Accessing and configuring the virtual machine
|
NOTE: If you recently created the virtual machine, it is recommended that you wait 3 or 4 minutes before you begin this procedure. |
|
1 |
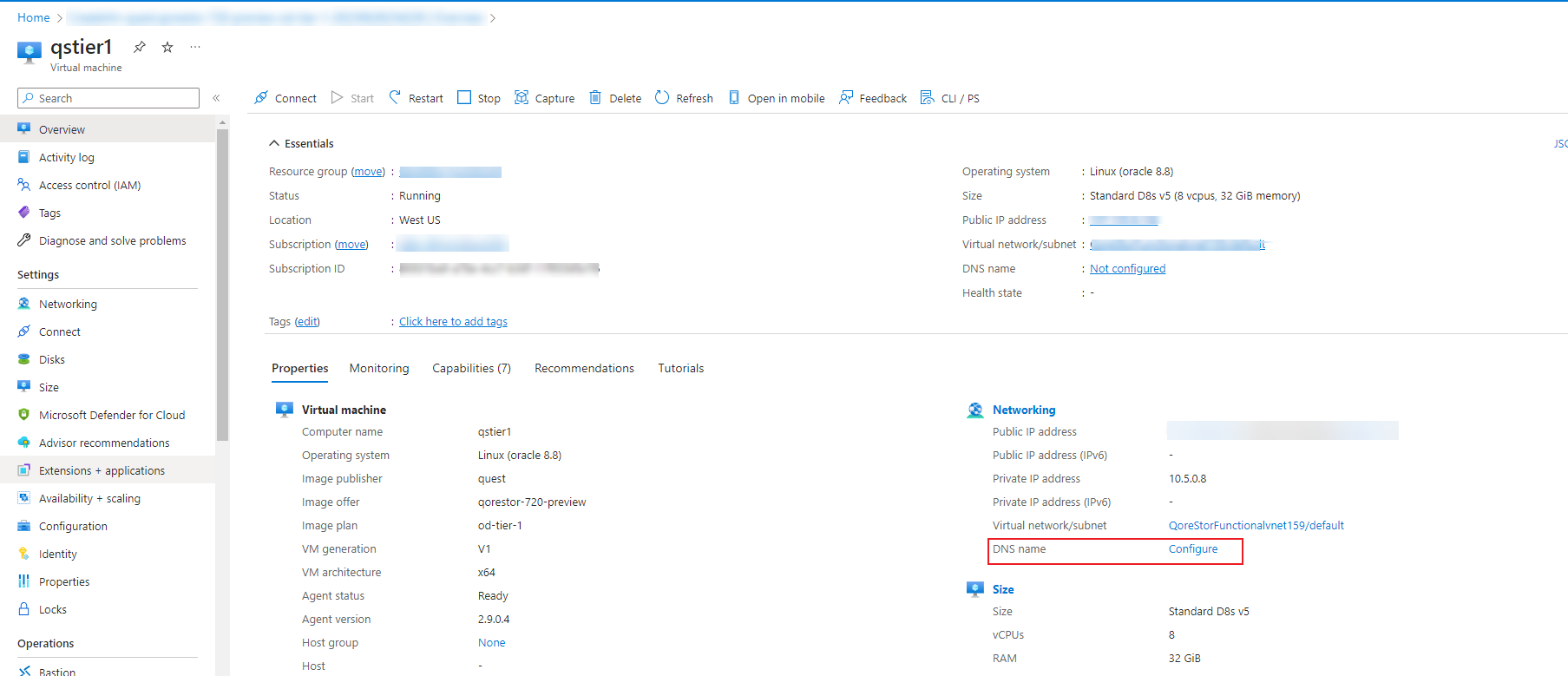
By default, the instance does not have the DNS name configured. To configure the DNS name, find the DNS name field in the Networking section, and then click Configure. |
|
2 |
By default, Azure provides the <region>.cloudapp.azure.com domain. Edit the options for the name based on your Public IP configuration, and then click Save. |
|
5 |
After you log in, verify the filesystem is operational for I/O using the system --show command. Check if "System State," is in "Operational Mode". |
|
NOTE: The system prompts you for the connection string in secret. |
|
7 |
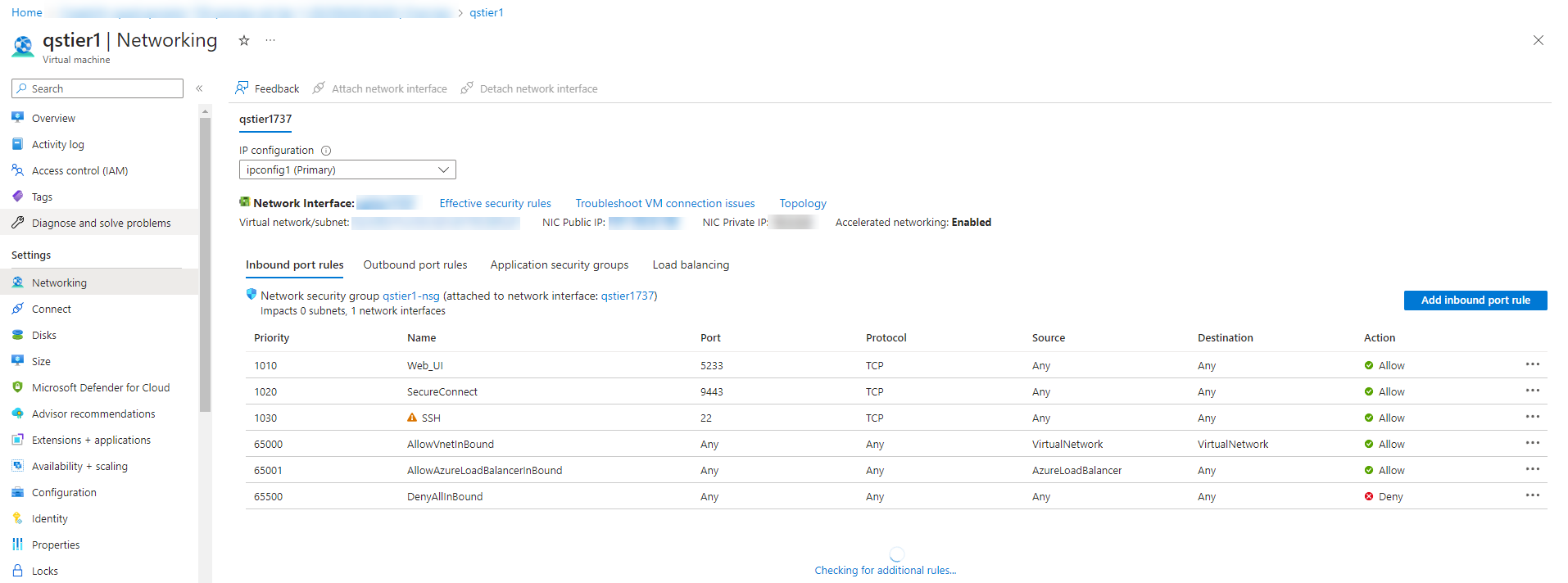
To access the QoreStor UI, use the public IP assigned in the section Creating the virtual machine. The URL for accessing QoreStor UI would be https://<public_ip_of_virutal_machine>:5233. |
Port usage
Configuring Azure Network Security Group settings
|
1 |
In the Azure console, find “Services” and click Network Security Groups. |
|
NOTE: Any modification to this NSG will change the default settings recommended by QoreStor. |
|
4 |
When opening an additional port, to add inbound rules for that specific port, click Inbound security rules on the left side, and then click the Add tab on the top side of the page. |
|
Select an IP or an Azure NSG. If the port can be used from any external interface, select Any. | |
|
Select a port range on the specified source. To select any range, select *. | |
|
Leave as the default selection, Custom. | |
|
(Required) Enter 9001-9005 for this port. | |
|
Select TCP. | |
|
Select Allow. | |
|
6 |
Click Add. |