Introducing Quest GPOADmin
Configuring GPOADmin
Configuring the Version Control server
Setting permissions on AD LDS
Setting permissions when using SQL as the configuration store
Port requirements
Editing the Version Control server properties
Editing the Version Control server configuration store
Replacing the Version Control server configuration settings
Migrating from AD/AD LDS to a SQL configuration store
Changing the Service Account
Root container assignment
Restricting GPO management for specific domains
Configuring role-based delegation
Restricting access to objects
Adding notifications for users
Selecting events on which to be notified
Restricting inheritance on notifications
Creating email templates
Working with Protected Settings policies
Using GPOADmin
Rights and role for Protected Settings for GPOs
Create a Protected Settings policy
Protecting policy settings based on extensions
Generating Protected Settings policies reports
Using Protected Settings policies
Checking a GPO against a Protected Settings policies and blocked extensions
Validating a GPO against a Protected Settings policies and blocked extensions before a check-in
Connecting to the Version Control system
Navigating the GPOADmin console
Search folders
Accessing the GPMC extension
Configuring user preferences
Working with the live environment
Working with controlled objects (version control root)
Creating Reports
Creating a custom container hierarchy
Selecting security, levels of approval, and notification options
Viewing the differences between objects
Copying/pasting objects
Proposing the creation of controlled objects
Checking compliance
Editing objects
Creating Group Policy Objects (GPOs)
Creating starter GPOs
Creating WMI filters
Creating scripts
Creating Desired State Configuration (DSC) PowerShell scripts
Merging GPOs
Restoring an object to a previous version
Restoring links to a previous version
Managing your links with search and replace
Linking GPOs to multiple Scopes of Management
Managing compliance issues automatically with remediation rules
Validating GPOs
Managing GPO revisions with lineage
Setting when users can modify objects
Working with registered objects
Creating labels
Cloaking a GPO
Locking a GPO
Establishing Management for an Object
Viewing history
Deleting version history
Clearing account names in version history
Viewing and editing object properties
Applying keywords on containers
Creating a report
Working with available objects
Enabling/disabling workflow
Checking out objects
Requesting the deletion of an object
Unregistering GPOs and removing history
Requesting approval
Working with checked out objects
Working with objects pending approval and deployment
Editing GPOs
Editing Intune objects (configuration profiles and compliance policies)
Editing WMI filters
Editing scripts
Linking GPOs
Synchronizing GPOs
Exporting and importing
Available reports
Appendix: Windows PowerShell Commands
Controlled object reports
Creating RSoP validation reports
Exporting registry settings
Working with report folders
Settings Report
Difference Report
Group Policy Comparison Report
History Report
Group Policy Object Settings Search Report
User Activity Report
Role Assignment Report
All Actions Report
Compliance Report
Change Auditor Report
Change Auditor Working Copies Report
Deployment Report
Protected Settings Assignment Report
Creating Controlled Object Reports
Diagnostic and troubleshooting reports
Group Policy Object Consistency Report
Software Installation Package Report
Linked/Unlinked Report
Linked/Unlinked SOMs Report
Inactive Policy Settings Report
Group Policy Object Security Report
Policy Analysis Report
GPO Synchronization Report
Group Policy Results
Group Policy Results Difference Report
Group Policy Modeling Report
Creating Diagnostic and Troubleshooting Reports
Live, working copy, latest version, and differences reports
Historical Settings Reports
Introduction
GPOADmin scripts
Available commands
Using the GPOADmin PowerShell commands (Examples)
Appendix: GPOADmin Event Log
Appendix: GPOADmin Backup and Recovery Procedures
Appendix: Customizing your workflow
Loading the GPOADmin modules
Extracting help for GPOADmin commands
Managing objects
Get information on all GPOs
Get information for all managed objects
Get unregistered objects
Register an object
Check out an object
Check in an object
Undo the check out of an object
Request approval for changes
Withdraw an approval request
Approve changes
Reject changes
Withdraw approval on an object
Deploy an object
Deploy an object at a future time and date
Check for pending deployments
Cancel pending deployment
Gathering object and GPOADmin information
Identify which objects are checked out
Identify which objects are checked out to me
What are the properties of an object
What objects are available
What objects are checked out
Utility commands
Gather GPOADmin license information
Install a GPOADmin license
Get logging options
Set logging options
Get notifications
Set notifications on objects
Administrative commands
Approval workflow information
Set the approval workflow
Identify user accounts
Identify user roles
Modify a role
Add a role
Get an object's security
Set an object's security
Overwrite a GPOs security filter
Protected Settings commands
What is a custom workflow action?
Working with custom workflow actions in the Version Control system
Working with the custom workflow actions xml file
Troubleshooting custom workflow actions
Appendix: GPOADmin Silent Installation Commands
Installing GPOADmin with msiexec.exe
Appendix: Configuring Gmail for Notifications
Appendix: Registering GPOADmin for Office 365 Exchange Online
Appendix: GPOADmin with SQL Replication
About Us
All components (Complete GPOADmin installation)
Client and components
Server and client
Client only
Client and PowerShell provider (Client Only button on Installation dialog)
PowerShell provider only
Watcher Service
Watcher Service on localhost
Watcher Service on another computer
Watcher Service and GPMC Extension on another computer
Watcher Service and Client only on another computer
Watcher Service, Client, and GPMC Extension on another computer
GPMC Extension
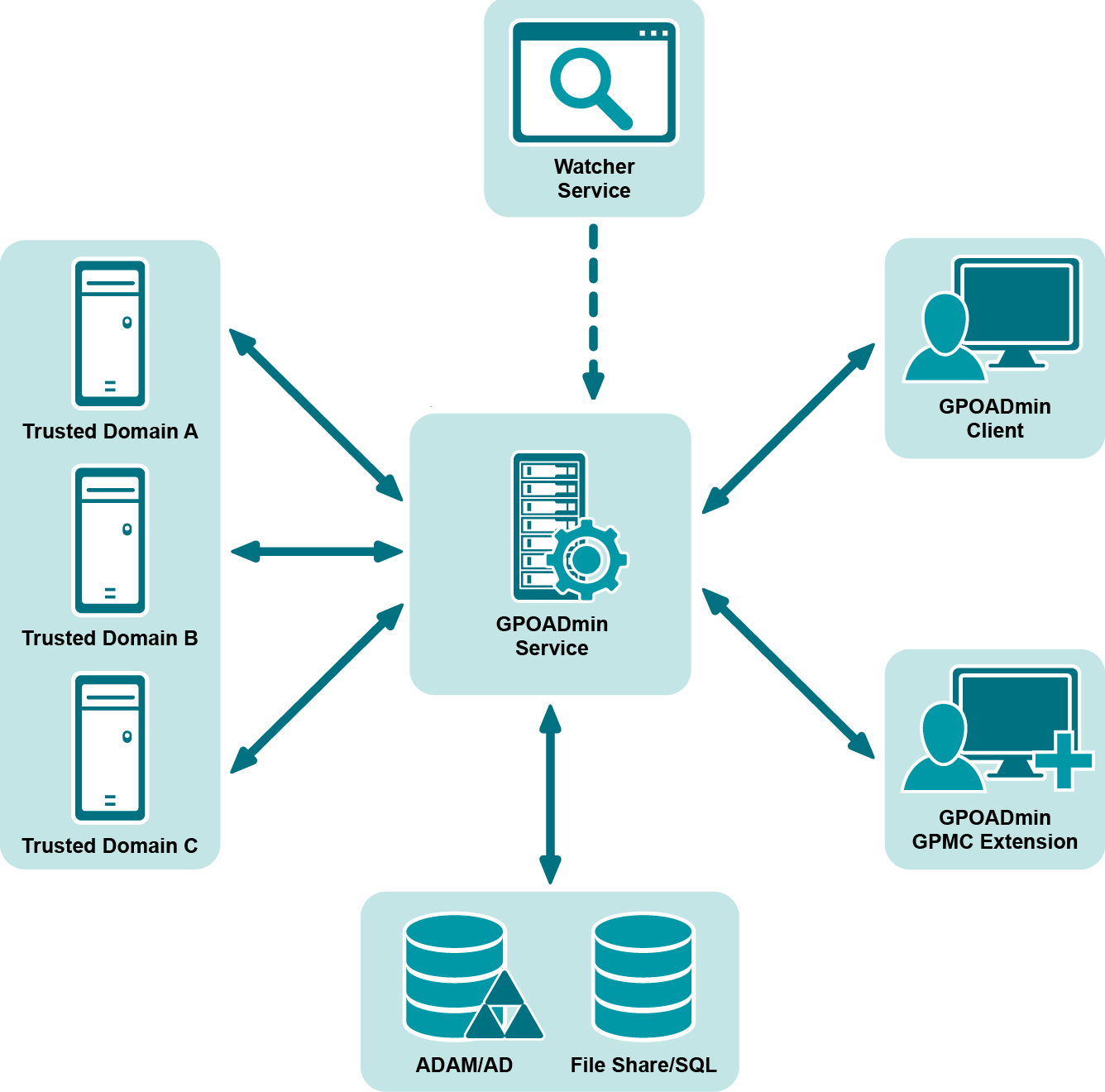
Introducing Quest GPOADmin
GPOADmin features
Figure 1. Group Policy Workflow
Client/server architecture
Multiforest support
- セルフ・サービス・ツール
- ナレッジベース
- 通知および警告
- 製品別サポート
- ソフトウェアのダウンロード
- 技術文書
- ユーザーフォーラム
- ビデオチュートリアル
- RSSフィード