4.2 Workstation and Member Server System Requirements
4.1 Migrator Pro for Active Directory Basic Installation Requirements
The Migrator Pro for Active Directory suite consists of Directory Sync Pro and Migrator Pro for Active Directory software packages. Both packages will require access to Microsoft SQL Server.
Single Server Installation Requirements
|
Supported Operating Systems |
|
|
SQL Server Requirements |
|
|
Minimum Hardware Requirements |
|
|
Additional Components |
|
If you are planning to have a long-term co-existence (1 year+), we recommend using the following formula to determine if you should use a full edition of SQL Server with our products. This formula assumes High / Verbose logging turned on for all profiles = worst case scenario.
Formula: (Expected months of co-existence x Users) x Profiles = N
If calculated N >= 12000 then we recommend full edition of SQL Server.
-
Low example: 3 months x 300 users x 1 profile = 900
-
Medium example: 6 months x 1000 users x 2 profiles = 12000
-
High example: 12 months x 3000 users x 5 profiles = 180,000
-
Extreme example: 14 months x 6000 users x 7 profiles = 588,000
Multi-Server Installation Requirements
Migrator Pro for Active Directory is scalable and supports segregating components and can be installed in a multi-server configuration to support larger or complex environments.
If required in larger installations, remote SQL Servers may be used for the primary database and the logging database. Additionally, the primary database and the logging database can be segregated onto separate SQL Server instances.
Each of the following roles/functions may be separated onto different servers as required in advanced configurations:
-
Directory Sync Pro for Active Directory/Migrator Pro for Active Directory Administrative Web Interface
-
Migrator Pro for Active Directory Web Service
-
Directory Sync Pro for Active Directory Databases
When installed independently, the components require the following resources:
|
Supported Operating Systems |
|
|
Migrator Pro for Active Directory Split Role Minimum Hardware Requirements |
|
|
Directory Sync Pro for Active Directory Hardware Requirements |
|
|
SQL Server |
|
|
Additional Components |
|
Report Server Requirements
|
SQL Server Requirements |
|
4.2 Workstation and Member Server System Requirements
|
Supported Operating Systems |
|
|
PowerShell Requirements |
|
|
.NET Framework Requirements |
|
4.3 Admin Agent Device Requirements
|
Operating System Requirements |
|
|
Supported Operating Systems |
|
|
Additional Requirements |
|
Domain Controller Access
For most scenarios, Migrator Pro for Active Directory requires access to at least one read/write domain controller in each source and target Active Directory domain. For fault tolerance, at least two domain controllers in each source and target domain is recommended.
If SID History will be synchronized, any domain controller listed in the Target DCs tab within a Directory Sync Pro for Active Directory profile will require access to the domain controller holding the PDC Emulator Active Directory FSMO role in the source. Keep in mind that even if the domain controller holding the PDC Emulator Active Directory FSMO role is not listed in the Source DCs tab, any SID History migration attempts will require a DC in the target to communicate with the PDC Emulator domain controller. For this reason, it is a best practice to ensure that all domain controllers specified on the Target DCs screen within a Directory Sync Pro for Active Directory profile have the appropriate networks access to communicate with the source domain controller holding the PDC Emulator Active Directory FSMO role before a SID History migration is attempted.
In limited scenarios, it is possible that Migrator Pro for Active Directory will not be responsible for creating or updating any accounts in the source or the target domains. In this scenario, Migrator Pro for Active Directory can be configured to communicate with Read Only Domain Controllers (RODCs).
Network/Firewall Requirements
Migrator Pro for Active Directory requires the following network ports to enable full functionality:
|
Source |
Target |
Port/Protocol |
|
Workstations and Member Servers |
Migrator Pro for Active Directory Server |
443 (TCP) or 80 (TCP) |
|
Migrator Pro for Active Directory Server |
Source and Target Domain Controllers |
135, 137, 389, 445, 1024-5000 (TCP) 389 (UDP) |
|
Migrator Pro for Active Directory Server |
Source and Target Domain Controllers |
135, 137, 389, 445, 49152-65535 (TCP) 389 (UDP) |
|
Target domain controllers listed in the Target DCs tab |
Domain controller in the source environment holding the PDC Emulator Active Directory FSMO role |
135, 137, 139, 389, 445, 3268 and 49152-65535 (TCP) 389 (UDP) |
The following ports need to be opened between workstations/servers and writable domain controllers for a successful domain join operation:
|
Type of Traffic |
Protocol and Port |
|
DNS |
TCP/UDP 53 |
|
Kerberos |
TCP/UDP 88 |
|
EPM |
TCP 135 |
|
NetLogon, NetBIOS Name Resolution |
UDP 137 |
|
DFSN, NetLogon, NetBIOS Datagram Service |
UDP 138 |
|
DFSN, NetBIOS Session Service, NetLogon |
TCP 139 |
|
C-LDAP |
TCP/UDP 389 |
|
DFS, LsaRpc, NbtSS, NetLogonR, SamR, SMB, SrvSvc |
TCP/UDP 445 |
|
LDAP SSL |
TCP 636 |
|
Random RPC |
TCP 1024-5000 |
|
GC |
TCP 3268 |
|
GC |
TCP 3269 |
|
DFS-R |
TCP 5722 |
|
Random RPC |
TCP 49152-65535 |
4.5 SSL Certificate Requirements
Migrator Pro for Active Directory does not require HTTPS (HTTP with SSL), and can operate using HTTP. However, it is strongly recommended to implement Migrator Pro for Active Directory using HTTPS to secure communications between the devices to be migrated and the Migrator Pro for Active Directory Server. In order to activate HTTPS on the IIS component in Windows, the Migrator Pro for Active Directory system will require that a SSL certificate is present.
An SSL Certificate is not provided as part of the installation. For the most secure installation, purchasing an SSL Certificate from a Windows supported 3rd party provider is recommended.
In scenarios where this is not possible, self-signed SSL Certificate can be generated in Windows following these directions: https://technet.microsoft.com/en-us/library/cc753127(v=ws.10).aspx
If using a self-signed certificate, it should be noted that Migrator Pro for Active Directory’s agent component would utilize the operating system’s certificate trust list. Due to the security nature of Active Directory migrations, there is no method of implementing an override and forcing the agent to use an untrusted certificate. If a self-signed certificate is used, that certificate will need to be added to the trusted root certificate list for all computer objects to be migrated. This can be accomplished via group policy: https://technet.microsoft.com/en-us/library/cc738131(v=ws.10).aspx
4.6 Service Account Requirements
Migrator Pro for Active Directory requires the following user account permissions and privileges to support Active Directory migrations:
-
One service account with read/write access to all organizational units (OUs) containing user, group, and computer objects in the source Active Directory to be migrated to the target environment.
-
One service account with administrative rights on the target domain(s)
-
If administrative rights cannot be granted, the service account requires the following rights:
-
The ability to create and modify user objects in the desired OUs in the target Active Directory environment.
-
Read Permissions to the configuration container in Active Directory
-
User credentials with the delegated migrateSIDHistory extended right.
-
-
-
A service account in each source and target domain with the ability to modify computer objects and add computers to the domain.
4.7 SQL Server Reporting Services (SSRS) Account Requirements
Migrator Pro for Active Directory's Reporting feature requires credentials in the following places:
-
Content credential: Credential for accessing the report server content.
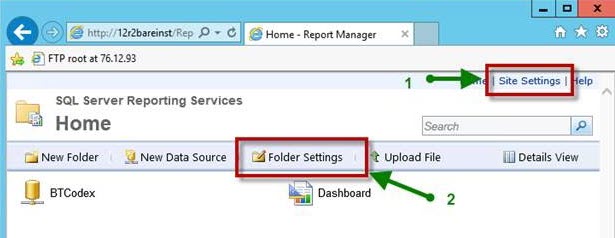
You must set the securities in two different places in the SSRS ‘Report Manager’ web interface (http://<servername>/Reports) to connect to the report server and upload reports from the installation program.
In the Site Settings, you MUST enable the ‘System Administrator’ role during installation. After installation is complete, you may change this user’s role to ‘System User’ if desired.
In the Folder Settings, you must add the same user with (at least) ‘Browser’ permission.

-
Data Source Credential: The Data Source is used to access queries in the ADM database. These credentials and roles are set in the SQL server with SSMS
The user must have public, db_reader, and db_executor roles on the ADM database.
The user must have the public role on the report server and report server temp databases.
4.8 DNS SRV Record Requirement
In each source domain, a SRV DNS record must be created to enable autodiscover for Migrator Pro for Active Directory agents.
-
To enable autodiscover when HTTPS is desired
-
Record Name: _btadm._https.SourceDomainName.Local
-
Weight and Priority: 0
-
Port Number: 443
-
-
To enable autodiscover when HTTP is desired
-
Record Name: _btadm._http.SourceDomainName.Local
-
Weight and Priority: 0
-
Port Number: 80
-
4.9 Offline Domain Join (ODJ) Requirements
In order to successfully facilitate the new Cached Credentials job (which supports the Offline Domain Join feature) a one-way external trust must be configured from the source domain to the target domain.
The devices that the ODJ process is being run on must have network connectivity to BOTH the source and target environments at the same time in order to have the Cached Credentials function work properly.
Offline domain join files must be created prior to running the Offline Domain Join process. A full explanation of Microsoft’s Djoin.exe utility and how to create these files can be found here:
https://technet.microsoft.com/en-us/library/offline-domain-join-djoin-step-by-step%28v=ws.10%29.aspx
Section 5. Requirements for Both Directory Sync Pro for Active Directory and Migrator Pro for Active Directory
4.3 Admin Agent Device Requirements
4.1 Migrator Pro for Active Directory Basic Installation Requirements
The Migrator Pro for Active Directory suite consists of Directory Sync Pro and Migrator Pro for Active Directory software packages. Both packages will require access to Microsoft SQL Server.
Single Server Installation Requirements
|
Supported Operating Systems |
|
|
SQL Server Requirements |
|
|
Minimum Hardware Requirements |
|
|
Additional Components |
|
If you are planning to have a long-term co-existence (1 year+), we recommend using the following formula to determine if you should use a full edition of SQL Server with our products. This formula assumes High / Verbose logging turned on for all profiles = worst case scenario.
Formula: (Expected months of co-existence x Users) x Profiles = N
If calculated N >= 12000 then we recommend full edition of SQL Server.
-
Low example: 3 months x 300 users x 1 profile = 900
-
Medium example: 6 months x 1000 users x 2 profiles = 12000
-
High example: 12 months x 3000 users x 5 profiles = 180,000
-
Extreme example: 14 months x 6000 users x 7 profiles = 588,000
Multi-Server Installation Requirements
Migrator Pro for Active Directory is scalable and supports segregating components and can be installed in a multi-server configuration to support larger or complex environments.
If required in larger installations, remote SQL Servers may be used for the primary database and the logging database. Additionally, the primary database and the logging database can be segregated onto separate SQL Server instances.
Each of the following roles/functions may be separated onto different servers as required in advanced configurations:
-
Directory Sync Pro for Active Directory/Migrator Pro for Active Directory Administrative Web Interface
-
Migrator Pro for Active Directory Web Service
-
Directory Sync Pro for Active Directory Databases
When installed independently, the components require the following resources:
|
Supported Operating Systems |
|
|
Migrator Pro for Active Directory Split Role Minimum Hardware Requirements |
|
|
Directory Sync Pro for Active Directory Hardware Requirements |
|
|
SQL Server |
|
|
Additional Components |
|
Report Server Requirements
|
SQL Server Requirements |
|
4.2 Workstation and Member Server System Requirements
|
Supported Operating Systems |
|
|
PowerShell Requirements |
|
|
.NET Framework Requirements |
|
4.3 Admin Agent Device Requirements
|
Operating System Requirements |
|
|
Supported Operating Systems |
|
|
Additional Requirements |
|
Domain Controller Access
For most scenarios, Migrator Pro for Active Directory requires access to at least one read/write domain controller in each source and target Active Directory domain. For fault tolerance, at least two domain controllers in each source and target domain is recommended.
If SID History will be synchronized, any domain controller listed in the Target DCs tab within a Directory Sync Pro for Active Directory profile will require access to the domain controller holding the PDC Emulator Active Directory FSMO role in the source. Keep in mind that even if the domain controller holding the PDC Emulator Active Directory FSMO role is not listed in the Source DCs tab, any SID History migration attempts will require a DC in the target to communicate with the PDC Emulator domain controller. For this reason, it is a best practice to ensure that all domain controllers specified on the Target DCs screen within a Directory Sync Pro for Active Directory profile have the appropriate networks access to communicate with the source domain controller holding the PDC Emulator Active Directory FSMO role before a SID History migration is attempted.
In limited scenarios, it is possible that Migrator Pro for Active Directory will not be responsible for creating or updating any accounts in the source or the target domains. In this scenario, Migrator Pro for Active Directory can be configured to communicate with Read Only Domain Controllers (RODCs).
Network/Firewall Requirements
Migrator Pro for Active Directory requires the following network ports to enable full functionality:
|
Source |
Target |
Port/Protocol |
|
Workstations and Member Servers |
Migrator Pro for Active Directory Server |
443 (TCP) or 80 (TCP) |
|
Migrator Pro for Active Directory Server |
Source and Target Domain Controllers |
135, 137, 389, 445, 1024-5000 (TCP) 389 (UDP) |
|
Migrator Pro for Active Directory Server |
Source and Target Domain Controllers |
135, 137, 389, 445, 49152-65535 (TCP) 389 (UDP) |
|
Target domain controllers listed in the Target DCs tab |
Domain controller in the source environment holding the PDC Emulator Active Directory FSMO role |
135, 137, 139, 389, 445, 3268 and 49152-65535 (TCP) 389 (UDP) |
The following ports need to be opened between workstations/servers and writable domain controllers for a successful domain join operation:
|
Type of Traffic |
Protocol and Port |
|
DNS |
TCP/UDP 53 |
|
Kerberos |
TCP/UDP 88 |
|
EPM |
TCP 135 |
|
NetLogon, NetBIOS Name Resolution |
UDP 137 |
|
DFSN, NetLogon, NetBIOS Datagram Service |
UDP 138 |
|
DFSN, NetBIOS Session Service, NetLogon |
TCP 139 |
|
C-LDAP |
TCP/UDP 389 |
|
DFS, LsaRpc, NbtSS, NetLogonR, SamR, SMB, SrvSvc |
TCP/UDP 445 |
|
LDAP SSL |
TCP 636 |
|
Random RPC |
TCP 1024-5000 |
|
GC |
TCP 3268 |
|
GC |
TCP 3269 |
|
DFS-R |
TCP 5722 |
|
Random RPC |
TCP 49152-65535 |
4.5 SSL Certificate Requirements
Migrator Pro for Active Directory does not require HTTPS (HTTP with SSL), and can operate using HTTP. However, it is strongly recommended to implement Migrator Pro for Active Directory using HTTPS to secure communications between the devices to be migrated and the Migrator Pro for Active Directory Server. In order to activate HTTPS on the IIS component in Windows, the Migrator Pro for Active Directory system will require that a SSL certificate is present.
An SSL Certificate is not provided as part of the installation. For the most secure installation, purchasing an SSL Certificate from a Windows supported 3rd party provider is recommended.
In scenarios where this is not possible, self-signed SSL Certificate can be generated in Windows following these directions: https://technet.microsoft.com/en-us/library/cc753127(v=ws.10).aspx
If using a self-signed certificate, it should be noted that Migrator Pro for Active Directory’s agent component would utilize the operating system’s certificate trust list. Due to the security nature of Active Directory migrations, there is no method of implementing an override and forcing the agent to use an untrusted certificate. If a self-signed certificate is used, that certificate will need to be added to the trusted root certificate list for all computer objects to be migrated. This can be accomplished via group policy: https://technet.microsoft.com/en-us/library/cc738131(v=ws.10).aspx
4.6 Service Account Requirements
Migrator Pro for Active Directory requires the following user account permissions and privileges to support Active Directory migrations:
-
One service account with read/write access to all organizational units (OUs) containing user, group, and computer objects in the source Active Directory to be migrated to the target environment.
-
One service account with administrative rights on the target domain(s)
-
If administrative rights cannot be granted, the service account requires the following rights:
-
The ability to create and modify user objects in the desired OUs in the target Active Directory environment.
-
Read Permissions to the configuration container in Active Directory
-
User credentials with the delegated migrateSIDHistory extended right.
-
-
-
A service account in each source and target domain with the ability to modify computer objects and add computers to the domain.
4.7 SQL Server Reporting Services (SSRS) Account Requirements
Migrator Pro for Active Directory's Reporting feature requires credentials in the following places:
-
Content credential: Credential for accessing the report server content.
You must set the securities in two different places in the SSRS ‘Report Manager’ web interface (http://<servername>/Reports) to connect to the report server and upload reports from the installation program.
In the Site Settings, you MUST enable the ‘System Administrator’ role during installation. After installation is complete, you may change this user’s role to ‘System User’ if desired.
In the Folder Settings, you must add the same user with (at least) ‘Browser’ permission.

-
Data Source Credential: The Data Source is used to access queries in the ADM database. These credentials and roles are set in the SQL server with SSMS
The user must have public, db_reader, and db_executor roles on the ADM database.
The user must have the public role on the report server and report server temp databases.

4.8 DNS SRV Record Requirement
In each source domain, a SRV DNS record must be created to enable autodiscover for Migrator Pro for Active Directory agents.
-
To enable autodiscover when HTTPS is desired
-
Record Name: _btadm._https.SourceDomainName.Local
-
Weight and Priority: 0
-
Port Number: 443
-
-
To enable autodiscover when HTTP is desired
-
Record Name: _btadm._http.SourceDomainName.Local
-
Weight and Priority: 0
-
Port Number: 80
-
4.9 Offline Domain Join (ODJ) Requirements
In order to successfully facilitate the new Cached Credentials job (which supports the Offline Domain Join feature) a one-way external trust must be configured from the source domain to the target domain.
The devices that the ODJ process is being run on must have network connectivity to BOTH the source and target environments at the same time in order to have the Cached Credentials function work properly.
Offline domain join files must be created prior to running the Offline Domain Join process. A full explanation of Microsoft’s Djoin.exe utility and how to create these files can be found here:
https://technet.microsoft.com/en-us/library/offline-domain-join-djoin-step-by-step%28v=ws.10%29.aspx
Section 5. Requirements for Both Directory Sync Pro for Active Directory and Migrator Pro for Active Directory
4.4 Networking Requirements
4.1 Migrator Pro for Active Directory Basic Installation Requirements
The Migrator Pro for Active Directory suite consists of Directory Sync Pro and Migrator Pro for Active Directory software packages. Both packages will require access to Microsoft SQL Server.
Single Server Installation Requirements
|
Supported Operating Systems |
|
|
SQL Server Requirements |
|
|
Minimum Hardware Requirements |
|
|
Additional Components |
|
If you are planning to have a long-term co-existence (1 year+), we recommend using the following formula to determine if you should use a full edition of SQL Server with our products. This formula assumes High / Verbose logging turned on for all profiles = worst case scenario.
Formula: (Expected months of co-existence x Users) x Profiles = N
If calculated N >= 12000 then we recommend full edition of SQL Server.
-
Low example: 3 months x 300 users x 1 profile = 900
-
Medium example: 6 months x 1000 users x 2 profiles = 12000
-
High example: 12 months x 3000 users x 5 profiles = 180,000
-
Extreme example: 14 months x 6000 users x 7 profiles = 588,000
Multi-Server Installation Requirements
Migrator Pro for Active Directory is scalable and supports segregating components and can be installed in a multi-server configuration to support larger or complex environments.
If required in larger installations, remote SQL Servers may be used for the primary database and the logging database. Additionally, the primary database and the logging database can be segregated onto separate SQL Server instances.
Each of the following roles/functions may be separated onto different servers as required in advanced configurations:
-
Directory Sync Pro for Active Directory/Migrator Pro for Active Directory Administrative Web Interface
-
Migrator Pro for Active Directory Web Service
-
Directory Sync Pro for Active Directory Databases
When installed independently, the components require the following resources:
|
Supported Operating Systems |
|
|
Migrator Pro for Active Directory Split Role Minimum Hardware Requirements |
|
|
Directory Sync Pro for Active Directory Hardware Requirements |
|
|
SQL Server |
|
|
Additional Components |
|
Report Server Requirements
|
SQL Server Requirements |
|
4.2 Workstation and Member Server System Requirements
|
Supported Operating Systems |
|
|
PowerShell Requirements |
|
|
.NET Framework Requirements |
|
4.3 Admin Agent Device Requirements
|
Operating System Requirements |
|
|
Supported Operating Systems |
|
|
Additional Requirements |
|
Domain Controller Access
For most scenarios, Migrator Pro for Active Directory requires access to at least one read/write domain controller in each source and target Active Directory domain. For fault tolerance, at least two domain controllers in each source and target domain is recommended.
If SID History will be synchronized, any domain controller listed in the Target DCs tab within a Directory Sync Pro for Active Directory profile will require access to the domain controller holding the PDC Emulator Active Directory FSMO role in the source. Keep in mind that even if the domain controller holding the PDC Emulator Active Directory FSMO role is not listed in the Source DCs tab, any SID History migration attempts will require a DC in the target to communicate with the PDC Emulator domain controller. For this reason, it is a best practice to ensure that all domain controllers specified on the Target DCs screen within a Directory Sync Pro for Active Directory profile have the appropriate networks access to communicate with the source domain controller holding the PDC Emulator Active Directory FSMO role before a SID History migration is attempted.
In limited scenarios, it is possible that Migrator Pro for Active Directory will not be responsible for creating or updating any accounts in the source or the target domains. In this scenario, Migrator Pro for Active Directory can be configured to communicate with Read Only Domain Controllers (RODCs).
Network/Firewall Requirements
Migrator Pro for Active Directory requires the following network ports to enable full functionality:
|
Source |
Target |
Port/Protocol |
|
Workstations and Member Servers |
Migrator Pro for Active Directory Server |
443 (TCP) or 80 (TCP) |
|
Migrator Pro for Active Directory Server |
Source and Target Domain Controllers |
135, 137, 389, 445, 1024-5000 (TCP) 389 (UDP) |
|
Migrator Pro for Active Directory Server |
Source and Target Domain Controllers |
135, 137, 389, 445, 49152-65535 (TCP) 389 (UDP) |
|
Target domain controllers listed in the Target DCs tab |
Domain controller in the source environment holding the PDC Emulator Active Directory FSMO role |
135, 137, 139, 389, 445, 3268 and 49152-65535 (TCP) 389 (UDP) |
The following ports need to be opened between workstations/servers and writable domain controllers for a successful domain join operation:
|
Type of Traffic |
Protocol and Port |
|
DNS |
TCP/UDP 53 |
|
Kerberos |
TCP/UDP 88 |
|
EPM |
TCP 135 |
|
NetLogon, NetBIOS Name Resolution |
UDP 137 |
|
DFSN, NetLogon, NetBIOS Datagram Service |
UDP 138 |
|
DFSN, NetBIOS Session Service, NetLogon |
TCP 139 |
|
C-LDAP |
TCP/UDP 389 |
|
DFS, LsaRpc, NbtSS, NetLogonR, SamR, SMB, SrvSvc |
TCP/UDP 445 |
|
LDAP SSL |
TCP 636 |
|
Random RPC |
TCP 1024-5000 |
|
GC |
TCP 3268 |
|
GC |
TCP 3269 |
|
DFS-R |
TCP 5722 |
|
Random RPC |
TCP 49152-65535 |
4.5 SSL Certificate Requirements
Migrator Pro for Active Directory does not require HTTPS (HTTP with SSL), and can operate using HTTP. However, it is strongly recommended to implement Migrator Pro for Active Directory using HTTPS to secure communications between the devices to be migrated and the Migrator Pro for Active Directory Server. In order to activate HTTPS on the IIS component in Windows, the Migrator Pro for Active Directory system will require that a SSL certificate is present.
An SSL Certificate is not provided as part of the installation. For the most secure installation, purchasing an SSL Certificate from a Windows supported 3rd party provider is recommended.
In scenarios where this is not possible, self-signed SSL Certificate can be generated in Windows following these directions: https://technet.microsoft.com/en-us/library/cc753127(v=ws.10).aspx
If using a self-signed certificate, it should be noted that Migrator Pro for Active Directory’s agent component would utilize the operating system’s certificate trust list. Due to the security nature of Active Directory migrations, there is no method of implementing an override and forcing the agent to use an untrusted certificate. If a self-signed certificate is used, that certificate will need to be added to the trusted root certificate list for all computer objects to be migrated. This can be accomplished via group policy: https://technet.microsoft.com/en-us/library/cc738131(v=ws.10).aspx
4.6 Service Account Requirements
Migrator Pro for Active Directory requires the following user account permissions and privileges to support Active Directory migrations:
-
One service account with read/write access to all organizational units (OUs) containing user, group, and computer objects in the source Active Directory to be migrated to the target environment.
-
One service account with administrative rights on the target domain(s)
-
If administrative rights cannot be granted, the service account requires the following rights:
-
The ability to create and modify user objects in the desired OUs in the target Active Directory environment.
-
Read Permissions to the configuration container in Active Directory
-
User credentials with the delegated migrateSIDHistory extended right.
-
-
-
A service account in each source and target domain with the ability to modify computer objects and add computers to the domain.
4.7 SQL Server Reporting Services (SSRS) Account Requirements
Migrator Pro for Active Directory's Reporting feature requires credentials in the following places:
-
Content credential: Credential for accessing the report server content.
You must set the securities in two different places in the SSRS ‘Report Manager’ web interface (http://<servername>/Reports) to connect to the report server and upload reports from the installation program.
In the Site Settings, you MUST enable the ‘System Administrator’ role during installation. After installation is complete, you may change this user’s role to ‘System User’ if desired.
In the Folder Settings, you must add the same user with (at least) ‘Browser’ permission.

-
Data Source Credential: The Data Source is used to access queries in the ADM database. These credentials and roles are set in the SQL server with SSMS
The user must have public, db_reader, and db_executor roles on the ADM database.
The user must have the public role on the report server and report server temp databases.

4.8 DNS SRV Record Requirement
In each source domain, a SRV DNS record must be created to enable autodiscover for Migrator Pro for Active Directory agents.
-
To enable autodiscover when HTTPS is desired
-
Record Name: _btadm._https.SourceDomainName.Local
-
Weight and Priority: 0
-
Port Number: 443
-
-
To enable autodiscover when HTTP is desired
-
Record Name: _btadm._http.SourceDomainName.Local
-
Weight and Priority: 0
-
Port Number: 80
-
4.9 Offline Domain Join (ODJ) Requirements
In order to successfully facilitate the new Cached Credentials job (which supports the Offline Domain Join feature) a one-way external trust must be configured from the source domain to the target domain.
The devices that the ODJ process is being run on must have network connectivity to BOTH the source and target environments at the same time in order to have the Cached Credentials function work properly.
Offline domain join files must be created prior to running the Offline Domain Join process. A full explanation of Microsoft’s Djoin.exe utility and how to create these files can be found here:
https://technet.microsoft.com/en-us/library/offline-domain-join-djoin-step-by-step%28v=ws.10%29.aspx
Section 5. Requirements for Both Directory Sync Pro for Active Directory and Migrator Pro for Active Directory
4.5 SSL Certificate Requirements
4.1 Migrator Pro for Active Directory Basic Installation Requirements
The Migrator Pro for Active Directory suite consists of Directory Sync Pro and Migrator Pro for Active Directory software packages. Both packages will require access to Microsoft SQL Server.
Single Server Installation Requirements
|
Supported Operating Systems |
|
|
SQL Server Requirements |
|
|
Minimum Hardware Requirements |
|
|
Additional Components |
|
If you are planning to have a long-term co-existence (1 year+), we recommend using the following formula to determine if you should use a full edition of SQL Server with our products. This formula assumes High / Verbose logging turned on for all profiles = worst case scenario.
Formula: (Expected months of co-existence x Users) x Profiles = N
If calculated N >= 12000 then we recommend full edition of SQL Server.
-
Low example: 3 months x 300 users x 1 profile = 900
-
Medium example: 6 months x 1000 users x 2 profiles = 12000
-
High example: 12 months x 3000 users x 5 profiles = 180,000
-
Extreme example: 14 months x 6000 users x 7 profiles = 588,000
Multi-Server Installation Requirements
Migrator Pro for Active Directory is scalable and supports segregating components and can be installed in a multi-server configuration to support larger or complex environments.
If required in larger installations, remote SQL Servers may be used for the primary database and the logging database. Additionally, the primary database and the logging database can be segregated onto separate SQL Server instances.
Each of the following roles/functions may be separated onto different servers as required in advanced configurations:
-
Directory Sync Pro for Active Directory/Migrator Pro for Active Directory Administrative Web Interface
-
Migrator Pro for Active Directory Web Service
-
Directory Sync Pro for Active Directory Databases
When installed independently, the components require the following resources:
|
Supported Operating Systems |
|
|
Migrator Pro for Active Directory Split Role Minimum Hardware Requirements |
|
|
Directory Sync Pro for Active Directory Hardware Requirements |
|
|
SQL Server |
|
|
Additional Components |
|
Report Server Requirements
|
SQL Server Requirements |
|
4.2 Workstation and Member Server System Requirements
|
Supported Operating Systems |
|
|
PowerShell Requirements |
|
|
.NET Framework Requirements |
|
4.3 Admin Agent Device Requirements
|
Operating System Requirements |
|
|
Supported Operating Systems |
|
|
Additional Requirements |
|
Domain Controller Access
For most scenarios, Migrator Pro for Active Directory requires access to at least one read/write domain controller in each source and target Active Directory domain. For fault tolerance, at least two domain controllers in each source and target domain is recommended.
If SID History will be synchronized, any domain controller listed in the Target DCs tab within a Directory Sync Pro for Active Directory profile will require access to the domain controller holding the PDC Emulator Active Directory FSMO role in the source. Keep in mind that even if the domain controller holding the PDC Emulator Active Directory FSMO role is not listed in the Source DCs tab, any SID History migration attempts will require a DC in the target to communicate with the PDC Emulator domain controller. For this reason, it is a best practice to ensure that all domain controllers specified on the Target DCs screen within a Directory Sync Pro for Active Directory profile have the appropriate networks access to communicate with the source domain controller holding the PDC Emulator Active Directory FSMO role before a SID History migration is attempted.
In limited scenarios, it is possible that Migrator Pro for Active Directory will not be responsible for creating or updating any accounts in the source or the target domains. In this scenario, Migrator Pro for Active Directory can be configured to communicate with Read Only Domain Controllers (RODCs).
Network/Firewall Requirements
Migrator Pro for Active Directory requires the following network ports to enable full functionality:
|
Source |
Target |
Port/Protocol |
|
Workstations and Member Servers |
Migrator Pro for Active Directory Server |
443 (TCP) or 80 (TCP) |
|
Migrator Pro for Active Directory Server |
Source and Target Domain Controllers |
135, 137, 389, 445, 1024-5000 (TCP) 389 (UDP) |
|
Migrator Pro for Active Directory Server |
Source and Target Domain Controllers |
135, 137, 389, 445, 49152-65535 (TCP) 389 (UDP) |
|
Target domain controllers listed in the Target DCs tab |
Domain controller in the source environment holding the PDC Emulator Active Directory FSMO role |
135, 137, 139, 389, 445, 3268 and 49152-65535 (TCP) 389 (UDP) |
The following ports need to be opened between workstations/servers and writable domain controllers for a successful domain join operation:
|
Type of Traffic |
Protocol and Port |
|
DNS |
TCP/UDP 53 |
|
Kerberos |
TCP/UDP 88 |
|
EPM |
TCP 135 |
|
NetLogon, NetBIOS Name Resolution |
UDP 137 |
|
DFSN, NetLogon, NetBIOS Datagram Service |
UDP 138 |
|
DFSN, NetBIOS Session Service, NetLogon |
TCP 139 |
|
C-LDAP |
TCP/UDP 389 |
|
DFS, LsaRpc, NbtSS, NetLogonR, SamR, SMB, SrvSvc |
TCP/UDP 445 |
|
LDAP SSL |
TCP 636 |
|
Random RPC |
TCP 1024-5000 |
|
GC |
TCP 3268 |
|
GC |
TCP 3269 |
|
DFS-R |
TCP 5722 |
|
Random RPC |
TCP 49152-65535 |
4.5 SSL Certificate Requirements
Migrator Pro for Active Directory does not require HTTPS (HTTP with SSL), and can operate using HTTP. However, it is strongly recommended to implement Migrator Pro for Active Directory using HTTPS to secure communications between the devices to be migrated and the Migrator Pro for Active Directory Server. In order to activate HTTPS on the IIS component in Windows, the Migrator Pro for Active Directory system will require that a SSL certificate is present.
An SSL Certificate is not provided as part of the installation. For the most secure installation, purchasing an SSL Certificate from a Windows supported 3rd party provider is recommended.
In scenarios where this is not possible, self-signed SSL Certificate can be generated in Windows following these directions: https://technet.microsoft.com/en-us/library/cc753127(v=ws.10).aspx
If using a self-signed certificate, it should be noted that Migrator Pro for Active Directory’s agent component would utilize the operating system’s certificate trust list. Due to the security nature of Active Directory migrations, there is no method of implementing an override and forcing the agent to use an untrusted certificate. If a self-signed certificate is used, that certificate will need to be added to the trusted root certificate list for all computer objects to be migrated. This can be accomplished via group policy: https://technet.microsoft.com/en-us/library/cc738131(v=ws.10).aspx
4.6 Service Account Requirements
Migrator Pro for Active Directory requires the following user account permissions and privileges to support Active Directory migrations:
-
One service account with read/write access to all organizational units (OUs) containing user, group, and computer objects in the source Active Directory to be migrated to the target environment.
-
One service account with administrative rights on the target domain(s)
-
If administrative rights cannot be granted, the service account requires the following rights:
-
The ability to create and modify user objects in the desired OUs in the target Active Directory environment.
-
Read Permissions to the configuration container in Active Directory
-
User credentials with the delegated migrateSIDHistory extended right.
-
-
-
A service account in each source and target domain with the ability to modify computer objects and add computers to the domain.
4.7 SQL Server Reporting Services (SSRS) Account Requirements
Migrator Pro for Active Directory's Reporting feature requires credentials in the following places:
-
Content credential: Credential for accessing the report server content.
You must set the securities in two different places in the SSRS ‘Report Manager’ web interface (http://<servername>/Reports) to connect to the report server and upload reports from the installation program.
In the Site Settings, you MUST enable the ‘System Administrator’ role during installation. After installation is complete, you may change this user’s role to ‘System User’ if desired.
In the Folder Settings, you must add the same user with (at least) ‘Browser’ permission.

-
Data Source Credential: The Data Source is used to access queries in the ADM database. These credentials and roles are set in the SQL server with SSMS
The user must have public, db_reader, and db_executor roles on the ADM database.
The user must have the public role on the report server and report server temp databases.

4.8 DNS SRV Record Requirement
In each source domain, a SRV DNS record must be created to enable autodiscover for Migrator Pro for Active Directory agents.
-
To enable autodiscover when HTTPS is desired
-
Record Name: _btadm._https.SourceDomainName.Local
-
Weight and Priority: 0
-
Port Number: 443
-
-
To enable autodiscover when HTTP is desired
-
Record Name: _btadm._http.SourceDomainName.Local
-
Weight and Priority: 0
-
Port Number: 80
-
4.9 Offline Domain Join (ODJ) Requirements
In order to successfully facilitate the new Cached Credentials job (which supports the Offline Domain Join feature) a one-way external trust must be configured from the source domain to the target domain.
The devices that the ODJ process is being run on must have network connectivity to BOTH the source and target environments at the same time in order to have the Cached Credentials function work properly.
Offline domain join files must be created prior to running the Offline Domain Join process. A full explanation of Microsoft’s Djoin.exe utility and how to create these files can be found here:
https://technet.microsoft.com/en-us/library/offline-domain-join-djoin-step-by-step%28v=ws.10%29.aspx
Section 5. Requirements for Both Directory Sync Pro for Active Directory and Migrator Pro for Active Directory