- Create GPO Central Store On The Domain Controllers.
The creation of the Central Store for GPO templates is mandatory in Windows 2008 or newer especially to add and distribute new GPO templates to the domain. To create the central store, perform the following:
- On a domain controller, navigate to \\domaincontroller\Sysvol. This should take you to C:\Windows\Sysvol\Sysvol.
- Drill down to the directories: <domain FQDN>\Policies
- Create the directory named PolicyDefinitions under the Policies directory. Allow permissions to inherit.
- The result should be a directory on disk with this path: C:\Windows\Sysvol\Sysvol\<domain FQDN>\policies\PolicyDefinitions.
- From the domain controller, navigate to c:\Windows\PolicyDefinitions.
- Copy the contents of that directory, including the subdirectories to the newly created PolicyDefinitions folder under Sysvol. This will create the Central Store for GPOs and will cause all of the GPO templates to be replicated.
Microsoft Reference for creating a Central Store: https://support.microsoft.com/en-us/kb/929841
- Add The Active Administrator ADMX Files To The GPO Repository And Add The Agent Installer To The Netlogon Share On The Domain Controller.
Active Administrator includes GPO templates for the managing of the data collection for workstation logons. In order to instruct the agent on where and over what port, this GPO template must be used.
- On the server where Active Administrator is installed, navigate to C:\Program Files\Quest\Active Administrator\Server\WorkstationLogonAuditAgent directory
- Inside the directory will be three files; the agent MSI, the .ADMX, and the .ADML file.
- Copy the .ADMX file to the following location ON THE DOMAIN CONTROLLER where the Central Store was created: C:\Windows\Sysvol\Sysvol\<domain FQDN>\policies\PolicyDefinitions.
- Copy the .ADML file to the following location ON THE DOMAIN CONTROLLER where the Central Store was created: C:\Windows\Sysvol\Sysvol\<domain FQDN>\policies\PolicyDefinitions\en-US. *For non-US users, place the ADML file in the appropriate language folder in the Central Store.
- Copy the Workstation Agent Installer to the NETLOGON share on the domain controller.
- Configure a GPO to install and configure the workstation auditing agent
To complete this operation you must create and configure a GPO to install and set the configuration information required for the agent to collect and send the logon data.
-
- Open the GPMC on a domain controller.
- Create and link a new GPO to an OU which contains workstations.
-
In the GPO, create a software package which references the Active Administrator Workstation Auditing Agent from its place in the Netlogon share. The path should be %Logonserver%\netlogon\Active Administrator Workstation Audit Agent.MSI. The logon server will be resolved to a DC name.
- In the same GPO, under the Computer Configuration | Policies | Administrative Templates: Policy definitions (ADMX files) retrieved from the Central Store | Quest Software | Active Administrator there will be policy settings which need to be set:
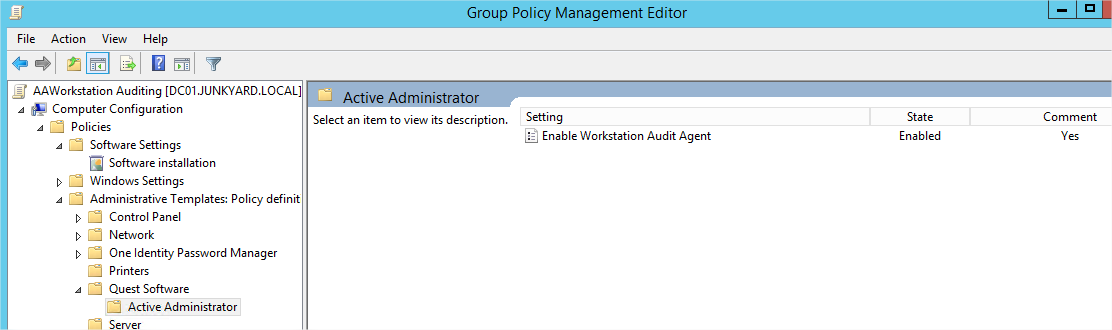
-
- Enter the settings for the GPO: The Agent should be ENABLED, the Active Administrator Server name supplied and the server port defined. Port 15601 is the default. Ensure that this port is open on all firewalls between the clients and the Active Administrator server.
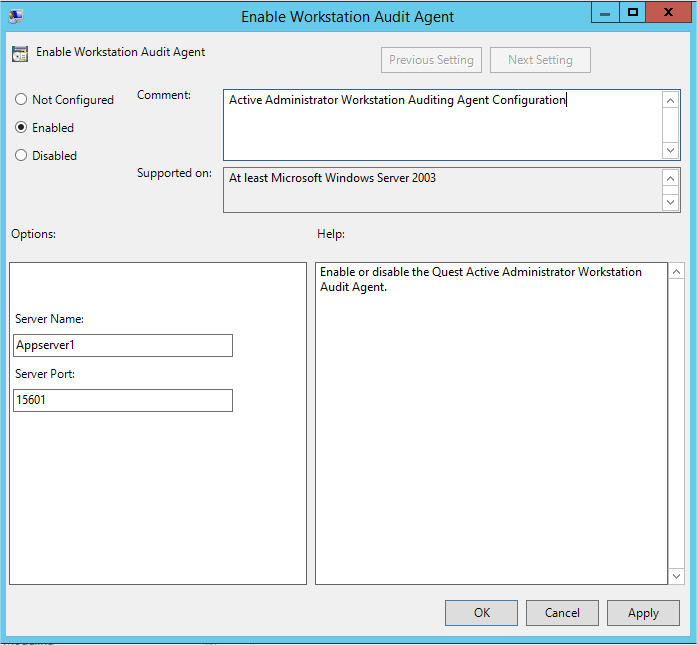
The next step is to allow the GPO to run on the workstations to install the agent and configure the agent settings. When this is completed it should be verified to ensure it is complete. To do this, the best way is to confirm in the client machine’s registry settings.
- Verifying the installation and configuration of the Workstation Logon Auditing Agent.
- Navigate to the workstation’s registry settings, this can be performed locally or remotely on the workstation using Regedit.exe.
- To verify that the Agent is installed ensure that this registry key exists:
- HKLM\Software\Policies\Quest Software\ActiveAdministrator\Settings
- HKLM\Software\Wow6432Node\Policies\Quest Software \ActiveAdministrator\Settings
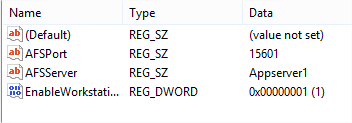
- To verify that the Agent settings have been implemented, navigate to HKLM\Software\Policies\Quest Software\ActiveAdministrator\Settings. In this location, you should see settings indicating the port used as AFSPort, the AA server listed as AFSServer and the enabling of the workstation agent as EnableWorkstationAuditAgent as shown below.
- Ensuring the Workstation Logon Audit is enabled in the Active Administrator Console.
There are two locations in the Active Administrator console where the Workstation Logon Auditing settings can be modified; under the Server Configuration and under the Auditing & Alerting Event Definitions.
-
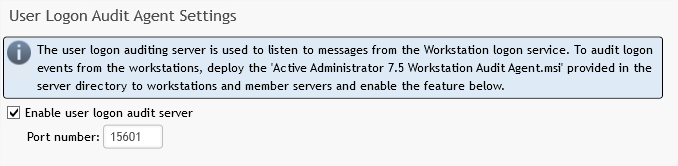
- Configuration. In the Active Administrator Console, at the bottom of the left side navigation pane, expand CONFIGURATION.
- On the right side of the console, the user will see several tiles. Select Workstation Logon Settings.
- Ensure the Enable User Logon Audit Server is selected, and the port is properly set. The default port value is 15601.
-
- In the Active Administrator Console, at the bottom of the left side navigation pane, expand “Auditing & Alerting”.
- On the right side of the console, select “Event Definitions”.
- Click on the “Definition Type” column header to reverse sort the Auditing Definitions – Find “Workstation” at the top of the list.
- Select all of the workstation events and right click to “Enable”.
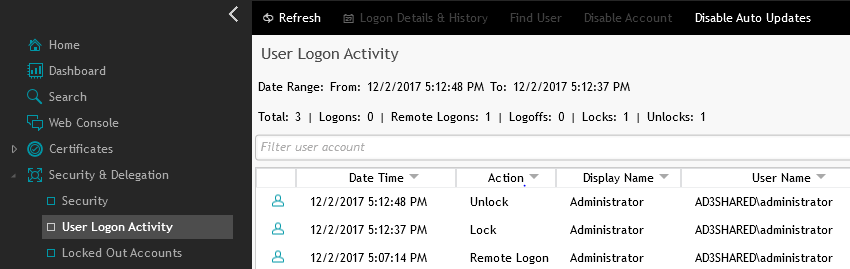
Navigate the Auditing & Alerting section and select “User Logon Activity” to review the auditing data for workstation logons.