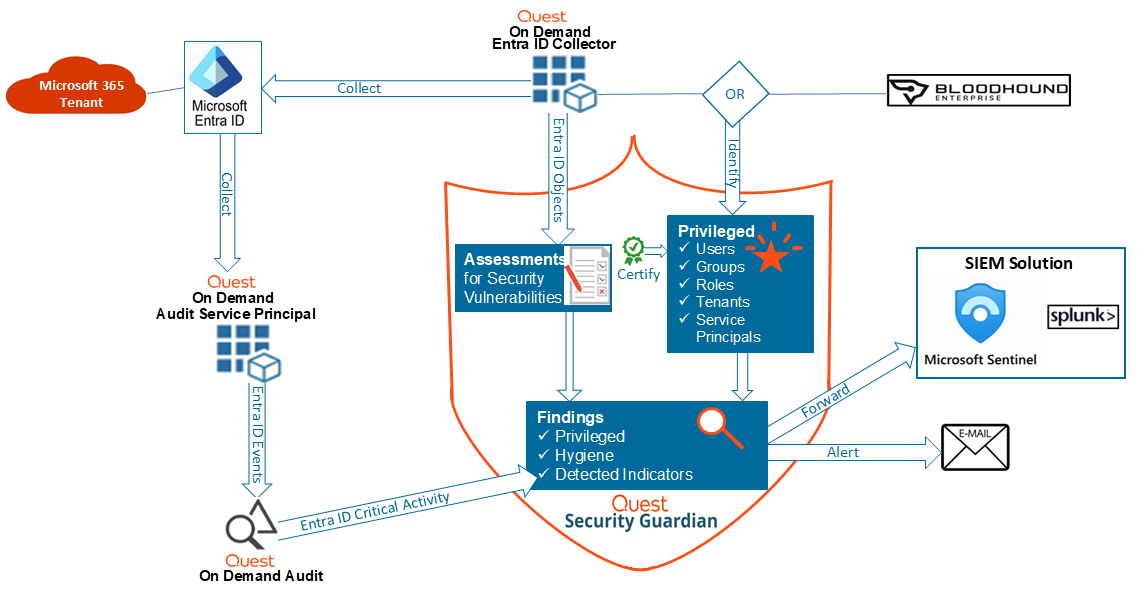
Additional components need to be configured to make Security Guardian fully functional.
To configure additional components:
-
From the On Demand left navigation menu, choose Security | Dashboard.
-
From the Configuration Status tile, configure the necessary components.
|
|
NOTE: Once an additional component is configured in On Demand, it's available to any other module that uses it. |
| Hybrid Agent |
Gives Security Guardian access to the Active Directory domains that you want to keep secure. |
On Demand Global Settings User Guide - Managing your on-premises domains
When configuring the agent, ensure that:
- the action Collect Active Directory object data is selected
- any domain for which you want object data to be collected is added.
|
|
NOTES:
-
The Collect Active Directory object data action uses Lightweight Directory Access Protocol (LDAP) by default. However, it will use Secure LDAP (LDAPS) if your environment is configured for it. Refer to the topic Secure LDAP Configuration and Deployment in the On Demand Global Settings user guide for details.
-
In addition to the permissions required for the hybrid agent, the service account (which the Collect Active Directory object data action uses) requires an additional permission to assess certain vulnerabilities.
-
The Manage Security Guardian Hybrid Audit action enables the Hybrid Audit Broker process on the Hybrid Agent. See Working with Hybrid Audit Brokers.
-
The Broker footprint:
-
Estimated disk-space for installation: 500MB + Log files.
-
Log files: By default, Broker related processes retain up to 10 log files (1MB each): 20MB.
-
Estimated disk-space for event storage: Up to 100,000 event batches waiting (max batch size is 1MB), 100GB space used or until 5% available free space on the drive where the Broker is installed. | |
| Hybrid Audit Agent |
Sends Active Directory events to Audit for reporting in Security Guardian Findings and allows you to protect Tier Zero objects. |
System requirements can be found in Change Auditor agent release notes.
For installation details see, Hybrid Audit Agent Deployment. |
| Entra ID Data Collector |
A Service Principal that gives Security Guardian access to Entra ID objects in the tenants that you want to keep secure. |
On Demand Global Settings:
When configuring the tenant, ensure that
Core | Collectors consent is granted to each tenant for which you want Entra ID object data to be collected.
|
|
NOTE: An additional consent, Audit | Basic is needed for the On Demand - Audit Entra ID Service Principal to collect Critical Activity, which contributes to Detected Indicator findings in Security Guardian. | |
|
Quest Change Auditor |
Sends Active Directory events to On Demand for reporting in Security Guardian Findings and allows you to protect Tier Zero objects.
|
|
NOTE: A minimum of version 7.3 is required to send critical activity events to On Demand, and a minimum of version 7.4 is required to protect Tier Zero objects. |
|
See Change Auditor Integration.
|
|
SpecterOps BloodHound Enterprise
(Optional) |
Identifies Tier Zero assets in your organization's Active Directory domain(s) and Privileged assets in your Entra ID tenant(s), which you can monitor and assess for security vulnerabilities in Security Guardian.
|
|
NOTE: If BloodHound Enterprise is not configured, Security Guardian will be used as your organization's provider. | |
See SpecterOps BloodHound Enterprise Integration. |
|
SIEM solution:
(Optional) |
Allows Security Guardian Findings to be forwarded to a configured SIEM tool for further analysis.
|
|
NOTE: Regardless of whether your organization uses a SIEM solution, you can also have Finding alerts sent via email. | |
Configuring a Forwarding Destination |


 .
.