| NOTE |
For Recovery Manager for Active Directory 10.1 or higher: Make sure that you use the Backup Agent version supplied with this release of Recovery Manager for Active Directory. |
Recovery Manager for Active Directory employs a Backup Agent to back up remote domain controllers and AD LDS (ADAM) hosts. This is because some backup APIs provided by the operating system cannot be used to access a target domain controller or AD LDS (ADAM) host from the Recovery Manager Console. Therefore, Backup Agent must be installed on a remote domain controller or AD LDS (ADAM) host in order to gain access to its specific objects. RMAD can automatically install Backup Agent before starting a backup, and remove it upon the completion of backup operation. Alternatively, you can preinstall Backup Agent manually. For more information on the advantages of using preinstalled Backup Agent, see Using preinstalled Backup Agent below.
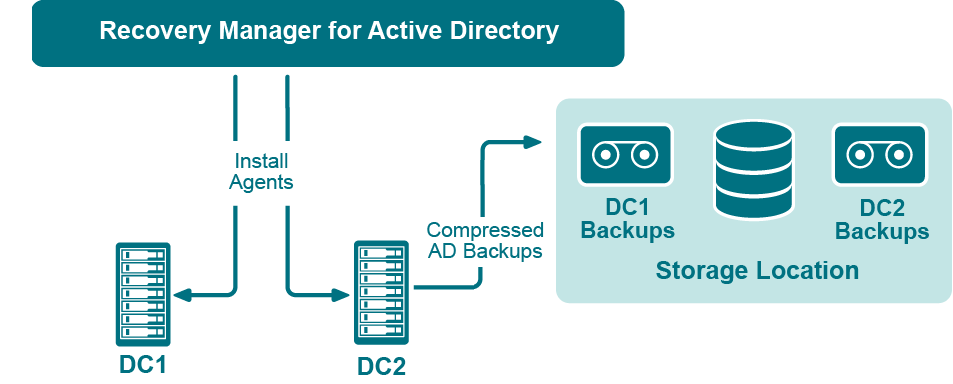
The Recovery Manager for Active Directory (RMAD) employs a Backup Agent when creating backups. The Backup Agent is installed on domain controllers DC1 and DC2 and compresses the data and transfers the compressed data to storage location.
Since Backup Agent compresses the data before sending it over the network, the network load is decreased significantly. The average compression ratio is 7:1. The use of Backup Agent also provides increased scalability and performance by allowing the creation of backups on multiple domain controllers in parallel.
RMAD allows to run Backup Agent in the security context of a specific user account. Since RMAD needs administrative access to the domain controller in order to run Backup Agent, the account under which RMAD is running must belong to the Administrators group on that domain controller or AD LDS (ADAM) host, providing administrative access to the entire domain. If RMAD cannot be started under such an account, separate credentials (user logon name and password) should be specified, so that Backup Agent is run under an account that has sufficient privileges.
RMAD allows you to back up Computer Collections using Backup Agent manually preinstalled on each target domain controller. This method enables you to
Perform a backup operation without having domain administrator privileges. It is sufficient if RMAD runs under a backup operator's credentials.
Reduce network traffic when backing up the Computer Collection.
Back up domain controllers in domains that have no trust relationships established with the domain in which RMAD is running, solving the so-called “no trust” problem.
| NOTE |
For Recovery Manager for Active Directory 10.3 or higher, the option to Use preinstalled Backup Agent is selected by default for all new computer collections. |
Recovery Manager for Active Directory (RMAD) enables the recovery of a portion of the directory or the entire directory, in the event of corruption or inadvertent modification. The granular, object-level, online restore may also be used to undelete directory objects. These powerful, security-sensitive functions of RMAD should only be performed by highly trusted directory administrators.
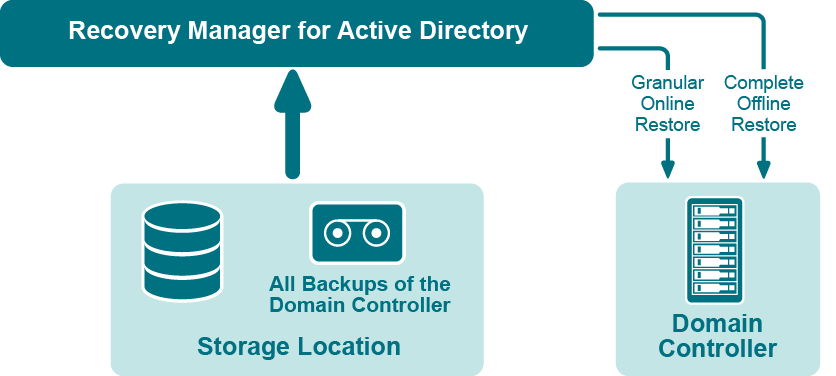
If certain objects are inadvertently deleted or modified in Active Directory, they can be restored from a backup of domain controller’s Active Directory® components, without restarting the domain controller or affecting other objects. If the Active Directory® database on a particular domain controller has been corrupted, the entire database can be restored from a Active Directory® backup created for that domain controller. All the restore operations are administered remotely.
Recovery Manager for Active Directory offers the following restore methods:
Granular online restore. Allows you to select Active Directory® objects from a backup, and then restore them to Active Directory®. This method allows for the recovery of individual Active Directory® objects, and selected attribute values in Active Directory® objects, with the least amount of administrative effort.
Complete offline restore. Restarts the target domain controller in Directory Services Restore mode, restores the Active Directory® database from the selected backup, and then restarts the domain controller in normal operational mode. This method enables the recovery of the entire Active Directory® database on a domain controller, and is most useful when recovering from database corruption.
Recovery Manager for Active Directory supports granular online restore from BMR backups.
Recovery Manager for Active Directory (RMAD) enables the recovery of Group Policy data from corruption or inadvertent modification, which can be caused by either hardware failure or human error.
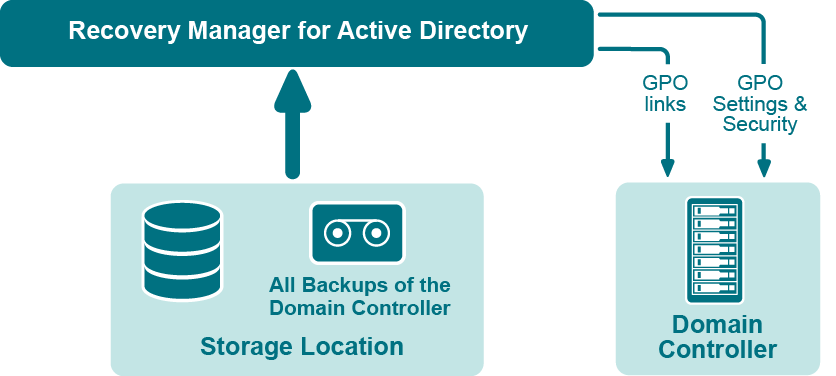
If specific Group Policy objects or links are inadvertently deleted or modified, they can be restored from a backup of a domain controller’s Active Directory® components, without restoring the entire Active Directory®, restarting the domain controller, or affecting other objects.
Recovery Manager for Active Directory includes the following options for Group Policy recovery:
Policy settings restore. If the Group Policy object was modified since the backup was created, this option restores all policy settings to the state they were in at the time of the backup. If the Group Policy object was deleted, this option creates a new object with the same name and policy settings as the backed-up object.
Security settings restore. Restores all security information contained in the Group Policy object. As a result, all users and security groups receive the access permissions that were specified in the Group Policy object at the time it was backed up.
GPO links restore. Restores all links associated with the Group Policy object to the state they were in at the time the backup was created. As a result, the object is once again used by the same sites, domains, and organizational units that were linked to it at the time the backup was created.
Comparison reports. Shows whether Group Policy object was deleted or modified since the backup time.
You can use any combination of these options. For example, suppose some links to a Group Policy object are accidentally deleted. If your backup contains an outdated version of the Group Policy object, you can restore only the links, without restoring the policy settings or security settings.
To eliminate downtime when recovering Group Policy, RMAD provides the Group Policy Restore method. This method allows individual Group Policy objects to be restored to a selected domain controller. The operation can be performed on any domain controller that can be accessed remotely. Using this method, domain controllers do not need to be restarted, and only those objects selected for recovery are affected.
For this type of restore, it is not necessary to create any special backups; you may use any regular backup of domain controller’s Active Directory® components.
A Group Policy Restore is particularly helpful when critical Group Policy objects or links have been inadvertently deleted or changed. To recover from such situations, you may carry out a Group Policy Restore to a domain controller using a Active Directory® backup that was created before the objects in question were deleted or modified.
Group Policy Restore allows you to roll back changes made to Group Policy information, and return individual Group Policy objects to the state they were in when the backup was created. It is important to note that a Group Policy Restore only affects the object selected for recovery, and optionally, the links to that object. Any objects that are not involved in the operation remain unchanged in the domain.
Recovery Manager for Active Directory (RMAD) provides comparison reports to assist with isolating deletion or changes to Active Directory® or AD LDS (ADAM), and troubleshooting the resulting problems. These reports are based on per-attribute comparisons of Active Directory®, AD LDS (ADAM), or Group Policy objects selected from a backup, with their counterparts in Active Directory®, AD LDS (ADAM), or another backup.
By comparing the state of the directory objects or Group Policy objects in Active Directory® with those in a backup, comparison reports improve the efficiency of recovering objects, by allowing you to specify precisely which objects should be restored.
By showing the changes that would be made to Active Directory® or AD LDS (ADAM) during a restore operation, comparison reports help to highlight possible side effects that could result from restoring data. If such side effects are indicated in the report, you may then reconsider whether to apply the changes to the “live” directory data.
Comparison reports may also be used to monitor changes that occurred in Active Directory or AD LDS (ADAM) since the backup was created, or within the period between two backups. Comparison reports assist with troubleshooting Active Directory®, and resolving problems that may result from the deletion of critical objects in Active Directory®. The reports also help you monitor changes made to Active Directory® or AD LDS (ADAM) by third party applications.
The ability to compare the current state of objects in Active Directory® or AD LDS (ADAM) with their state in a backup helps when troubleshooting problems that may result from the deletion or modification of a user account or an Organizational Unit, or modification of more critical objects. Comparison reports show whether critical objects were deleted or modified since a backup was made.
The deletion of critical objects such as a domain controller’s computer account or the "NTDS Settings" object is one of the most common causes of Active Directory® problems.
Other critical, equally sensitive objects include all objects in the System container, such as FRS subscription objects, trusted domain objects (TDO), and DNS objects. By comparing the current state of objects in the System container with the state of the objects in a backup, it is possible to isolate problems that result from the absence or incorrect modification of critical objects.
RMAD serves as a valuable tool when implementing a change management process. The importance of testing changes to Active Directory® is paramount, whether you are changing configurations, installing new software, or implementing service packs and patches. The product has the ability to report changes, and if necessary, roll back changes made to Active Directory®. This improves the effectiveness of testing application deployment scenarios in a laboratory environment, and monitoring changes made to Active Directory® by third-party applications.