Agent Management view
|
1 |
At the top of the Agent Management view, click Active Directory, and then click Add to launch the Agent Setup wizard. |
|
2 |
On the Prepare page, carefully read the instructions about the steps that you need to take before proceeding with the wizard. |
|
3 |
On the Auto-Discovery or Manual page, indicate if you want to manually configure an Active Directory agent to monitor a single Domain Controller, or search your domain and auto-discover Domain Controllers via LDAP. Click Next. |
|
• |
|
• |
|
4 |
On the Select the Search Domain page, specify the domain to search for Domain Controllers, where Active Directory agent instances are to be created and activated. |
|
• |
Domain: Type the fully qualified name (myDomain.com) of a domain to search for Domain Controllers (DCs). |
|
• |
User Name: Type the user principal name of the account to be used to query Active Directory® on the selected domain.The following formats are accepted for the user principal name: myUser@myDomain.com, myUser, and myDomain.com\myUser. |
|
• |
Password: Enter the password associated with the above user account. |
|
• |
Enable SSL For LDAP: Selecting this check box if security LDAP is required. |
|
NOTE: 1. When selecting Enable SSL For LDAP, import the root certificate of the monitoring domain into both FglAM and Foglight keystore. 2. Ensure that the Subject Alternative Name of the certificate used by LDAP service includes both server FQDN and Domain name. For detailed information on how to import certificate into both FMS and FglAM keystore in FIPS-compliant mode, refer to Managing certificates for FglAM and Managing certificates for FMS in FIPS-compliant mode . For detailed information on how to import certificate into both FMS and FglAM keystore in non-FIPS mode, refer to Managing certificates for FglAM and Managing certificates for FMS in non-FIPS mode . |
|
5 |
On the Select Servers page, select one or more DCs that you want to monitor. |
|
• |
Domain Controller: Displays the name of the DCs found on the selected domain. |
|
• |
Active Directory Agent Exists: Indicates whether an Active Directory agent instance has already been created for a DC. A green check mark in this check box indicates that an agent instance has already been created for the DC. DCs already monitored by other Active Directory agents are unavailable for selection in the list. |
|
6 |
On the Configure Agent Properties page, review the Active Directory agent properties, and edit them, as necessary. select the agent properties, as necessary. |
|
• |
Domain Controller(s): The name of the domain controller found on the selected domain. |
|
• |
Communication Protocol: Selects to run the WMI query through DCOM or WinRM. |
|
• |
WinRM Port: The WinRM port number on the monitored Domain Controller. This property only appears if the Communication Protocol is set to WinRM through HTTP or WinRM through HTTPS. |
|
NOTE: 1. When setting Communication Protocol as WinRM through HTTPs, import the root certificate of the monitoring domain into FglAM keystore. 2. Ensure that the Subject Alternative Name of the certificate used by LDAP service includes both server FQDN and Domain name. For detailed information on how to import certificate into FglAM keystore, refer to Managing certificates for FglAM . |
|
• |
LDAP Authentication Mechanism: The authentication scheme used to connect to the LDAP server: Simple (default) or Kerberos. |
|
• |
Enable SSL For LDAP: Indicates if the LDAP connection is secure or not (default). |
|
NOTE: 1. When selecting Enable SSL For LDAP, import the root certificate of the monitoring domain into both FglAM and Foglight keystore. 2. Ensure that the Subject Alternative Name of the certificate used by LDAP service includes both server FQDN and Domain name. For detailed information on how to import certificate into both FMS and FglAM keystore in FIPS-compliant mode, refer to Managing certificates for FglAM and Managing certificates for FMS in FIPS-compliant mode . For detailed information on how to import certificate into both FMS and FglAM keystore in non-FIPS mode, refer to Managing certificates for FglAM and Managing certificates for FMS in non-FIPS mode . |
|
• |
Is a Virtual Host?: Indicates if the selected Domain Controller runs on a virtual host. |
|
• |
Virtual Environment: The type of the virtual environment: VMware or Hyper-V. This property only appears if the selected Domain Controller runs on a virtual host. |
|
7 |
On the Select the Agent Manager Host page, select the Foglight Agent Manager Host to be used for the new Active Directory agent instances. |
|
• |
|
• |
The Active Directory Agent Package Deployed column indicates whether the Active Directory agent package has been deployed to the Foglight Agent Manager host(s). A green check in this column indicates that the Active Directory agent package has been deployed. |
|
• |
The Windows Agent Package Deployed column indicates whether the Windows agent package is already deployed to the Agent Manager host(s). A green check in this column indicates that the Windows agent package has been deployed. This column is displayed only if the selected Domain Controller runs on a physical host. |
|
8 |
On the Assign and Validate Credentials page, review the available credentials, and edit them, as necessary. |
|
• |
To create a new credential, click Add host(s) to a new credential. |
|
• |
In the Create New Credential and Assign dialog box, create a credential that you want to use to access the monitored resource. Type a new credential name, domain, user name, password, and lockbox, and click Submit. |
|
• |
To select an existing credential, click Add host(s) to an existing credential. |
|
• |
|
• |
To bypass the prerequisites verification, select the Do not check for prerequisites check box. |
|
9 |
On the Summary page, review the configuration settings chosen for the new agent, and its prerequisite diagnostics, including: |
|
• |
Active Directory Agent: The name of the selected Active Directory agent instance. |
|
• |
Windows Agent: The name of the selected Windows agent instance. |
|
• |
Success: The agent instance can connect to the monitored Domain Controller and collect data. |
|
• |
Error: The agent instance cannot connect to the monitored Domain Controller instance and collect data. Click this link to find out what causes this error. Carefully review the information in the popup that appears in order address the problem. |
|
|
1 |
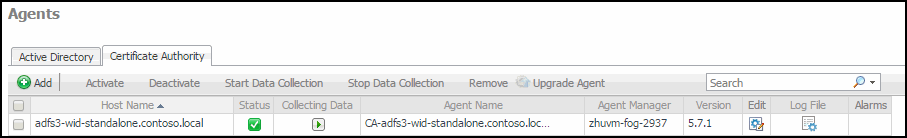
At the top of the Agent Management view, click Certificate Authority, and then click Add to launch the Agent Setup wizard. |
|
2 |
On the Configure CA Agent Properties page, specify the host where Certificate Authority agent instances are to be created and activated. |
|
• |
Host Name: Type the fully qualified name of a Certificate Authority server. |
|
• |
Communication Protocol: Selects to run the WMI query through DCOM or WinRM. |
|
• |
WinRM Port: The WinRM port number on the monitored Host. This property only appears if the Communication Protocol is set to WinRM through HTTP or WinRM through HTTPS. |
|
NOTE: 1. When setting Communication Protocol as WinRM through HTTPs, import the root certificate of the monitoring domain into FglAM keystore. 2. Ensure that the Subject Alternative Name of the certificate used by LDAP service includes both server FQDN and Domain name. For detailed information on how to import certificate into FglAM keystore, refer to Managing certificates for FglAM . |
|
3 |
On the Select the Agent Manager Host page, select the Foglight Agent Manager Host to be used for the new Certificate Authority agent instances. |
|
• |
|
• |
The Certificate Authority Agent Package Deployed column indicates whether the Certificate Authority agent package has been deployed to the Foglight Agent Manager host(s). A green check in this column indicates that the Certificate Authority agent package has been deployed. |
|
4 |
On the Assign and Validate Credentials page, review the available credentials, and edit them, as necessary. |
|
• |
To create a new credential, click Add host(s) to a new credential. |
|
• |
In the Create New Credential dialog box, create a credential that you want to use to access the monitored resource. Type a new credential name, domain, user name, password, and lockbox, and click Submit. |
|
• |
To select an existing credential, click Add host(s) to an existing credential. |
|
• |
|
5 |
On the CA Summary page, review the configuration settings chosen for the new agent, and its prerequisite diagnostics, including: |
|
• |
Host Name: The name of the selected Certificate Authority agent instance. |
|
• |
Communication Protocol: The communication protocol selected to run the WMI query. |
|
• |
WinRM Port: The WinRM port number on the monitored Host. This property only appears if the Communication Protocol is set to WinRM through HTTP or WinRM through HTTPS. |
|
• |
Agent Manager: The name of the selected Foglight Agent Manager Host to be used for the new Certificate Authority agent instances. |
The Agent Setup wizard closes. The Certificate Authority agent is now added and configured, and appears in the Agent Management view, on the Administration > Certificate Authority tab.
The Agent Edit wizard guides you through the process of editing private agent properties.
|
1 |
|
2 |
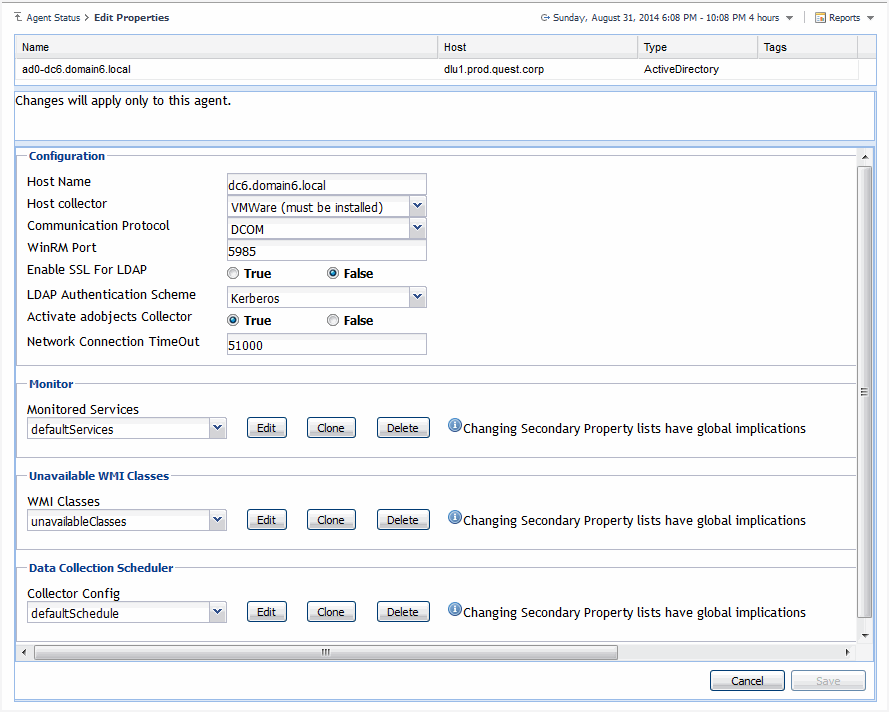
In the Agent Edit wizard, on the Configure Agent Properties page, review the Active Directory agent properties, and edit them, as necessary. |
|
• |
Domain Controller(s): The name of the domain controller found on the selected domain. |
|
• |
Communication Protocol: Selects to run the WMI query through DCOM or WinRM. |
|
• |
WinRM Port: The WinRM port number on the monitored Domain Controller. This property only appears if the Communication Protocol is set to WinRM through HTTP or WinRM through HTTPS. |
|
NOTE: 1. When setting Communication Protocol as WinRM through HTTPs, import the root certificate of the monitoring domain into FglAM keystore. 2. Ensure that the Subject Alternative Name of the certificate used by LDAP service includes both server FQDN and Domain name. For detailed information on how to import certificate into FglAM keystore, refer to Managing certificates for FglAM . |
|
• |
LDAP Authentication Mechanism: The authentication scheme used to connect to the LDAP server: Simple (default) or Kerberos. |
|
• |
Enable SSL For LDAP: Indicates if the LDAP connection is secure or not (default). |
|
NOTE: 1. When selecting Enable SSL For LDAP, import the root certificate of the monitoring domain into both FglAM and Foglight keystore. 2. Ensure that the Subject Alternative Name of the certificate used by LDAP service includes both server FQDN and Domain name. For detailed information on how to import certificate into both FMS and FglAM keystore in FIPS-compliant mode, refer to Managing certificates for FglAM and Managing certificates for FMS in FIPS-compliant mode . For detailed information on how to import certificate into both FMS and FglAM keystore in non-FIPS mode, refer to Managing certificates for FglAM and Managing certificates for FMS in non-FIPS mode . |
|
• |
Is a Virtual Host?: Indicates if the selected Domain Controller runs on a virtual host. |
|
• |
Virtual Environment: The type of the virtual environment: VMware or Hyper-V. This property only appears if the selected Domain Controller runs on a virtual host. |
|
• |
Host Info Provider: Indicates the host metrics collected by the Windows agent or the Active Directory agent. |
|
3 |
On the Assign and Validate Credentials page, review the available credentials, and edit them, as necessary. |
|
• |
To create a new credential, click Add host(s) to a new credential. |
|
• |
In the Create New Credential and Assign dialog box, create a credential that you want to use to access the monitored resource. Type a new credential name, domain, user name, password, and lockbox, and click Submit. |
|
• |
To select an existing credential, click Add host(s) to an existing credential. |
|
• |
|
4 |
The Agent Edit wizard guides you through the process of editing CA agent properties.
|
1 |
In the Agent Management > Certificate Authority view, in the row containing the agent whose properties you want to edit, click the Edit column. |
|
2 |
In the Agent Edit wizard, on the Configure CA Agent Properties page, review the Certificate Authority agent properties, and edit them, as necessary. |
|
• |
Host Name: Type the fully qualified name of a Certificate Authority server. |
|
• |
Communication Protocol: Selects to run the WMI query through DCOM or WinRM. |
|
• |
WinRM Port: The WinRM port number on the monitored Host. This property only appears if the Communication Protocol is set to WinRM through HTTP or WinRM through HTTPS. |
|
NOTE: 1. When setting Communication Protocol as WinRM through HTTPs, import the root certificate of the monitoring domain into FglAM keystore. 2. Ensure that the Subject Alternative Name of the certificate used by LDAP service includes both server FQDN and Domain name. For detailed information on how to import certificate into FglAM keystore, refer to Managing certificates for FglAM . |
|
3 |
On the Assign and Validate Credentials page, review the available credentials, and edit them, as necessary. |
|
• |
To create a new credential, click Add host(s) to a new credential. |
|
• |
In the Create New Credential dialog box, create a credential that you want to use to access the monitored resource. Type a new credential name, domain, user name, password, and lockbox, and click Submit. |
|
• |
To select an existing credential, click Add host(s) to an existing credential. |
|
• |
|
4 |
On the CA Summary page, review the configuration settings chosen for the new agent, and its prerequisite diagnostics, including: |
|
• |
Host Name: The name of the selected Certificate Authority agent instance. |
|
• |
Communication Protocol: The communication protocol selected to run the WMI query. |
|
• |
WinRM Port: The WinRM port number on the monitored Host. This property only appears if the Communication Protocol is set to WinRM through HTTP or WinRM through HTTPS. |
|
• |
Agent Manager: The name of the selected Foglight Agent Manager Host to be used for the new Certificate Authority agent instances. |
The Agent Edit wizard closes. The Certificate Authority agent is updated automatically in the Agent Management view, on the Administration > Certificate Authority tab.
If any monitoring agents are unable to collect data or connect to the monitored Domain Controllers, you can inspect the underlying cause using the Prerequisites Diagnostic button on the Agent Management toolbar.
|
1 |
In the Agent Management view, select the row containing the agent whose prerequisites you want to examine, and click Prerequisites Diagnostic on the toolbar. |
|
2 |
Review the results in the Prerequisites Diagnostic dialog box. |
|
• |
Agent Name: The name of the selected Active Directory agent instance. |
|
• |
Monitored Host: The name of the host on which the monitored Domain Controller is running. |
|
• |
Success: The agent instance can connect to the monitored Domain Controller and collect data. |
|
• |
Error: The agent instance cannot connect to the monitored Domain Controller and collect data. Click this link to find out what causes this error. Carefully review the information in the popup that appears in order address the problem. |
Managing certificates
|
• |
<foglight_home> is a placeholder that represents the path to the Foglight Management Server installation. |
|
• |
<foglight_agent_mgr_home> is a placeholder that represents the path to the Foglight Agent Manager installation. This can be the location of the Foglight Agent Manager installation on a monitored host, or the home directory of the Foglight Agent Manager that comes embedded with the Foglight Management Server. For example: |
All the certificate-related command line options require that FglAM be up and running.
bin/fglam --add-certificate "user alias 1"=/path/to/certificate/file
|
• |
FglAM requires the Base64 format. To verify if the certificate file is encoded with Base64, open the certificate with a notepad and the certificate should be similar to the following example: -----BEGIN CERTIFICATE----- XXXXXXXX= -----END CERTIFICATE----- |
|
NOTE: If the certificate is not Base64 format, use openssl command to convert the certificate file into a Base64 file. Use either of the following commands depending on the source form: openssl x509 -inform DER -in xxx.cer -out xxx.crt or openssl x509 -inform PEM -in xxx.cer -out xxx.crt |
|
• |
The alias is required and is used in the list and delete operations to refer to the certificate. It can be anything. |
Print out a list of certificates and the aliases that refer to them.
Refer to the example output below:
Remove a certificate referred to by an alias.
bin/fglam --delete-certificate "user alias 1"
Use the keytool utility shipped with Foglight to create, import, or export certificates. This utility can be found at: <foglight_home>\jre\bin\keytool.
There are two FMS running modes:
The KeyStore Foglight used under non-FIPS mode is located at: <foglight_home>/jre/lib/security/cacerts (default password: changeit)
Use the keytool command in FMS JRE located in <foglight>/jre/bin
|
• |
<alias>: The alias is required and is used in the list and delete operations to refer to the certificate. It can be anything. |
|
• |
<foglight_home>: The folder path where the Foglight is installed. |
|
• |
<certificate path>: Your custom certificate path. |
keytool -list -keystore <foglight_home>/jre/lib/security/cacerts -storepass changeit
Remove a certificate referred to by an alias.
The KeyStore Foglight used in FIPS-compliant mode is located at: <foglight_home>/config/security/trust.fips.keystore (default password: nitrogen)
Use the keytool command in FMS JRE located in <foglight>/jre/bin.
|
• |
<alias>: The alias is required and is used in the list and delete operations to refer to the certificate. It can be anything. |
|
• |
<Foglight_home>: The folder path where Foglight is installed. |
|
• |
<certificate path>: Your custom certificate path. |
Prints out a list of certificates and the aliases that refer to them.
Refer to the example output below:
Remove a certificate referred to by an alias.
Issuer: CN=CA, DC=ca, DC=local
Valid from: Sun Jan 06 23:07:06 CST 2019 until: Wed Apr 06 23:07:06 CST 2022
Trust this certificate? [no]: yes
Certificate was added to keystore
Active Directory agent properties
To display an agent’s properties page, use one of the following methods:
|
• |
From the navigation panel, navigate to Dashboards > Administration > Agents > Agent Properties. On the Agent Properties dashboard, select an agent. The Properties panel is displayed, showing the current properties for the selected agent instance. |
|
• |
From the navigation panel, navigate to Dashboards > Administration > Agents > Agent Status. On the Agent Status dashboard, select an agent from the list and click Edit > Edit Properties. The Agent Status dashboard refreshes, showing the current properties for the selected agent instance. |
For more information on using the Agent Status dashboard to edit agent properties, see the Foglight Administration and Configuration Help.
The following tables describe the properties that can be modified for either an individual or all Active Directory agent instances, by clicking Modify the private properties for this agent or Modify the properties of all ActiveDirectory agents links, respectively.
For additional information, see these topics:
|
• |
Configuration
|
The fully qualified domain name (myServer.myDomain.com) of the target server from which data is to be collected. | ||||||||||
|
Select the host collector to be used to collect host metrics:
| ||||||||||
|
Selects to run the WMI query through DCOM, WinRM Through HTTP, or WinRM Through HTTPS. | ||||||||||
|
Supports both Basic and Kerberos authentication schemes, when connected to LDAP server. | ||||||||||
|
Turns on/ off the adobjects (user count, groups count, computer count) collection. In one domain, it only needs one agent to collect such information. | ||||||||||