How to Gather Event Data with InTrust
IIS logs can be collected with or without agents. For successful gathering, make sure the system requirements are met, as described in Microsoft IIS Events.
To gather IIS log data
- In InTrust Manager, select Configuration | Sites | Microsoft Windows Network, and make sure the All IIS Servers site includes your IIS servers.
- To automatically install agents on the site computers, select Install Agents from the site’s shortcut menu.
- Select the IIS Daily Collection task, or configure a new task as needed, with a gathering job associated with the correct gathering policy and site. In the task properties, select the Schedule enabled option.
- Select the IIS Weekly Reporting task, or configure a new reporting task as needed, and enable its schedule in the similar way.
|
|
Caution: If you change the location of IIS log files between gathering sessions, make sure the old log files are available in the new location. |
IP Address Resolution
If specified by InTrust settings, IP addresses found in the log are resolved to host names, and InTrust saves them both (IP addresses and host names) into the log, appending them to original fields. This can significantly slow down the gathering process; so this option is disabled by default. If necessary, you can enable this option in the following way:
- In InTrust Manager, select Configuration | Data Sources.
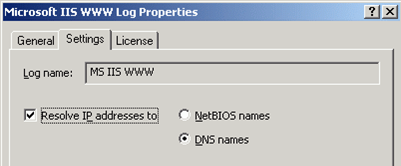
- On the right pane, select the IIS log you need, for example, Microsoft IIS WWW Log
- From its shortcut menu, select Properties, on the Settings tab select Resolve IP addresses to and specify whether to resolve them into NetBIOS names or DNS names:
How to Monitor for Critical Events
To monitor for critical events, InTrust agents are used on the computers included in the target site. If the agents are not yet installed, they will be deployed automatically as soon as you activate a real-time monitoring policy.
To simplify the configuration of the real-time monitoring workflow, InTrust Knowledge Pack for Microsoft IIS offers predefined monitoring rules and policies.
|
IMPORTANT: For real-time monitoring to work on 64-bit Windows, IIS must be running in 32-bit mode. |
To configure IIS monitoring with InTrust
- In InTrust Manager, carry out the following:
- Enable the rule that will handle the events you need, for example, 'Unauthorized web-page access attempt', or any other rule from Real-Time Monitoring | Rules | IIS RTM Rules | Common Attacks.
- Activate a monitoring policy that will bind this rule to your InTrust site, that is the Real-Time Monitoring | Policies | IIS Security policy.
- If you want to get an email notification upon alert generation, in the Configuration | Personnel, select Notification Groups, select the necessary group and specify the desired recipients.
- Select the site you will monitor (All IIS Servers), and from its shortcut menu, select Properties. Click Security, and make sure the list of accounts includes users you want to be able to work with the alerts (as alert readers or alert managers). Check the same for the rule group containing the rule you are using.
- In Monitoring Console, do the following:
- Open the profile you want to work with, or create a profile by running Monitoring Console Administration from the Start menu.
- Configure an alert view to display the necessary alerts.
For detailed information on configuring gathering and monitoring processes, refer to the Auditing Guide and Real-Time Monitoring Guide.
InTrust Knowledge Pack for Microsoft IIS
The Knowledge Pack for Microsoft IIS offers a set of predefined InTrust objects that will help you configure the gathering and monitoring of event data from your IIS servers. The following objects are included:
- Gathering policies:
- IIS: Security
Collects all IIS security events to both a repository and a database.
- IIS: Health
Collects all IIS health events both to a repository and a database.
- IIS: Usage: WWW
Collects IIS Web Site log both to a repository and a database.
- IIS: Usage: FTP
Сollects IIS FTP Site log both to a repository and a database.
- Import policies:
- IIS: Security
Imports all IIS security events to a database.
- IIS: Health
Imports all IIS health events to a database.
- IIS: Usage: WWW
Imports events from IIS Web Site log to a database.
- IIS: Usage: FTP
Imports events from IIS FTP Site log to a database.
- Jobs:
- IIS Security events collection
Collection of all the IIS security events to the default repository and the default database.
- IIS Web Site Reporting
Weekly reporting of IIS Web Site usage and security events.
- IIS FTP Reporting
Weekly reporting of IIS FTP Site usage and security events.
- Tasks:
- IIS Daily collection
Daily collection of all the IIS events to the default repository and the default database.
- IIS Weekly Reporting
Weekly reporting of IIS statistics and the most critical events.
- “All IIS servers” site
- “IIS Security” real-time monitoring policy
Applies real-time monitoring rules related to IIS security.
