The Software Inventory - Summary Page report reports on data collected from computers logging onto the network. The report details each computer's installed software. The report includes graphical representation of the software installed on computers reported on and the number of installations for each application. It is followed by the software details for each computer.
The Software Inventory report prompts the user for the Scanned Since, Computer Name and Virtual Machine type.
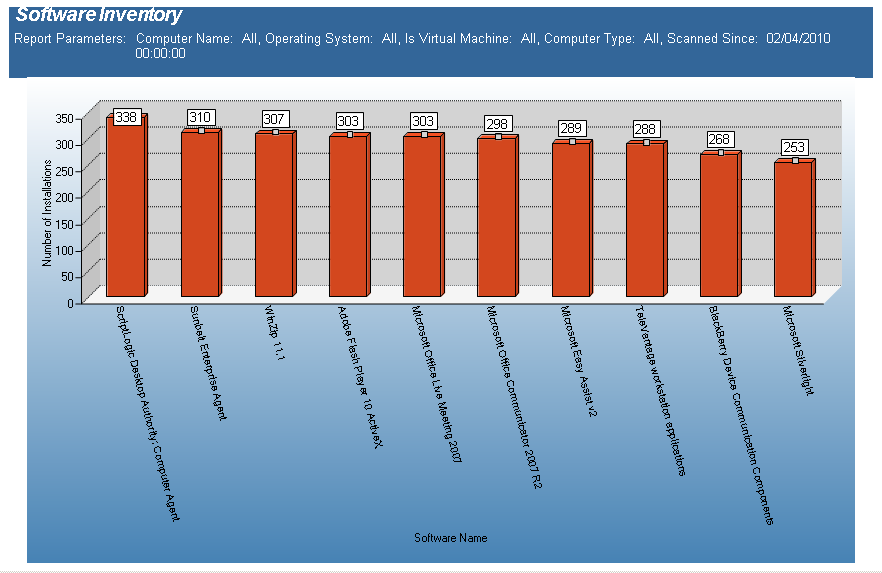
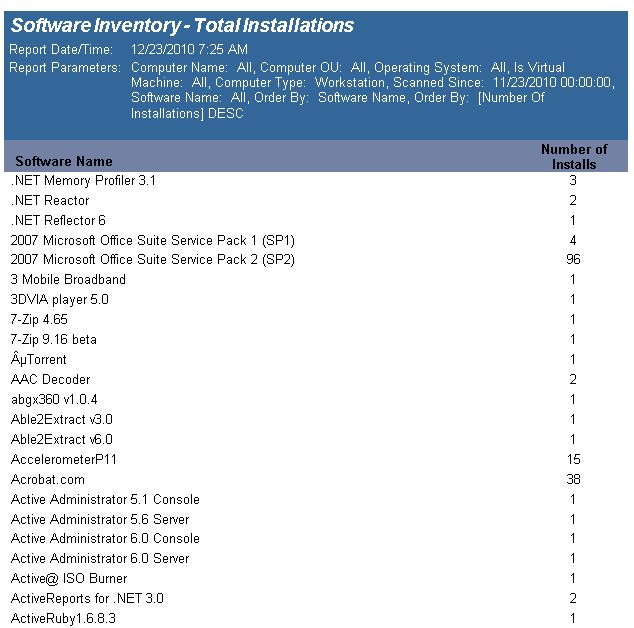
The Software Inventory - Total Installations report reports on data collected regarding installed applications. The report counts the various applications on each desktop based on collected data.
The Software Inventory - Total Installations report prompts the user for the Report Date to include Computer Name, Computer OU, Virtual Machine type, Scanned Since and Software Name.
This report is ordered by Software Name and Number of Installations in descending order.
The Software Inventory - Total Installations with Computer List report reports on data collected from computers logging onto the network. The report details each computer's installed software, sorted by Software Name..
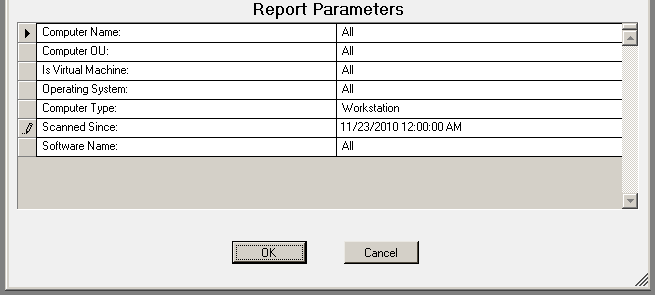
The Software Inventory report prompts the user for the Computer Name, Computer OU, Virtual Machine type, Scanned Since and Software Name.
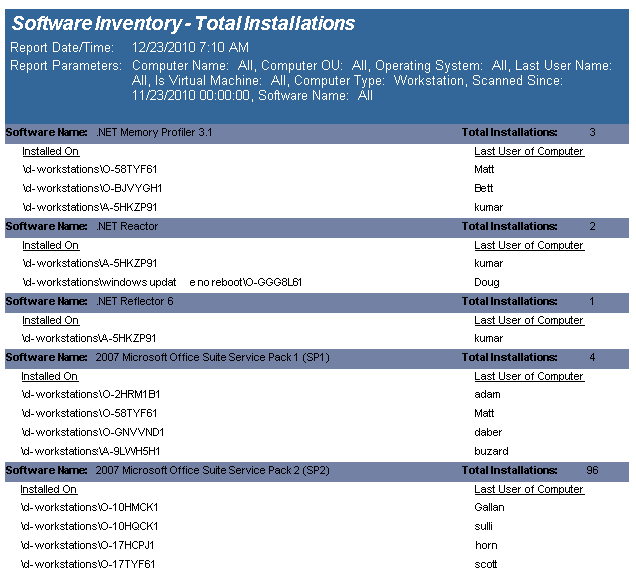
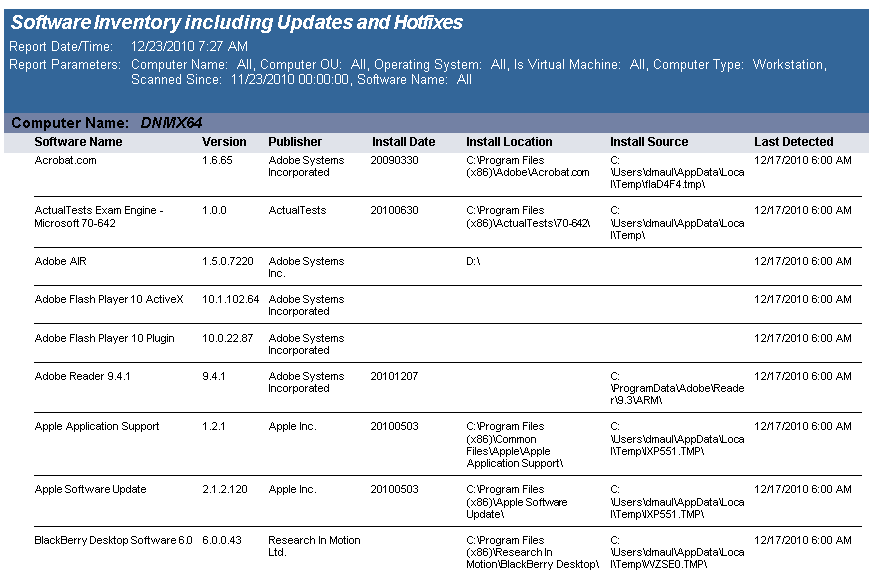
The Software Inventory including Hotfixes and Updates) report reports on data collected from computers logging onto the network. The report details each computer's installed software.
The Software Inventory report prompts the user for the Computer Name, Computer OU, Virtual Machine type, Scanned Since and Software Name.
The Software Inventory with Last User (includes Updated) report reports on data collected from computers logging onto the network. The report details each computer's installed software.
The Software Inventory report prompts the user for the Computer Name, Computer OU, Virtual Machine type, Scanned Since date and Software Name.
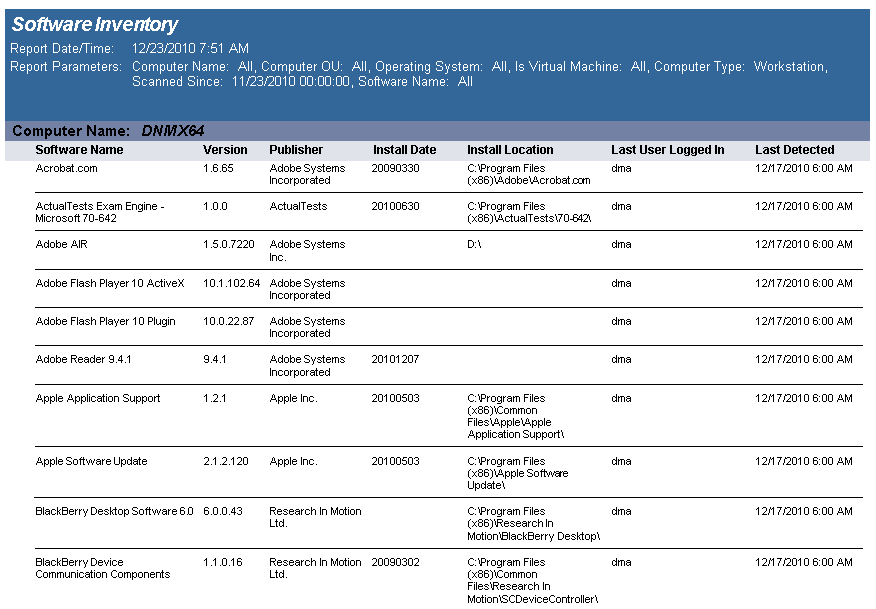
The Software Inventory with Last User report reports on data collected from computers logging onto the network. The report details each computer's installed software.
The Software Inventory report prompts the user for the Computer Name, Computer OU, Virtual Machine type, Scanned Since date, and Software Name.

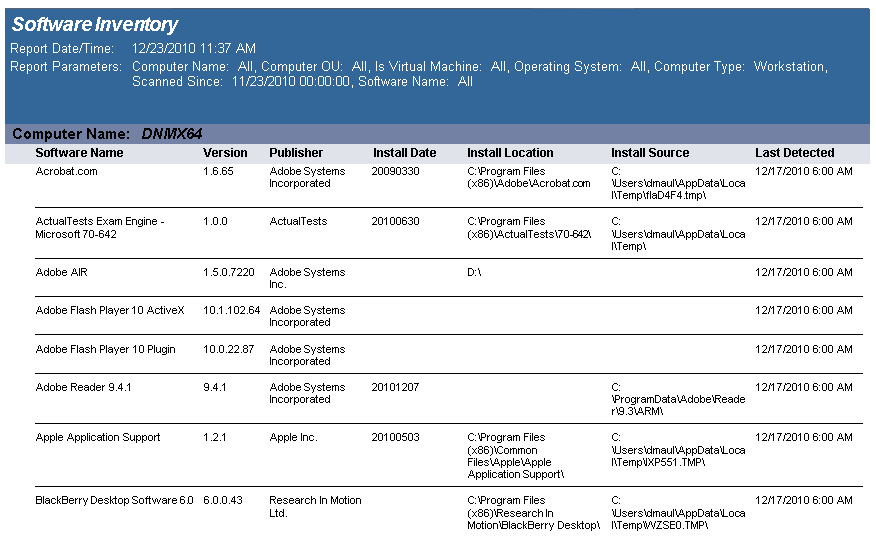
The Software Inventory report reports on data collected from computers logging onto the network. The report details each computer's installed software.
The Software Inventory report prompts the user for the Computer Name, Computer OU, Virtual Machine type, Scanned Since date, and Software Name.
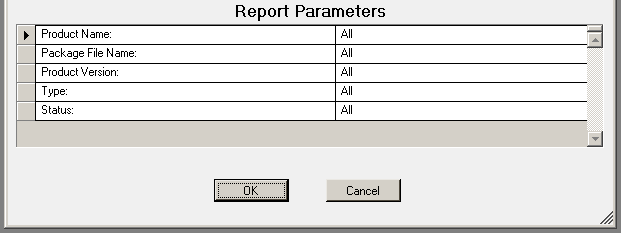
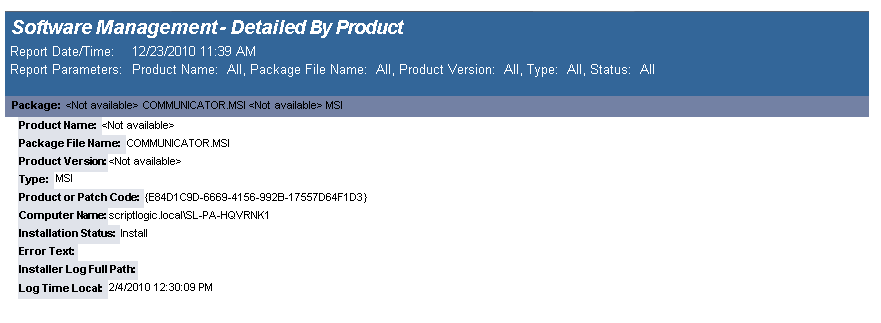
The Software Management - Detailed By Product report details the packages that have been deployed by a Software Management configuration element.
The Software Management - Summary report lists the software packages deployed by a Software Management configuration element.
The USB-Port Security - All Device Events report reports on data collected about the following device events: Plugin/Powerup, Unplug/Disable, Device Disabled, Device Enabled, Read and Write Denied and Read and Write Allowed. Filenames will be reported on all read and write events to a removable storage device.
The USB-Port Security - All Device Events report prompts the user for the Event type, Virtual Machine type, Computer type and Scanned Since date to report on.
This report is ordered by Log Time.
The USB-Port Security - All USB Devices report reports on data collected about all USB devices used on the network and are within the report parameters.
The USB-Port Security - All USB Devices report prompts the user for a Product Name, Virtual Machine, Computer Type and Logged Since date to report on.


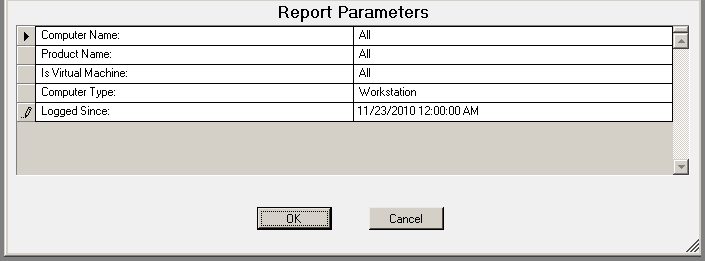
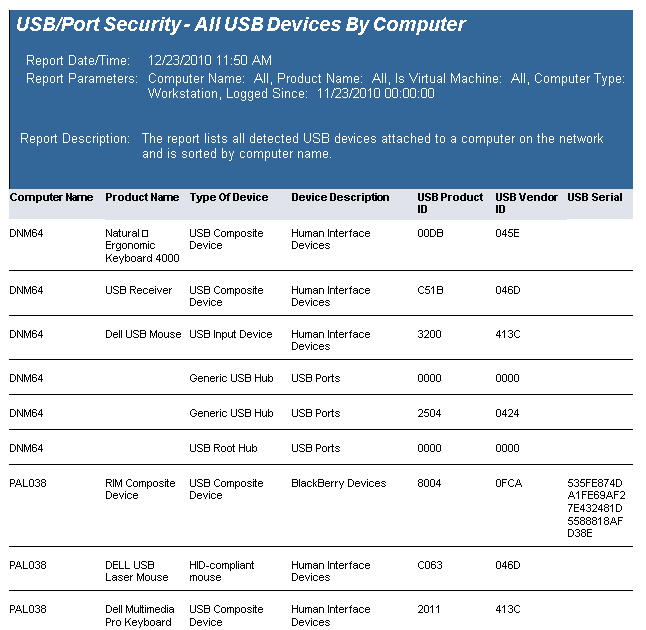
The USB-Port Security - All USB Devices by Computer report reports on data collected about all USB devices used on the network and are within the report parameters.
The USB-Port Security - All USB Devices by Computer report prompts the user for a Computer Name, Product Name, Virtual Machine, Computer Type and Logged Since date to report on.
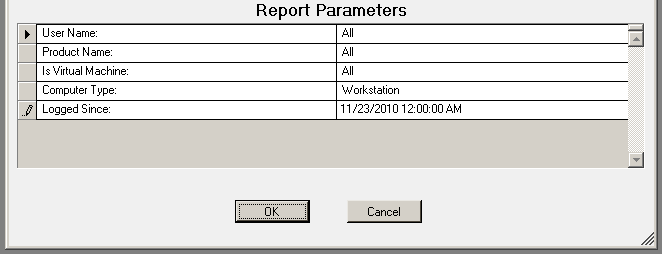
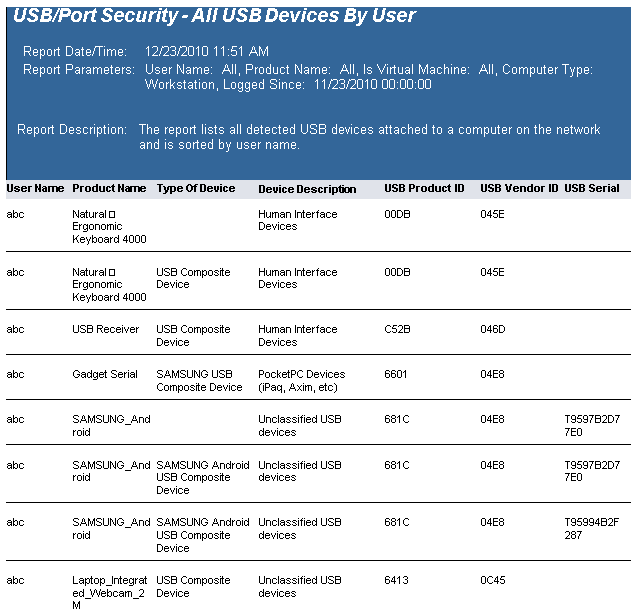
The USB-Port Security - All USB Devices by User report reports on data collected about all USB devices used on the network and are within the report parameters.
The USB-Port Security - All USB Devices by User report prompts the user for a User Name, Product Name, Virtual Machine, Computer Type and Logged Since date to report on.
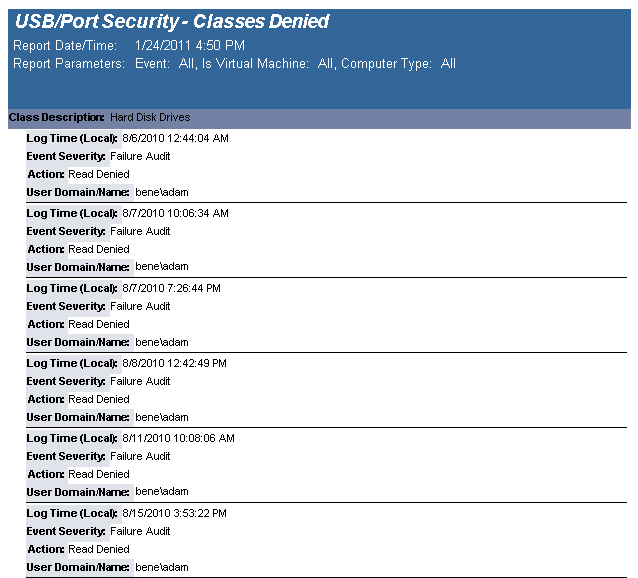
The USB-Port Security - Classes Denied report reports on data collected about denied and disabled device events per class of device. Device classes include Blackberry, Bluetooth, CD/DVD, Firewire, Floppy Disks, Hard Disk Drives, Infrared ports, IoMega devices, MP3 Players, Modems, PCMCIA controllers, Palm OS Devices, Parallel ports, Pocket PC devices, Removable storage devices, Serial ports, USB storage and WiFi devices.
The USB-Port Security - Classes Denied report prompts the user for the Scanned Since date to report on. The report can also be run for All machines, Virtual Machines only or Non-virtual Machines only.
This report is grouped by Class and sorted by Device Description.
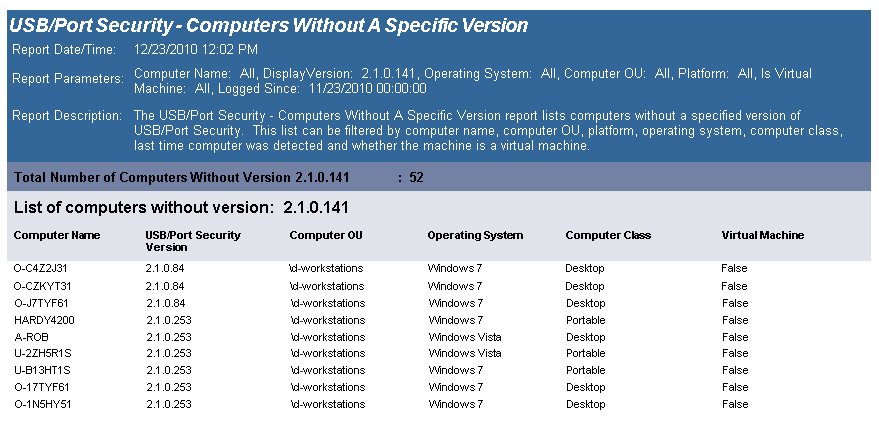
The USB-Port Security Computers Without A Specific Version report lists all computers without the specified version of the USB/Port Security client. Included in the report is the current version of the USB/Port Security that is installed on the client among other information about the computer.

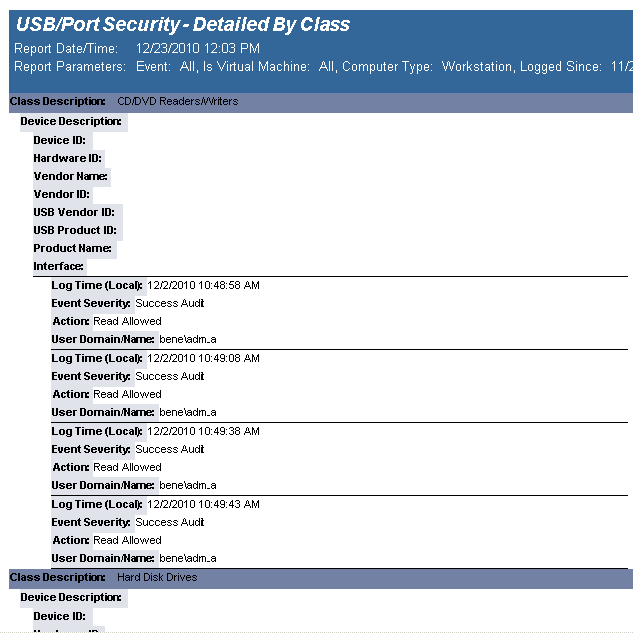
The USB-Port Security - Detailed by Class report reports on data collected about each class of devices. Device classes include Blackberry, Bluetooth, CD/DVD, Firewire, Floppy Disks, Hard Disk Drives, Infrared ports, IoMega devices, MP3 Players, Modems, PCMCIA controllers, Palm OS Devices, Parallel ports, Pocket PC devices, Removable storage devices, Serial ports, USB storage and WiFi devices.
The USB-Port Security - Detailed by Class report prompts the user for the Scanned Since date to report on. The report can also be run for All machines, Virtual Machines only or Non-virtual Machines only.
This report is grouped by Class and sorted by Device Description.
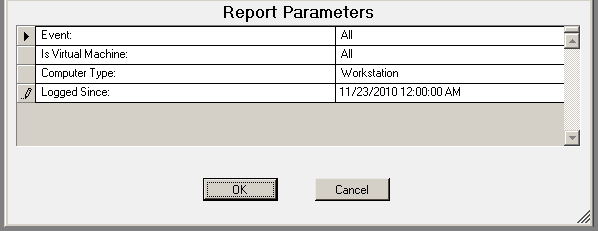
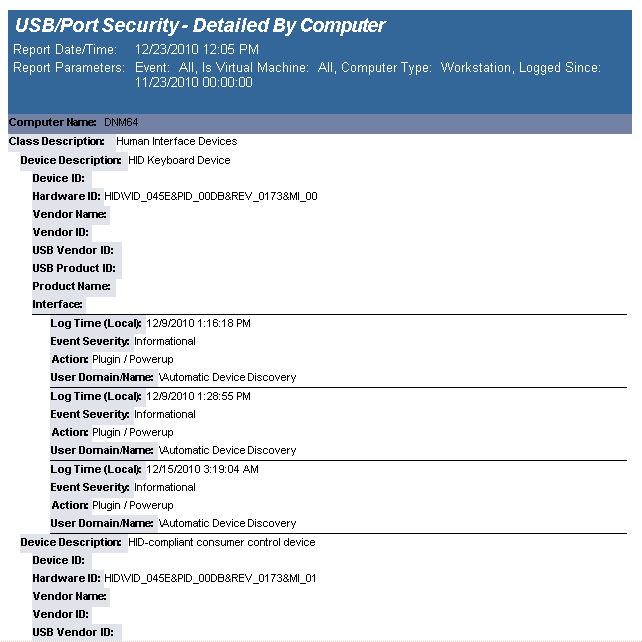
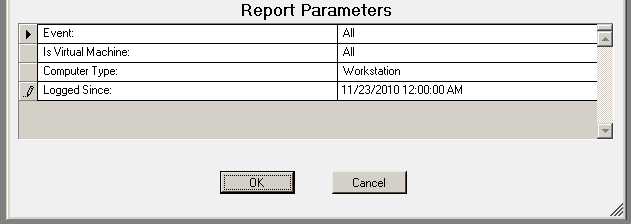
The USB-Port Security - Detailed by Computer report reports on data collected about each class of devices. Device classes include Blackberry, Bluetooth, CD/DVD, Firewire, Floppy Disks, Hard Disk Drives, Infrared ports, IoMega devices, MP3 Players, Modems, PCMCIA controllers, Palm OS Devices, Parallel ports, Pocket PC devices, Removable storage devices, Serial ports, USB storage and WiFi devices.
The USB-Port Security - Detailed by Computer report prompts the user for the Scanned Since date to report on. The report can also be run for All machines, Virtual Machines only or Non-virtual Machines only.
This report is grouped by Computer Name and Class and sorted by Device Description.
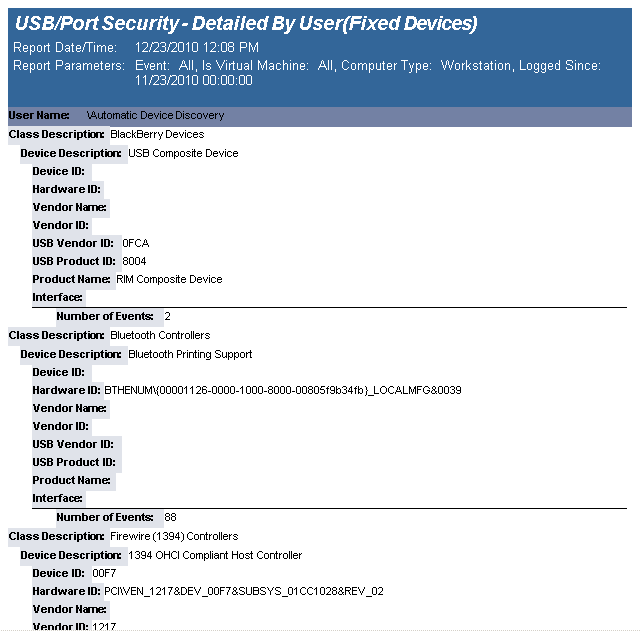
The USB-Port Security - Detailed by User (Fixed Devices) report reports on data collected about all Fixed device classes.
The USB-Port Security - Detailed by User(Fixed Devices) report prompts the user for the Scanned Since date to report on. The report can also be run for All machines, Virtual Machines only or Non-virtual Machines only.
This report is grouped by User Domain, User Name and Class and sorted by Device Description.
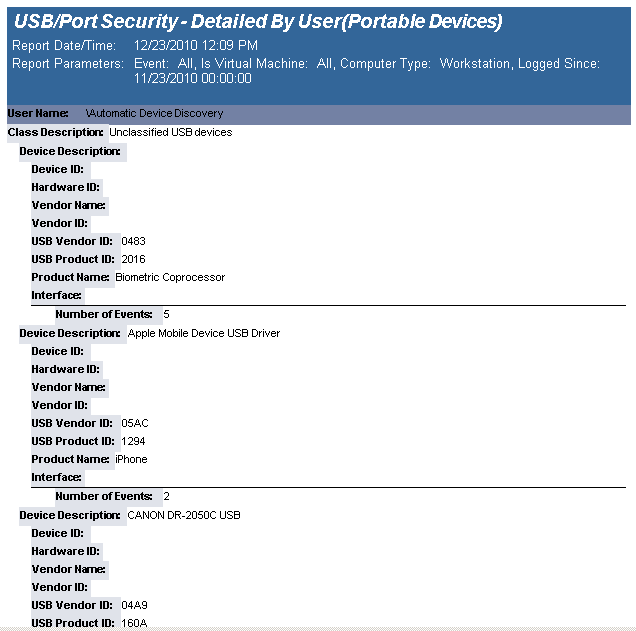
The USB-Port Security - Detailed by User (Portable Devices) report reports on data collected about all Portable device classes, USB and Firewire.
The USB-Port Security - Detailed by User Portable Devices) report prompts the user for the Scanned Since date to report on. The report can also be run for All machines, Virtual Machines only or Non-virtual Machines only.
This report is grouped by User Domain, User Name and Class and sorted by Device Description.
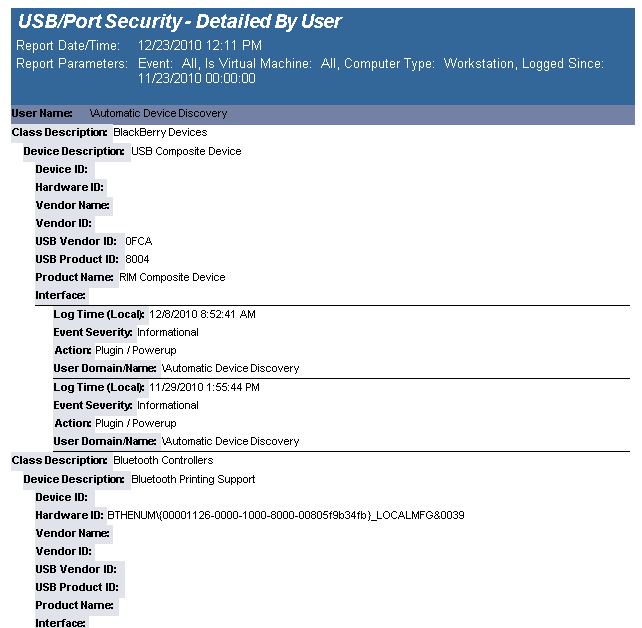
The USB-Port Security - Detailed by User report reports on data collected about each class of devices. Device classes include Blackberry, Bluetooth, CD/DVD, Firewire, Floppy Disks, Hard Disk Drives, Infrared ports, IoMega devices, MP3 Players, Modems, PCMCIA controllers, Palm OS Devices, Parallel ports, Pocket PC devices, Removable storage devices, Serial ports, USB storage and WiFi devices.
The USB-Port Security - Detailed by User report prompts the user for the Scanned Since date to report on. The report can also be run for All machines, Virtual Machines only or Non-virtual Machines only.
This report is grouped by User Domain, User Name and Class and sorted by Device Description.
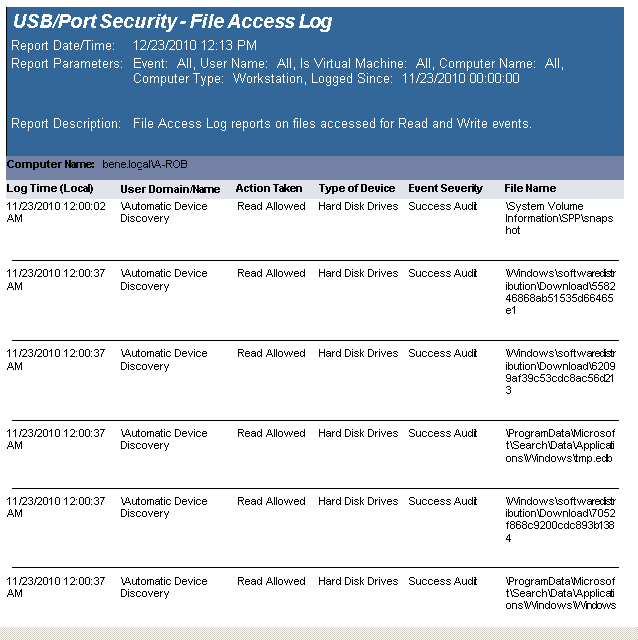
The USB-Port Security - USB File Access Log reports data collected about files that have been touched for read or write access, to or from a USB device.
The USB-Port Security - USB File Access Log prompts the user for the Event, User Name, Virtual Machine type, Computer Name, Computer Type, and Logged Since date to report on.
This report is grouped by Computer Name and is ordered by event log time.
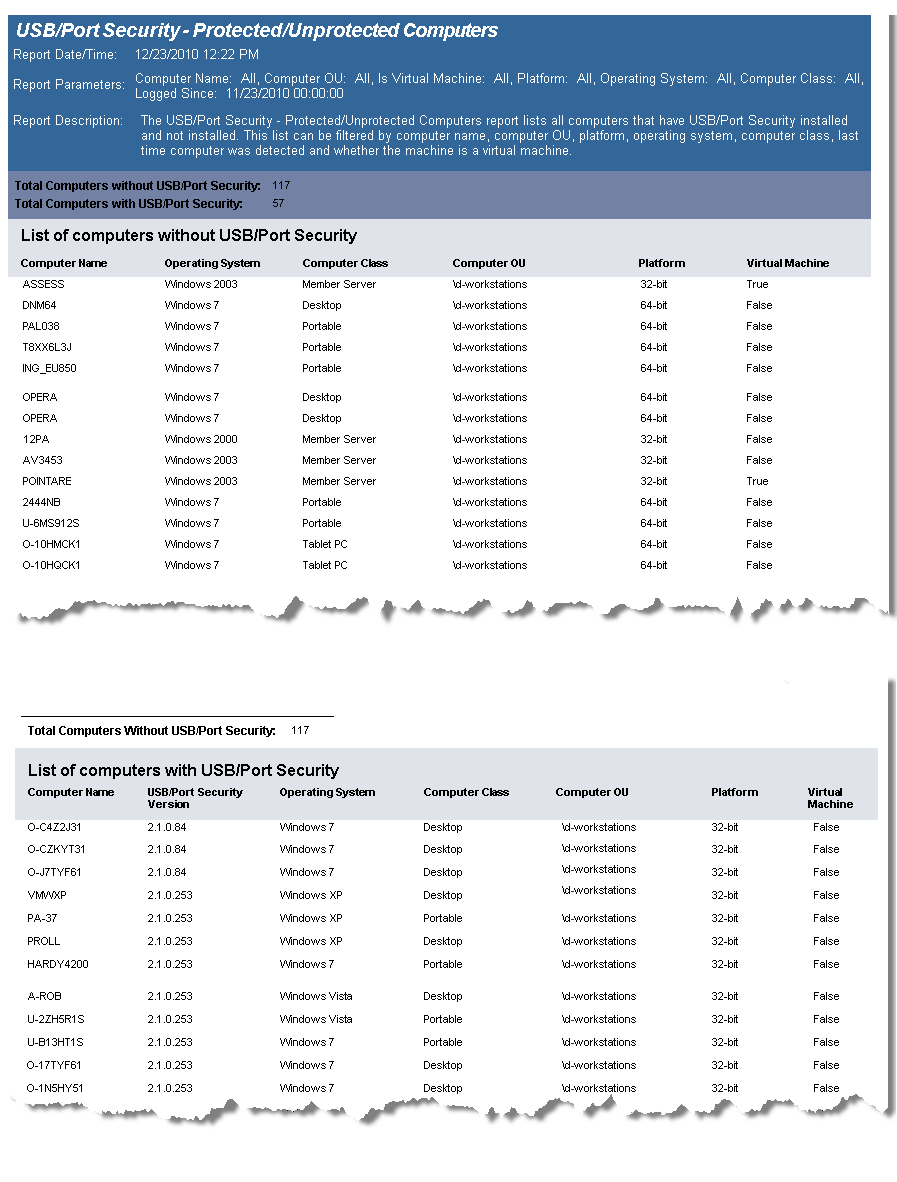
The USB/Port Security Protected/Unprotected Computers report lists all computers that have USB/Port Security client installed and those that do not have the client installed and grouped accordingly.
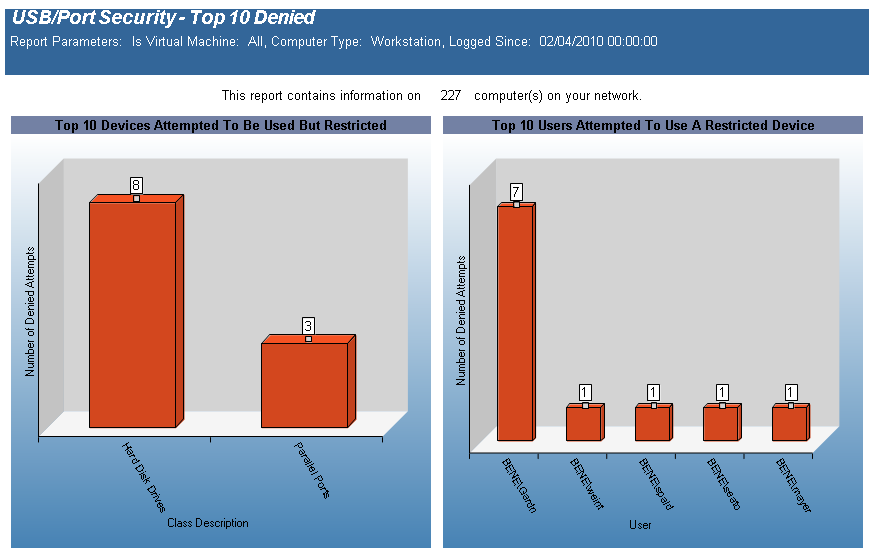
The USB-Port Security - Top 10 Denied report is a graphical report displaying the Top 10 Devices Attempted to be Used but Restricted and the Top 10 Users Attempting to use a Restricted Device. The Top 10 Devices Attempted to be Used but Restricted graph is grouped by device class. The Top 10 Users Attempting to use a Restricted Device is grouped by User Domain/User Name.
The USB-Port Security - Top 10 Denied report prompts the user for the Scanned Since date to report on. The report can also be run for All machines, Virtual Machines only or Non-virtual Machines only.
The USB-Port Security - Users Denied report reports on data collected about Users that generated denied and/or disabled device events. The report is grouped by User Domain, User Name, Class Description and Device Description.
The USB-Port Security - Users Denied report prompts the user for the Scanned Since date to report on. The report can also be run for All machines, Virtual Machines only or Non-virtual Machines only.
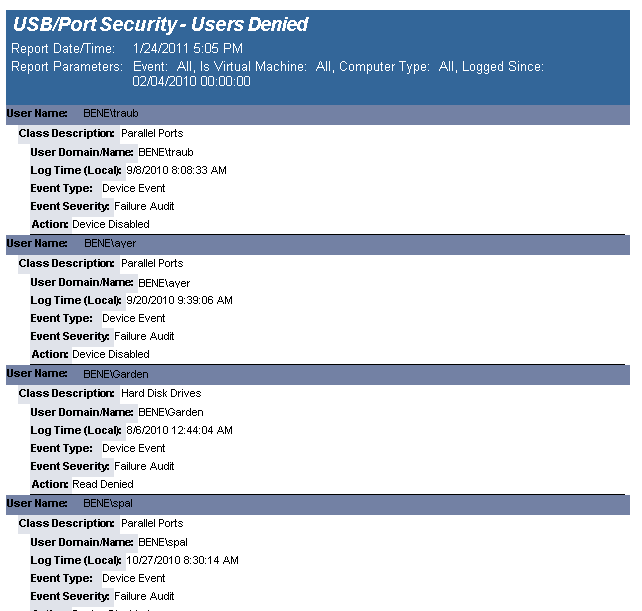
The USB-Port Security - Users Denied (Fixed Devices) report reports on data collected about Users that generated denied and/or disabled device events. The report is grouped by User Domain, User Name, Class Description and Device Description.
The USB-Port Security - Users Denied(Fixed Devices) report prompts the user for the Scanned Since date to report on. The report can also be run for All machines, Virtual Machines only or Non-virtual Machines only.

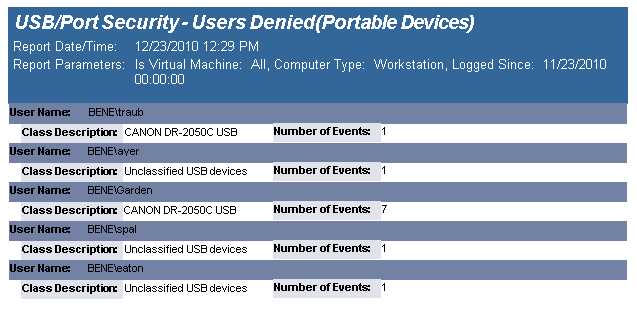
The USB-Port Security - Users Denied(Portable Devices) report reports on data collected about Users that generated denied and/or disabled device events. The report is grouped by User Domain, User Name, Class Description and Device Description.
The USB-Port Security - Users Denied (Portable Devices) report prompts the user for the Scanned Since date to report on. The report can also be run for All machines, Virtual Machines only or Non-virtual Machines only.
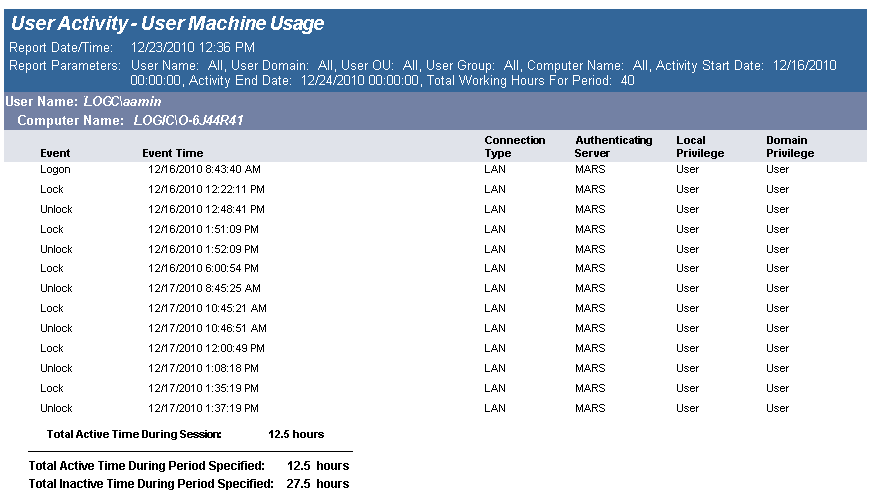
The User Activity - Machine User Usage report details user activity on each computer. Total active and inactive session times are calculated. Total active time per session is the time between logon or unlock to lock or logoff. Total inactive time is (total working hours for the time period) (total active time for the time period).
Usage events are grouped by computer and then by each user of the computer.

The User Activity - Summary Page report displays, graphically, user activity across multiple computers. Usage events are grouped by user, then by each computer they have logged on to. Total active time is tallied for all computers. Total active time per session is (login or unlock) to (lock or logoff). Total inactive time is (total working hours for the time period) (total active time for the time period) (no lower than 0).
This report can be used for scenarios where users log on to multiple computers over the course of the working hours period, for example, when a user uses a different computer every day over the course of a week.

The User Activity - User Machine Usage report details user activity over multiple computers. Total active and inactive session times are calculated. Total active time per session is the time between logon or unlock to lock or logoff. Total inactive time is (total working hours for the time period) (total active time for the time period).
Usage events are grouped by user and then by each computer the user has logged on to.
This tends to be a large report. It may be necessary to narrow down the report parameters by user, computer or a smaller date range.
The User Activity Per Computer - Summary Page report displays, graphically, the top 10 inactive users and top 10 active users. Total active and inactive session times are calculated. Total active time per session is the time between logon or unlock to lock or logoff. Total inactive time is (total working hours for the time period) (total active time for the time period).
This report can be used for scenarios where a user may be logged into more than one workstation at one time.

The User Activity Per Computer report details user activity on each computer that the user has logged on to and tallies active time for each computer. Total active and inactive session times are calculated. Total active time per session is the time between logon or unlock to lock or logoff. Total inactive time is (total working hours for the time period) (total active time for the time period).
This report can be used for scenarios where a user may be logged into more than one workstation at one time.
The report is grouped by User ID and Computer ID.
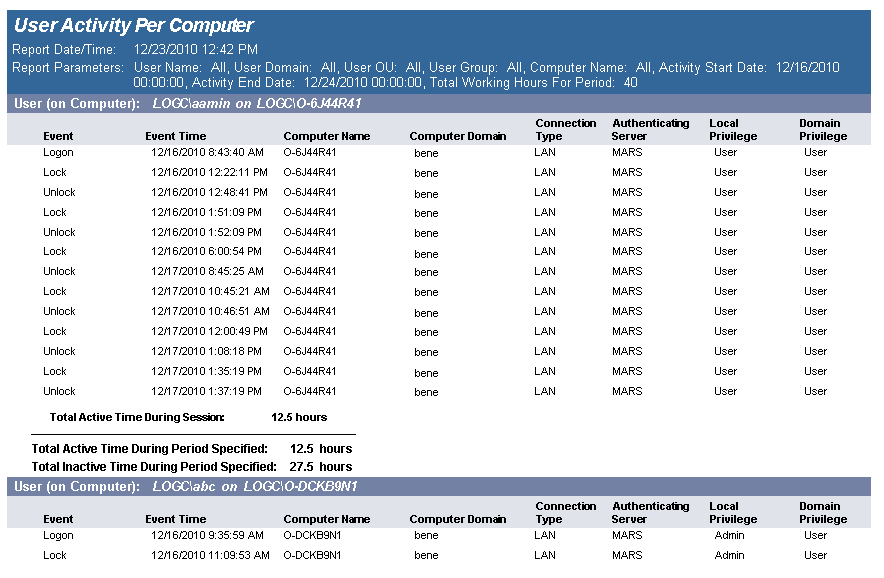
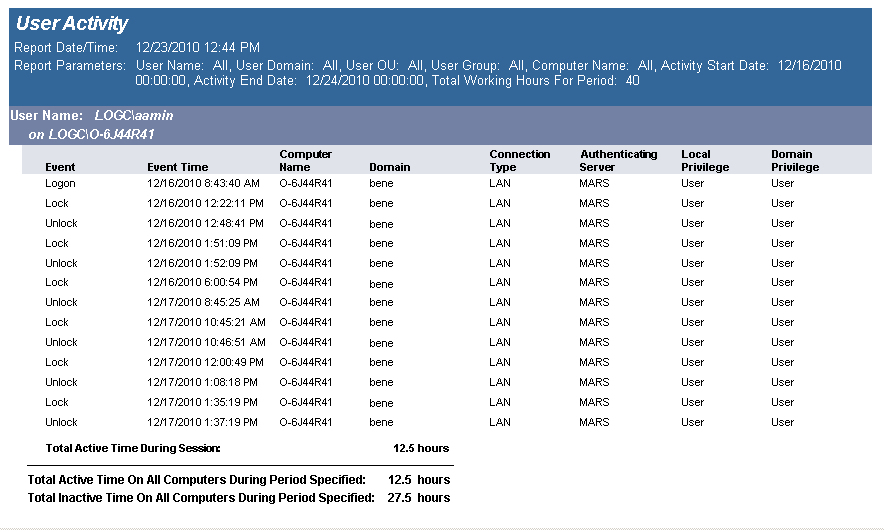
The User Activity report details user activity across multiple computers. Usage events are grouped by user then by each computer they have logged on to. Total active time is tallied for all computers. Total active time per session is (login or unlock) to (lock or logoff). Total inactive time is (total working hours for the time period) (total active time for the time period) (no lower than 0).
This report can be used for scenarios where users log on to multiple computers over the course of the working hours period, for example, when a user uses a different computer every day over the course of a week.
The report is grouped by User and is sorted by UserId, Computer Domain, Computer Name and Activity Time.
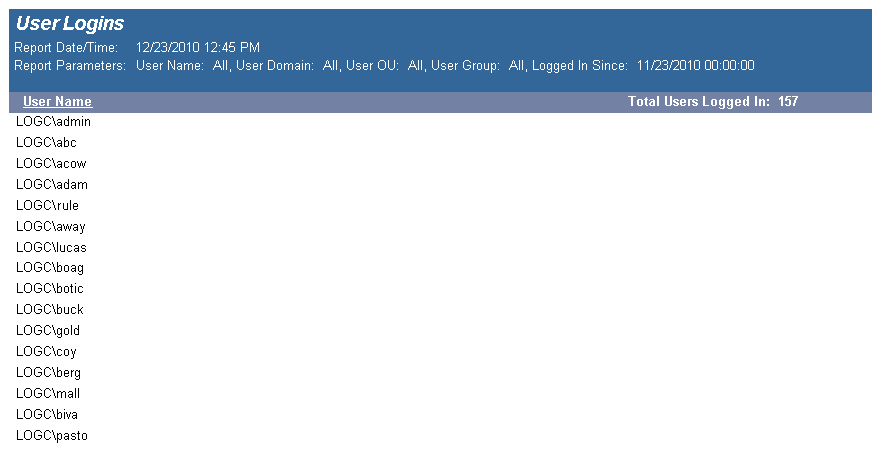
The User Logins report details user logins across the enterprise. This report can be used to sum the number of logins per User Name, Domain, OU, or Group based on the date the user last logged in.