Overview of data handled by On Demand Recovery
On Demand Recovery manages the following type of customer data:
- Azure Active Directory and Office 365 users, groups, conditional access policies, service principals with their properties, and device information returned by Azure Active Directory Graph API, including account name, email addresses, contact information, department, membership, and other properties.
- On Demand Recovery does not back up and does not store user passwords and password hashes.
For more information about Azure Active Directory connection information and security tokens, refer to the On Demand Core product documentation:
Admin Consent and Service Principals
On Demand Recovery requires access to the customer’s Azure Active Directory and Office 365 tenancies. The customer grants that access using the Microsoft Admin Consent process, which will create a Service Principal in the customer's Azure Active Directory with minimum consents required by On Demand Recovery (Groups and Users).
The Service Principal is created using Microsoft's OAuth certificate based client credentials grant flow https://docs.microsoft.com/en-us/azure/active-directory/develop/v2-oauth2-client-creds-grant-flow. Customers can revoke Admin Consent at any time. See https://docs.microsoft.com/en-us/azure/active-directory/manage-apps/delete-application-portal and https://docs.microsoft.com/en-us/skype-sdk/trusted-application-api/docs/tenantadminconsent for details.
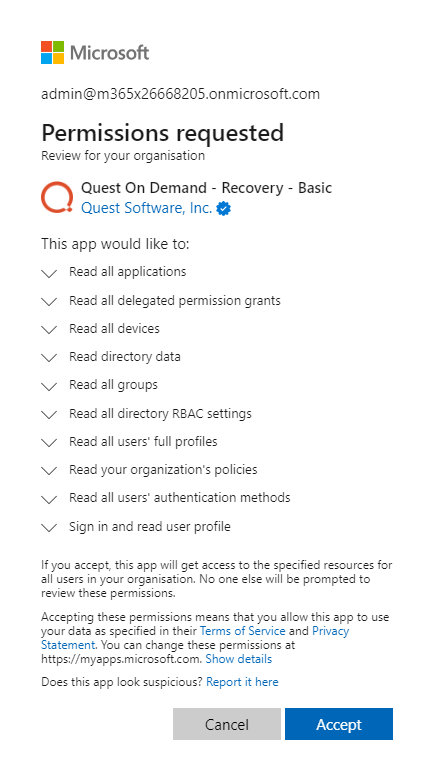
Following is the base consent required by On Demand.

In addition to the base consents required by On Demand, On Demand Recovery requires the following consents:
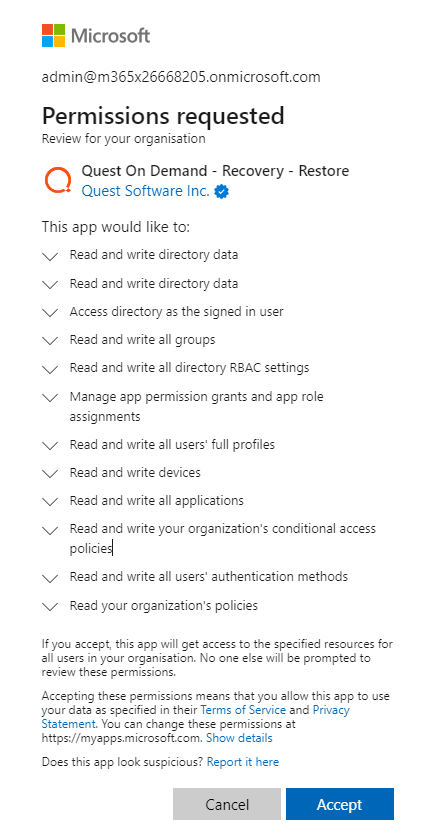
In addition to the base consents required by On Demand and On Demand Recovery, to restore Office 365 and Azure Active Directory data the following consent is required:
Exchange Online PowerShell
To perform Exchange tasks, you will need to grant consent to Exchange Online PowerShell, and assign the Exchange Admin Role. For details, please see the About admin consent status and the Granting and regranting admin consent sections in the On Demand Global Settings User Guide.
Location of customer data
The following datacenters are used to store customer data:
For US organizations
- Backups are stored in Geo-redundant Azure Blob Storage – encrypted at rest:
- Primary replica - West US 2 (Washington)
- Secondary replica - West Central US (Wyoming)
- Unpacked backups are stored on Azure virtual disks that are associated with independent Elasticsearch nodes (per customer) which are part of Azure Kubernetes Service West US 2 (Washington) - encrypted at rest
- Logs are stored in Log Analytics East US (Virginia) – encrypted at rest
- Service account credentials that are used to backup MFA settings, inactive mailboxes, conditional access policies, Gallery applications, and SSO settings data (if the corresponding option is selected) are stored in Azure Key Vault Central US (Iowa).
For Canadian organizations
- Backups are stored in Geo-redundant Azure Blob Storage – encrypted at rest
- Primary replica – Canada Central (Toronto)
- Secondary replica – Canada East (Quebec City)
- Unpacked backups are stored on Azure virtual disks that are associated with independent Elasticsearch nodes (per customer) which are part of Azure Kubernetes Service Canada Central (Toronto) – encrypted at rest
- Logs are stored in Log Analytics Canada Central (Toronto) – encrypted at rest
-
Service account credentials that are used to backup MFA settings, inactive mailboxes, conditional access policies, Gallery applications, and SSO settings data (if the corresponding option is selected) are stored in Azure Key Vault Canada Central (Toronto).
For European organizations
- Backups are stored in Geo-redundant Azure Blob Storage – encrypted at rest:
- Primary replica – North Europe (Ireland)
- Secondary replica – West Europe (Netherlands)
- Unpacked backups are stored on Azure virtual disks that are associated with independent Elasticsearch nodes (per customer) which are part of Azure Kubernetes Service North Europe (Ireland) – encrypted at rest
- Logs are stored in Log Analytics North Europe (Ireland) – encrypted at rest
- Service account credentials that are used to backup MFA settings, inactive mailboxes, conditional access policies, Gallery applications, and SSO settings data (if the corresponding option is selected) are stored in Azure Key Vault North Europe (Ireland).
For UK organizations
- Backups are stored in Geo-redundant Azure Blob Storage – encrypted at rest:
- Primary replica – UK South
- Secondary replica – UK West
- Unpacked backups are stored on Azure virtual disks that are associated with independent Elasticsearch nodes (per customer) which are part of Azure Kubernetes Service UK South – encrypted at rest
- Logs are stored in Log Analytics UK South – encrypted at rest
- Service account credentials that are used to backup MFA settings, inactive mailboxes, conditional access policies, Gallery applications, and SSO settings data (if the corresponding option is selected) are stored in Azure Key Vault UK South.
For Australian organizations
- Backups are stored in Geo-redundant Azure Blob Storage – encrypted at rest:
- Primary replica – Australia East
- Secondary replica – Australia Southeast
- Unpacked backups are stored on Azure virtual disks that are associated with independent Elasticsearch nodes (per customer) which are part of Azure Kubernetes Service Australia East – encrypted at rest
- Logs are stored in Log Analytics Australia East– encrypted at rest
- Service account credentials that are used to backup MFA settings, inactive mailboxes, conditional access policies, Gallery applications, and SSO settings data (if the corresponding option is selected) are stored in Azure Key Vault Australia East.
Other regions are supported on customer request.
Privacy and protection of customer data
The most sensitive customer data collected and stored by On Demand Recovery is the Azure Active Directory and Office 365 data including users, groups, service principals, conditional access policies, devices and their associated properties. All properties which are available in Microsoft Azure AD Graph API and MSOnline – such as users email, work title, department, phone number, address and others – are stored in the backup. On Demand Recovery does not back up and does not store user passwords and password hashes.
The backup data for each customer is stored in a separate Azure Blob Container. This information is protected through the Azure built in data at rest Server-Side encryption mechanism. It uses the strongest FIPS 140-2 approved block cipher available, Advanced Encryption Standard (AES) algorithm, with a 256-bit key.
Geo-redundant storage is used which means that backup data is replicated to a secondary region that is hundreds of miles away from the primary region. Backup data is durable even in the case of a complete regional outage or a disaster in which the primary region is not recoverable.
Service account credentials that are used to backup MFA settings and conditional access policies (if the corresponding option is selected) and security tokens are stored in Microsoft Azure Key Vault. For details about encryption within Azure Key Vault, see the Privacy and Protection of Customer Data section in the Quest On Demand Core Security Guide.
For more information about Azure Blob Storage, see the following links:



