Logging
The Logging object maintains log files used to track information about users logging onto the network and the computer they are logging on from. Several customized fields of information may be stored in the log file. The first 17 fields are automatically configured by default. They may be changed, deleted, or added to, to meet specific needs.
Log files are Comma Separated Value (.CSV) formatted files. These files may be viewed by clicking View Logs. These files may also be viewed in any text editor, including notepad.
Log files use the profile name and current date for its file naming convention. The file name is in the format of ProfileName_YYYYMMDD.CSV and is stored in the LOGS$ share, by default. A single log file is created once per day per profile and contains all logon information for the day and profile.
Log file location
Path
Enter the location where the log files will be created or press Browse to select a folder. The location may be specified in the form of a path, mapped drive or UNC. Dynamic variables may be used as an aid in defining the location. Press F2 to select a dynamic variable from the popup list.
If specifying a UNC, the location should be specified in the form of \\server\share\. Typically, the log file folder is a shared folder and is stored on a Domain Controller.
The default share name (unless modified during the install) is set to LOGS$.
Example:
\\pdcserver\LOGS$$ use LOGS$ share on pdcserver
To disable logging, clear the specified Path.
Variable list
Log file list
Log files can be configured with several fields of customized information. Log file elements within the list are processed in the order that they appear in the list.
Click Add to add a new element to the list. This will add the new element to the end of the list.
Click the Edit link to edit the existing highlighted element in the list. Enter static text into the variable field, select a variable from the drop down list and/or press F2 or the Insert dynamic variable link to use insert a dynamic variable.
Copy will duplicate the selected element. You are given the opportunity to modify the settings at the time of the copy.
Click Delete to remove the highlighted element from the list.
Use Move Up and Move Down to reorder the elements in the list by moving the selected element up or down.
The following variables are defaults in new profiles:
|
Variable |
Description |
|
$Date |
Current date |
|
$Time |
Current time |
|
$LogonServer |
Authenticating Domain Controller |
|
$ConnType |
Connection method |
|
$WrkSta |
Computer Name |
|
$SiComputerType |
Computer Type |
|
$IPaddr |
TCP/IP address |
|
$SiCpuType |
CPU Type |
|
$SiCpuSpeed |
CPU Speed |
|
$SiRamMb |
Physical RAM (Mb) |
|
$SystemDrive |
System Drive |
|
$VerboseOS |
Verbose Operating System version |
|
$OSCSDVersion |
Current service pack |
|
$HotFixes |
Current Hot Fixes |
|
$IeCurVer |
Internet Explorer version |
|
$OfficeCurVer |
Microsoft Office version |
|
$UserID |
User ID |
|
$FullName |
User's full name |
|
$Description |
User account Description |
View logs
Click the View Logs tab to open the Log File Viewer.
Available logs
Filter the available log files by Profile, Year and Month.
Purge old log files
Purge log files older than
Enter the age of log files to purge. Files must be older than the number of months specified. Click Purge to remove files.
Message Boxes
The Message Boxes object allows you to centrally manage and configure popup messages. This popup window is displayed on the client during the logon process after the user is authenticated. Message boxes can be used to notify users of scheduled downtime or upcoming company events.
Since displaying Message Boxes could interfere with the automatic logon process, Message Boxes will NOT be displayed on any computer if AutoAdminLogon is enabled.
Settings
Message box
Window title
Type in static text or press the F2 key to select a dynamic variable. The window title is displayed at the top of the popup window.
Message
Enter the text to be displayed in the message box. Dynamic variables can be used in conjunction with your text. Press the F2 key to select a dynamic variable.
Style
Select a message box style from the Style list. Choose from Information, Warning, or Error. Each style displays an icon to the left of the message. The styles make use of the following icons in the message box:
Information (i)
Warning (!)
Error (x)
Timeout
Enter a numeric value representing the number of seconds the message box will be displayed for. It will be displayed for this number of seconds unless the OK button is pressed before the timeout occurs. Enter 0 to disable the timeout function.
Cycle
UID
The UID entry is used to make each element in the Message Box list, a unique item, regardless of the contents of the message box. The data in this entry is automatically generated and should not be modified. However, if an configuration element in the list is set to run Once Per Day or One Time, and must be executed a second time, the UID can be changed by clicking 
Frequency
Select One Time (Computer),One Time (User) ,Once Per Day (Computer) ,Once Per Day (User), Every time elect a logon frequency from the drop-down list. Select from
- Select Every time to display the Message Box at the specified cycle, every time the user logs on or off the network.
- Select Once Per Day (User) to display the Message Box at the specified cycle, one time per day for the current user.
- Select Once Per Day (Computer) to display the Message Box at the specified cycle, one time per day for the computer.
- Select One Time (User) to display the Message Box at the specified cycle, a single time for the current user.
- Select One Time (Computer) to display the Message Box at the specified cycle, a single time for the computer.
The Message Box is displayed at the specified cycle and frequency.
Cycle
Select a time interval for which your message box will display. Choose from Everyday, Day of Week, Monthly (Day of Week), Monthly (Day of Month), or Specific Date.
- Selecting Every time as the cycle, will force the Message Box to be displayed each logon, logoff and refresh as specified in the validation logic.
- Selecting Day of Week as the cycle presents a new Day of Week list allowing the selection of a day from Sunday to Saturday. The Message Box will be displayed on the specified day, every week, at the selected frequency.
- Selecting Monthly (Day of Week) as the cycle, presents a new Day of Month list allowing the selection of a day in the month ranging from 1st Sunday, 1st Monday, . . . to the last Saturday of the month. The Message Box will be displayed on the specified day, at the selected frequency.
- Selecting Monthly (Day of Month) as the cycle, presents a new Day of Month list allowing the selection of a day number of the month. The Message Box will be displayed on the specified day of the month, at the selected frequency.
- Selecting Specific Date as the cycle presents an entry to which the specific date should be entered. Press the Date arrow to make your date selection from any calendar day. The Message Box will be displayed on the specific day, at the selected frequency.
Validation Logic
Select the Validation Logic tab to set the validation rules for this element.
Notes
Select the Notes tab to create any additional notes needed to document the profile element.
Description
When adding or modifying a profile object element, the description appears above the settings tab. Enter a description to annotate the element. The default value for new profile elements can be changed by going to the system Preferences.
Microsoft Office Settings
Microsoft Office Settings
The Microsoft Office object provides the ability to centrally configure default file locations for Microsoft Office.
By centrally configuring the paths used by Microsoft Office, it is ensured that user-created documents are stored to network servers rather than locally on the user’s computer. This enables documents to be secured, backed up nightly, and made available to the user regardless of which computer the user logs on from.
|
|
Note: Microsoft Office 2010 and 2016 are supported. |
Settings
Application options
Application/suite
Select an application including the version from the list.
Option
Select an option from the list. The content of the list varies based on the Application/Suite chosen.
Path
Specify a path that the selected option should be redirected to. The path may be in the form of a path, mapped drive or UNC. Click Browse to navigate to the path. Optionally, press the F2 key to use a Desktop Authority dynamic variable.
Validation Logic
Select the Validation Logic tab to set the validation rules for this element.
Notes
Select the Notes tab to create any additional notes needed to document the profile element.
Description
When adding or modifying a profile object element, the description appears above the settings tab. Enter a description to annotate the element. The default value for new profile elements can be changed by going to the system Preferences.
Microsoft Outlook Profiles
The Microsoft Outlook Profiles object provides the ability to configure one or more client mail profiles. Mail profiles are part of the Windows Messaging system and are used to define the services and options needed to connect the Outlook client to your Microsoft Exchange server. An administrative template can be established that will automatically configure the most common services used by Outlook when your clients log on to the network.
Desktop Authority will automatically create mail profiles for a user on any computer that they log on to. With Desktop Authority performing this necessary administrative task, a visit to each desktop will be saved. Your users will benefit from increased productivity if they roam to different computers — no matter which computer they log on to. They will have access to their electronic mail instantly!
Mail Profile creation requires Internet Explorer 4.01 or greater to be installed on the client.
|
|
NOTE: Microsoft Outlook 2010, 2013, 2016,Exchange 2010, 2013, 2016 and Exchange Online are supported. |
|
|
NOTE: Exchange Online support (Microsoft's cloud-based Exchange solution) is limited to the on-premise configuration of supported versions of Microsoft Outlook as an Exchange Online email client. It does not include support for configuring any cloud-based (off-premise) Exchange Online server or client properties. |
Settings
Mail profile
If user has an existing profile, do not apply the settings below
Select this check box disable the creation of profiles for users that have existing profiles on the client they are logging in from. Clear this check box to enable the creation of mail profiles regardless of whether there are existing profiles for the user.
Delete all profiles except for user's default profile
Select this check box to delete all profiles for this user except the user's default profile.
Rename user's existing default profile if mail profile name is different
If the user mail profile name is different than what is specified as the Mailbox name, select this check box to rename the existing profile. Leave this check box clear to keep the existing profile name.
Delete all backup profiles created during configuration
Select this check box to remove all backup profiles.
Mail profile name
Enter the name to be used for the new profile creation. This can be static text, a Desktop Authority dynamic variable, or a combination of the two. Press the F2 key to select a dynamic variable.
The default value for the mail profile name is $FullName.
Mailbox name
Enter the name of the mailbox the user will be connected to on the Exchange Server. Press the F2 key to select a dynamic variable.
The Mailbox name must match the Display Name, Alias or Distinguished Object name defined for the user on the Exchange Server. To achieve this, use a dynamic variable. This may need to be used in combination with static text.
The default for this field is $UserID, which typically matches the user’s Display Name defined in Exchange.
Exchange Mail server
Enter the name of the Exchange server to which the profile will be connected to. Type the server name into the field or click Browse to locate and select a server. Press the F2 key to select a dynamic variable.
Cached Mode
Select this check box, 
Connect to Microsoft Exchange using HTTP
Select this check box, 
Exchange CAS (Proxy) server
Enter the name of the client access server or proxy server. Type the server name into the field or click Browse to locate and select a server. Press the F2 key to select a dynamic variable.
Connect using SSL only
Select this check box, 
On fast networks, connect using HTTP first, then connect using TCP/IP
Select this check box, 
On slow networks, connect using HTTP first, then connect using TCP/IP
Select this check box, 
Use this authentication when connecting to my proxy server for Exchange
Open the drop down list and select the authentication method you want to use when connecting to your proxy server. Options include Negotiate, Basic and NTLM Authentication.
|
|
Note: Please refer to your Exchange/Outlook version-specific documentation for more information regarding authentication. |
Additional mailboxes
|
|
Note: Please note that Microsoft Outlook must be opened once on individual client machines before Desktop Authority is able to configure additional mailboxes. |
Many times it is necessary to assign a delegate to a mailbox. A delegate is someone who is given permission to view a mailbox other than their own. The mailbox will be added to the delegates profile and be visible to the user when Outlook opens. Click Add to add a mailbox to the Mailbox list. Specify the mailbox owner's UserName as the mailbox name. Click Delete to remove the selected mailbox from the mailbox list.
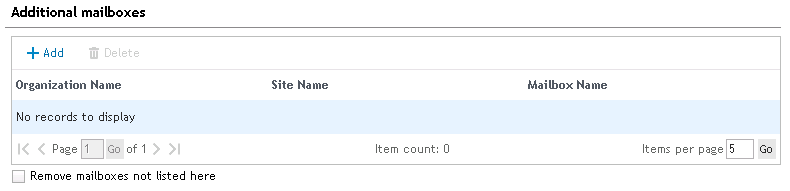
Additional mailboxes will be assigned to any user who validates for the configuration setting. In order for the user to have permission to view the additional mailbox, the delegate must be granted permission to view the nominated mailbox. Desktop Authority will take care of adding the additional mailboxes to the delegate's profile.
Remove mailboxes not listed here
Select this check box to remove any mailbox associated with the mail profile that is not explicitly defined in the Desktop Authority mailbox list.
Validation Logic
Select the Validation Logic tab to set the validation rules for this element.
Notes
Select the Notes tab to create any additional notes needed to document the profile element.
Description
When adding or modifying a profile object element, the description appears above the settings tab. Enter a description to annotate the element. The default value for new profile elements can be changed by going to the system Preferences.


