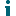Adding credentials for Office 365 ingest account in Credential Editor
If you want to add/change credentials for Office 365 ingest account, you must be logged in as the local service account under which the Services (particularly Office 365 module) runs. Use the Archive Shuttle Credentials Editor for adding/changing of the credentials for Office 365 ingest account.
The tool is called ArchiveShuttle.Module.CredentialsEditor.exe and is by default located in: C:\Program Files (x86)\QUADROtech\Archive Shuttle Modules\CredentialsEditor\.
Then, follow these steps:
1.Run the tool, click Add and specify the valid UPN account and the valid password. Then, click OK and save the credentials.
2.Restart the module.
At least one service account is required per import module. One service account needs to have configured Global Administrator rights and rest of the accounts should have Application Impersonation rights configured.
|
|
NOTES: ·When ingest accounts are not visible in the Health page, you have to restart the Office 365 module service first and then Core service to have accounts from Credential Editor loaded to that page. ·Service accounts must be unique and cannot repeat across additional module instances. |
OAuth support for GCC and GCC High tenants
You may experience an issue where it is claimed that OAuth is not supported with GCC and GCC High tenants. This issue can be resolved using the Credentials Editor.
1.Go the the Credentials Editor, then the Office 365 Auth tab.
2.Click Edit.
3.On the Azure cloud drop down list, select:
a.AzureCloud for GCC tenants
b.AzureUSGovernment for GCC High tenants.
4.Click OK.
Using Microsoft Graph
Use of Microsoft Graph is enabled automatically from Archive Shuttle 11.0.
If using Microsoft Graph, ensure that the Microsoft Entra ID App Registration section has been filled in the Credentials Editor, regardless if OAuth is being used. If Azure App Registration is left empty, an error will occur.
Microsoft Graph commands and permissions
One of the following permissions is required to call this API. To learn more, including how to choose permissions, see Permissions.
|
Permission type |
Permissions (from least to most privileged) |
|---|---|
|
Delegated (work or school account) |
User.ReadBasic.All, User.Read.All, Directory.Read.All |
|
Application |
User.Read.All, Directory.Read.All |
One of the following permissions is required to call this API. To learn more, including how to choose permissions, see Permissions.
|
Permission type |
Permissions (from least to most privileged) |
|---|---|
|
Delegated (work or school account) |
User.Read, User.ReadBasic.All, User.Read.All, Directory.Read.All |
|
Application |
User.Read.All, Directory.Read.All |
One of the following permissions is required to call this API. To learn more, including how to choose permissions, see Permissions.
|
Permission type |
Permissions (from least to most privileged) |
|---|---|
|
Delegated (work or school account) |
Organization.Read.All, Directory.Read.All |
|
Application |
Organization.Read.All, Directory.Read.All |
One of the following permissions is required to call this API. To learn more, including how to choose permissions, see Permissions.
|
Permission type |
Permissions (from least to most privileged) |
|---|---|
|
Delegated (work or school account) |
User.ReadWrite.All, Directory.ReadWrite.All |
|
Application |
User.ReadWrite.All, Directory.ReadWrite.All |
One of the following permissions is required to call this API. To learn more, including how to choose permissions, see Permissions.
|
Permission type |
Permissions (from least to most privileged) |
|---|---|
|
Delegated (work or school account) |
User.ReadWrite, User.ReadWrite.All, User.ManageIdentities.All, Directory.ReadWrite.All |
|
Application |
User.ReadWrite.All, User.ManageIdentities.All, Directory.ReadWrite.All |
One of the following permissions is required to call this API. To learn more, including how to choose permissions, see Permissions.
|
Permission type |
Permissions (from least to most privileged) |
|---|---|
|
Delegated (work or school account) |
User.ReadWrite.All |
|
Application |
User.ReadWrite.All |
One of the following permissions is required to call this API. To learn more, including how to choose permissions, see Permissions.
For applications:
|
Permission type |
Permissions (from least to most privileged) |
|---|---|
|
Delegated (work or school account) |
Application.ReadWrite.All, Directory.ReadWrite.All |
|
Application |
Application.ReadWrite.OwnedBy, Application.ReadWrite.All |
The requester needs to have one of the following roles: Global Administrator or Application Administrator.
For users:
|
Permission type |
Permissions (from least to most privileged) |
|---|---|
|
Delegated (work or school account) |
User.ReadWrite.All |
|
Application |
Not supported. |
The signed-in user needs to have one of the following roles: Global Administrator or User Administrator.
For groups:
|
Permission type |
Permissions (from least to most privileged) |
|---|---|
|
Delegated (work or school account) |
Group.ReadWrite.All |
|
Application |
Not supported. |
The requester needs to have one of the following roles: Global Administrator or Groups Administrator.
Global Administrator consent for app-only permissions
Any app-only permission requires a global administrator of the directory to give consent to the application. Select one of the following options, depending on the role:
Global tenant administrator
For a global tenant administrator:
1.Go to Enterprise applications in the Azure portal
2.Select the app registration, and select Permissions from the Security section of the left pane.
3.Select the button labeled Grant admin consent for {Tenant Name} (where {Tenant Name} is the name of the directory)
Standard user
For a standard user of your tenant, ask a global administrator to grant admin consent to the application. To do this, provide the following URL to the administrator:
In the URL:
·Replace Enter_the_Tenant_Id_Here with the tenant ID or tenant name (for example, contoso.microsoft.com)
·Enter_the_Application_Id_Here is the application (client) ID for the registered application
|
|
NOTE: The error 'AADSTS50011: No reply address is registered for the application' may be displayed after you grant consent to the app by using the preceding URL. This error occurs because the application and the URL do not have a redirect URI. This can be ignored. |