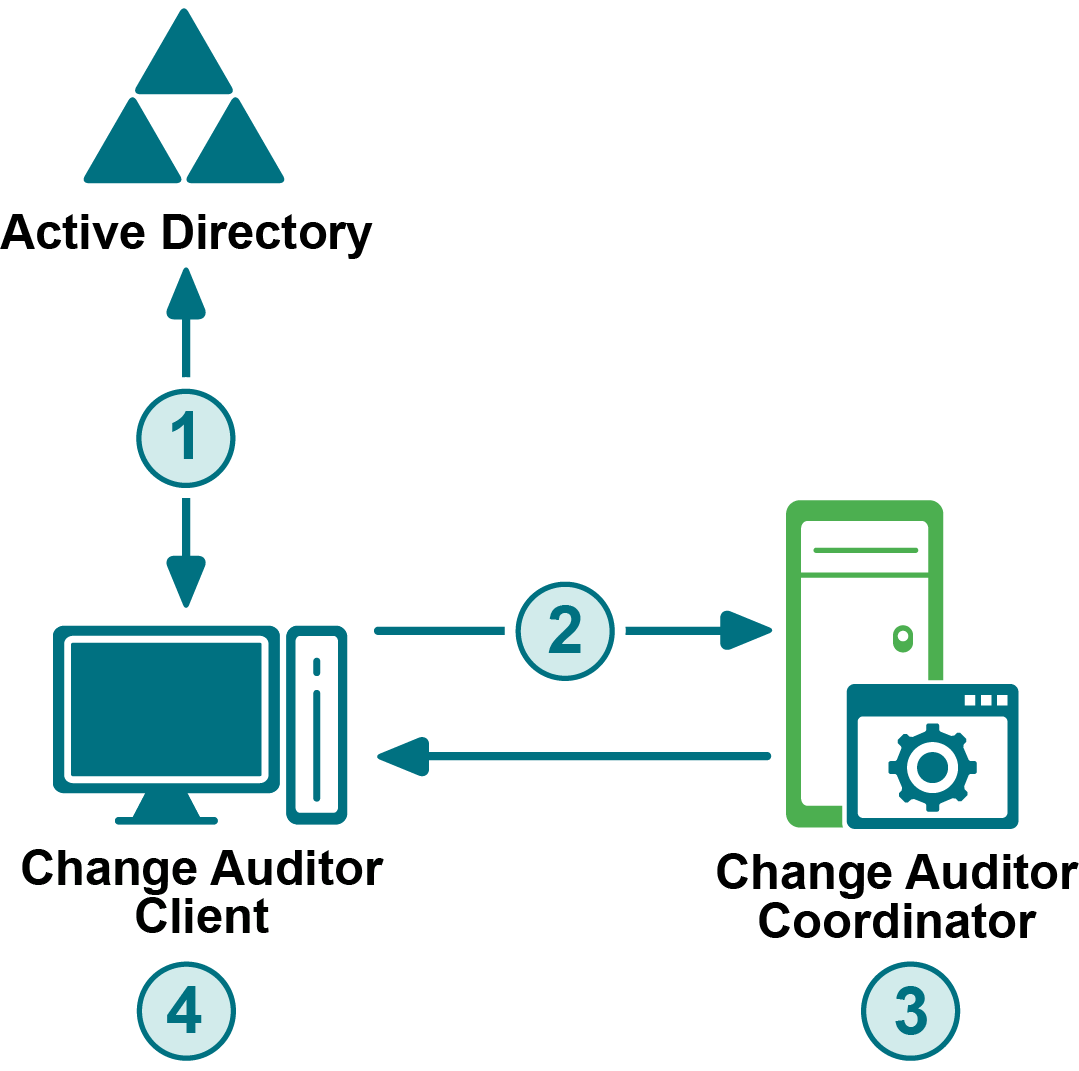
Change Auditor Services
Quest Change Auditor Coordinator
Quest Change Auditor Workstation Agent
Quest Change Auditor Agent
Change Auditor for EMC
Change Auditor licensing processes
Component Start-up Considerations
Change Auditor network communications
Coordinator internal tasks
Forest topology collection
Group expansion
Alert processing
License check
Remote deployment
Agent heartbeat check
Refresh coordinator statistics
Event aggregator
SQL upgrade monitor
Open handle
Scheduled purge job
Scheduled archive job
Scheduled report job
Registry Settings
Force agent WCF port
Force client port
Force SDK port
Use predefined GC for name resolution
Allow collation switch
Report zip limit
SQL command timeout
Enable ChangeAuditor Agent service to start with the Microsoft security update (KB2264107)
Adjust memory dumps settings
Change Auditor built-in fault tolerance
Change Auditor protection
Database Considerations
How to move the Change Auditor database and coordinator to another server
How to estimate the required SQL server disk space
How SQL Server Autogrow affects Change Auditor
How to query an archive database
Account exclusions best practices
Secure password storage
|
1 |
Change Auditor uses CryptProtectData with a key length that is variable-dependent upon input phrase. This encryption is symmetric. This encryption is automatically enabled. This encryption cannot be used outside of Change Auditor.
Client to coordinator connection
Agent to coordinator connection (version 6.x and 7.0.1)
|
3 |
Agent to coordinator connection (version 7.0.2)
|
2 |