TPAM Auditing Overview
In enterprises Quest Total Privileged Access Management (TPAM) appliance controls privileged identity management and privileged access control in order to meet highest compliance and security requirements. Providing comprehensive auditing of privileged user activity across all of the systems managed by TPAM is vital for raising individual accountability and achieving compliance goals set by external regulations and internal security policy requirements. InTrust complements TPAM auditing capabilities by collecting logs produced by TPAM and correlating them with other native logs residing on Windows and Unix/Linux systems.
InTrust can help you track sys-admin and user activity recorded by TPAM, password and session requests from TPAM users, and also monitor TPAM appliance state. This is enabled through configuring InTrust to collect TPAM logs transmitted to a Syslog server.
To integrate InTrust with TPAM, use the InTrust Knowledge Pack for TPAM that is provided.
Benefits of Using InTrust
When integrated with TPAM, InTrust brings new, powerful means of automating and streamlining your auditing workflow:
- Long-term data storage, archival, and backup. With InTrust, you can use file-based or Centera-based repositories to store TPAM logs in a compressed form for any period of time; extract events from the repository for on-going reporting needs. These features help organizations comply with external regulations and internal policies.
- Exploration and representation of TPAM logs in InTrust Repository Viewer with the following benefits:
- Quick and interactive full-text search
- Fields detection and field-based search
- Grouping, sorting and charting of information
- Consolidation of various log sources to allow comprehensive analysis of privileged users activity, such as:
- Logon events from Windows DCs and logon session events from Windows workstations
- Events from native logs residing on UNIX/Linux hosts managed by TPAM
- Changes to Active Directory, File Systems, Exchange objects and other infrastructure components and IT data captured by the Change Auditor family of products
The following figure shows how TPAM and related systems work together.
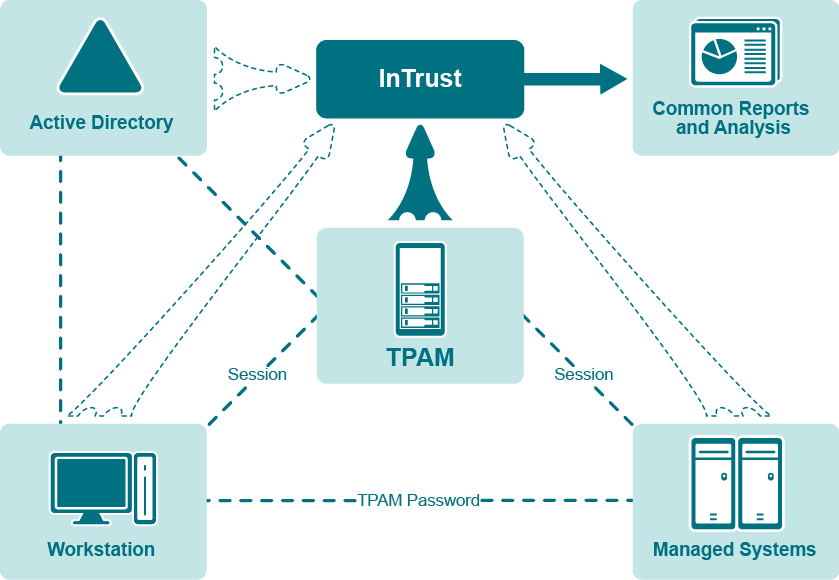
Note that in addition to collecting TPAM logs, InTrust can also collect logs from related systems, such as hosts managed by TPAM, workstations from which users connect to TPAM and Active Directory domain controllers where TPAM users reside. For more information about that, refer to the corresponding InTrust documentation.
How Integration Works
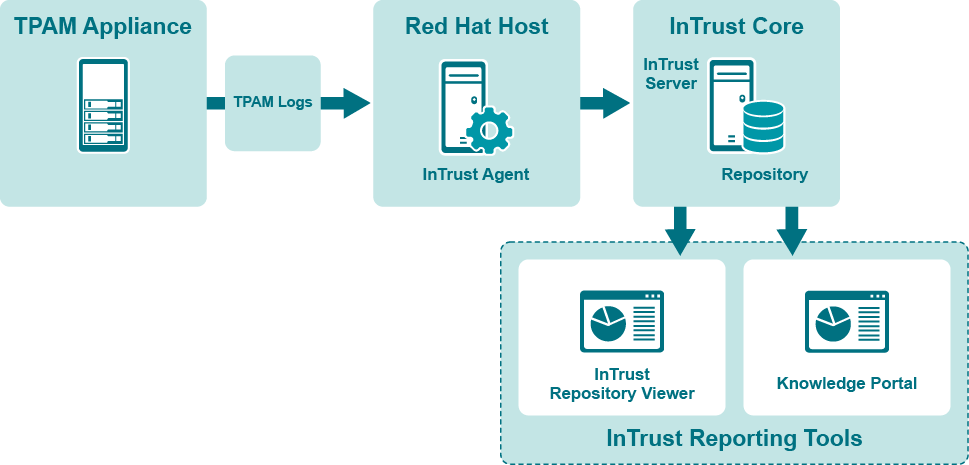
Communication between the components takes place as follows:
- TPAM logs such as user and sys-admin activity are forwarded to a Red Hat or Oracle Linux host with installed InTrust agent acting as a Syslog listener.
- Then logs are parsed on InTrust side and put into the InTrust repository.
- TPAM events in InTrust Repository are normalized into a common representation not requiring expert knowledge of events.
- As a result, data from TPAM can be tracked using one of the following:
- Repository Viewer (for ad-hoc searches and forensic analysis)
- Quest Knowledge Portal (for interactive and schedule based reporting)
This scenario is shown in the following diagram.
Getting Started
- Step 1. Install InTrust with TPAM Knowledge Pack
- Step 2. Configure TPAM Log Forwarding
- Step 3. Allow Syslog Reception on Linux Host
- Step 4. Install the Agent
- Step 5. Establish a Connection with InTrust Server
- Step 6. Add Agent to Site on InTrust Server
- Step 7. Enable Schedule for Daily Collection Task
- Step 8. Run Daily Collection Task

