-
タイトル
Multi-factor Authentication on Metalogix Archive Manager -
説明
Multi-factor Authentication
ArchiveWeb supports multi-factor authentication (MFA) for O365 user accounts. Setting up MFA is a two-step process:
1.Create a new application in the Azure portal.
2.Configure ArchiveWeb with the Archive Manager configuration tool.
-
対策
Create a new application in the Azure portal
ArchiveWeb requires a specific Azure site to be created that is used to return an authentication token back to the ArchiveWeb after a user is authenticated via Microsoft portal.
1.Login to your Azure Portal using your administrator credentials (https://portal.azure.com). If your account gives you access to more than one tenant, select your account in the top right corner, and set your portal session to the Azure AD tenant that you want.
2.In the left-hand navigation pane, select the Azure Active Directory service, and then select App registrations > New registration. The App registrations page appears.
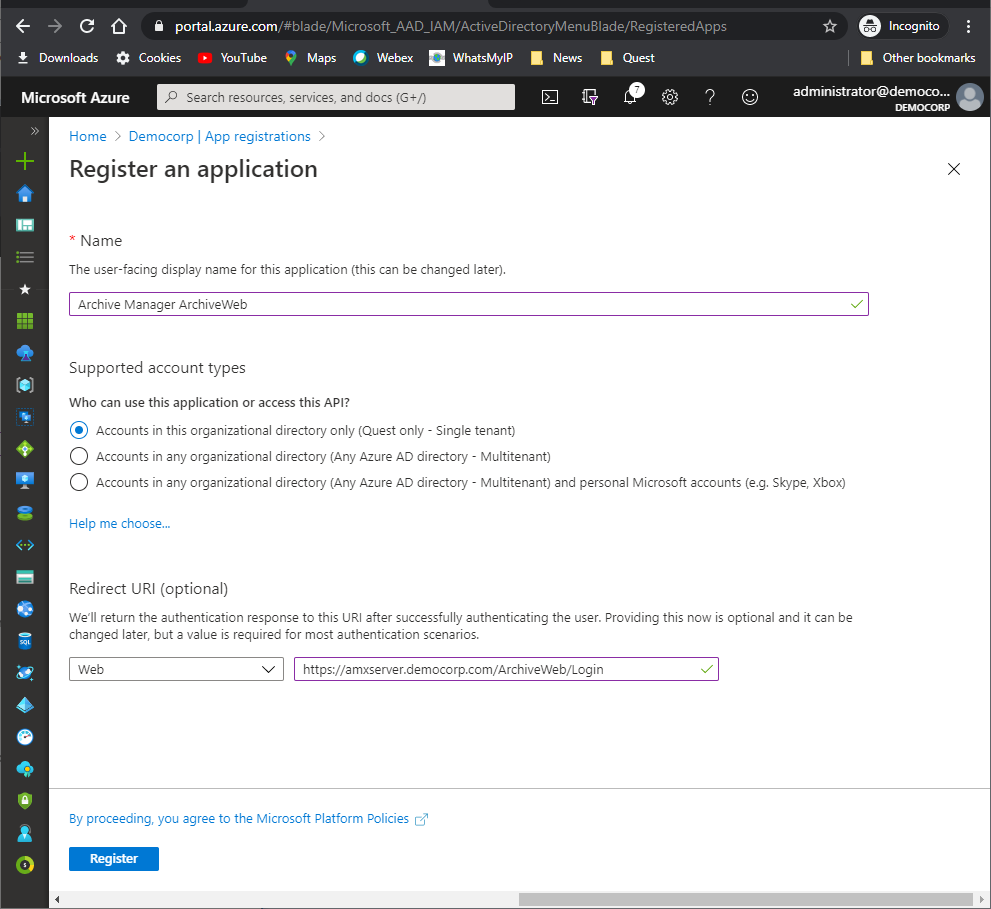
3.Click New registration. The Register an Application page appears.
4.Provide the information on this page as described below:
a.Name - Enter a meaningful application name that will be displayed to users. For example, Archive Manager ArchiveWeb.
b.Supported account types - Select the account type you would like your application to support that best meets your company policy.
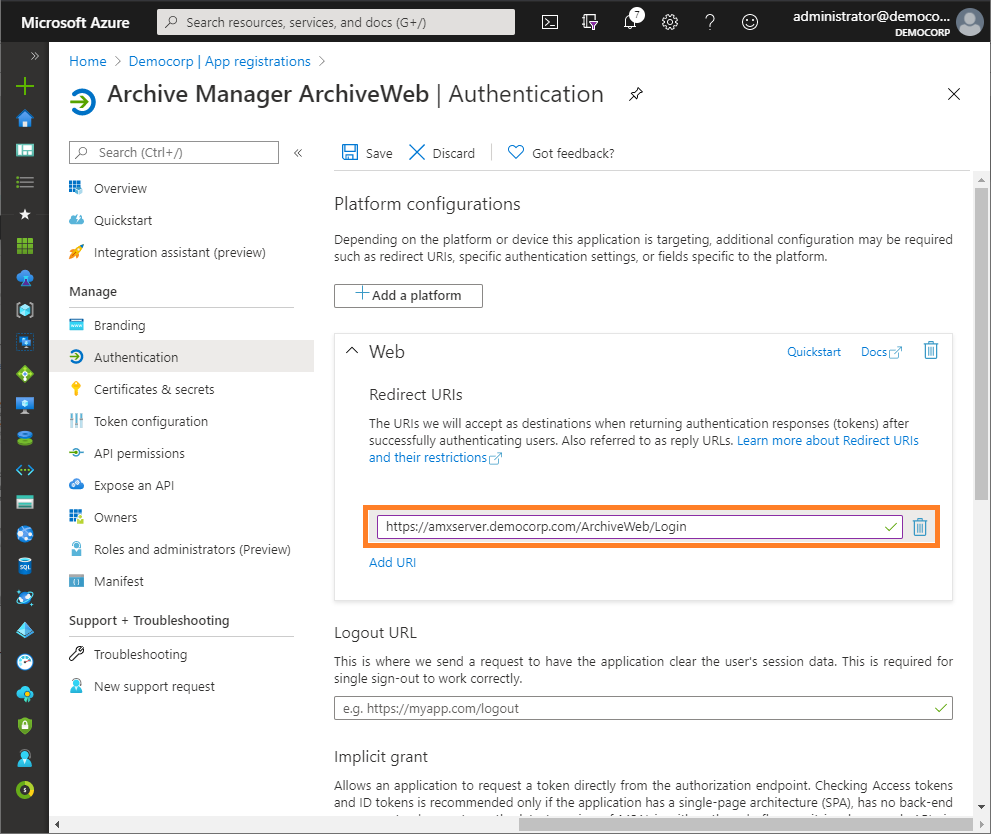
c.Redirect URI - from the application type dropdown select Web. In the URI field enter the ArchiveWeb URI where the user will be redirected after multi-factor authentication (eg. https://<fullservername>/ArchiveWeb/Login)
NOTE: The HTTPS protocol is required for MFA to work with O365. To ensure the HTTPS can be used, follow the steps below;
1.On the ArchiveWeb server, open the IIS Management Console.
2.Expand the server node and then expand the Sites node.
3.Select Default Web Site and right-click to open the context menu. Then select Edit Bindings. The Site Bindings window opens.
4.Click Add. The Add Site Bindings window opens.
5.Select https from the Type dropdown and fill in the other details as required.
6.Click OK to save the https site binding.
7.Restart the IIS service from the server node and then close the IIS Management console.
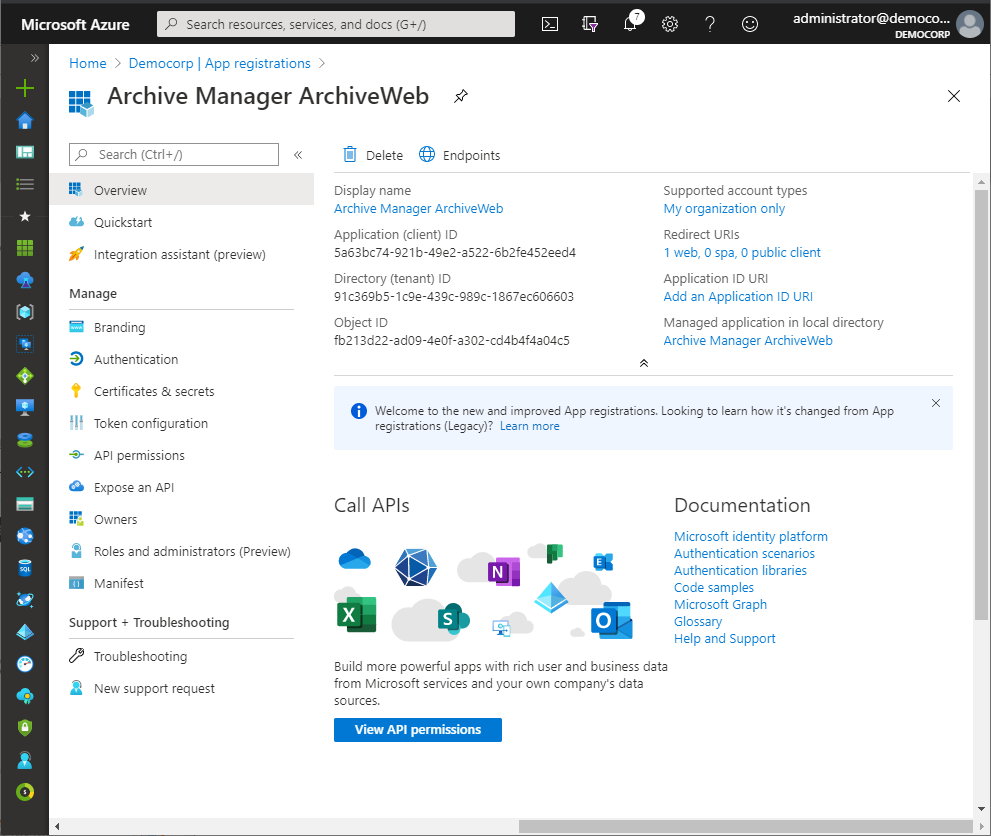
5.Click Register. Azure AD assigns a unique application (client) ID to your app, and the application's Overview page opens.
6.From the navigation menu, click Branding. Enter the URLs that your organization may use for the different branding artifacts.
7.From the navigation menu, click Authentication and verify that the Redirect URI parameters are as expected.
8.From the navigation menu, click Certificates & Secrets.
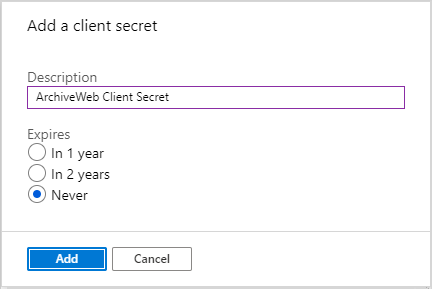
9.In the Client secrets section click New client secret. the Add a client secret page opens.
10.Enter values as described below:
a.Description - enter a meaningful description. For example, ArchiveWeb Client Secret.
b.Expires - set the expiry term that best meets your company policy.
11.Click Add. the client secret is displayed on the Certificates & Secrets page.
IMPORTANT: Copy and save the client secret in a safe place. It will not be available when you navigate away from this Azure blade.
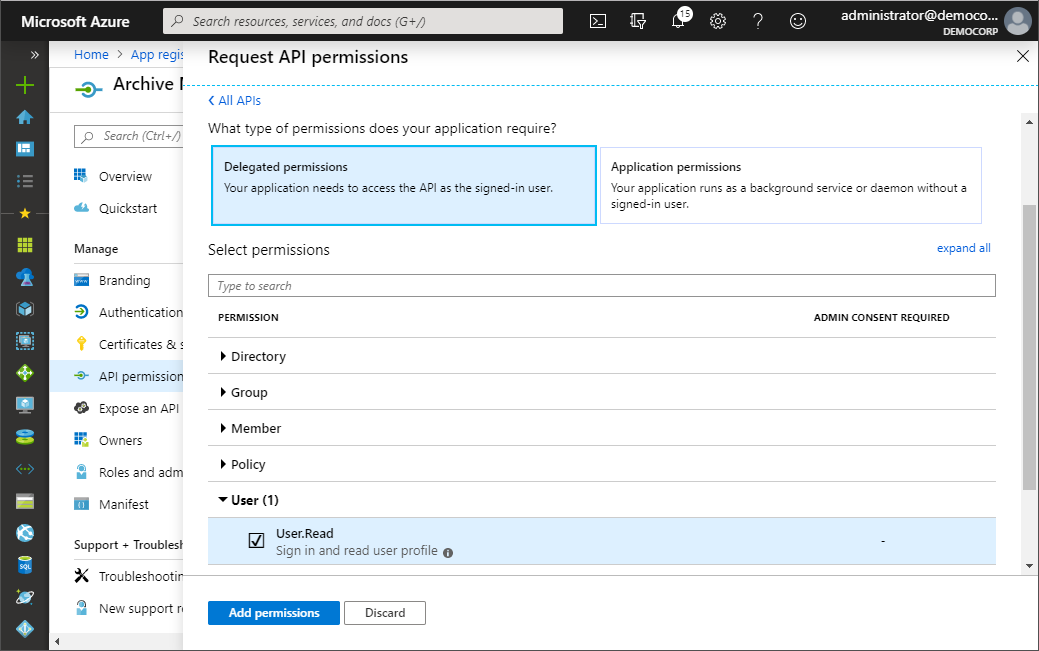
12.From the navigation menu, click API Permissions. and then click Add a permission. The Request API permissions page appears.
13.From the Microsoft APIs category, scroll down to the Supported legacy APIs section and select Microsoft Graph.
14.From the Request API permissions page for Azure Active Directory Graph that appears, select Delegated permissions.
15.Click Add permission.
16.From the navigation menu, click Expose an API.
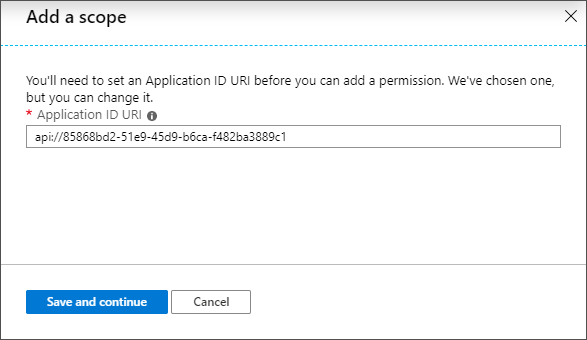
17.In the Scopes defined section, click Add a scope. The Add a scope page opens.
18.Microsoft Azure generates an Application ID URI automatically. It is a globally unique URI used to identify this web API. It is the prefix for scopes and in access tokens,and is also referred to as an identifier URI. You can keep this value or specify a unique value in the same format.
IMPORTANT: Copy and save this value in a safe place.
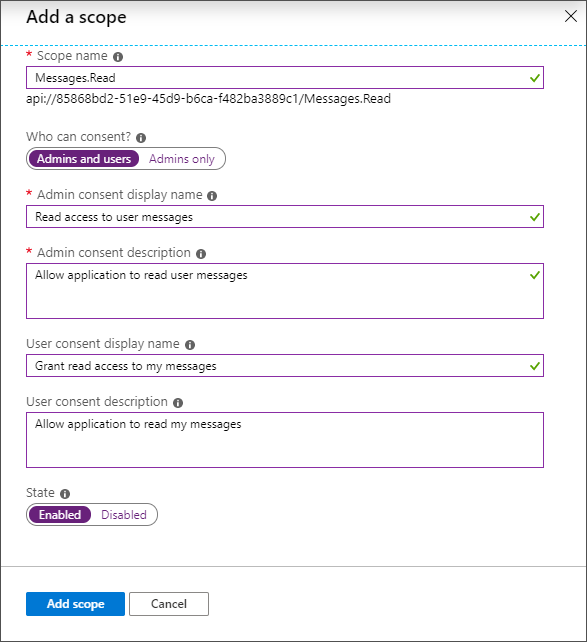
19.Click Save and continue. The Add a scope page displays more options.
20.Click Add scope to complete the registration.
Configure ArchiveWeb with the Archive Manager configuration tool1.Open the Archive Manager Configuration Tool from C:\Program Files (x86)\Common Files\PAM\PAMConfig\PamConfig.exe
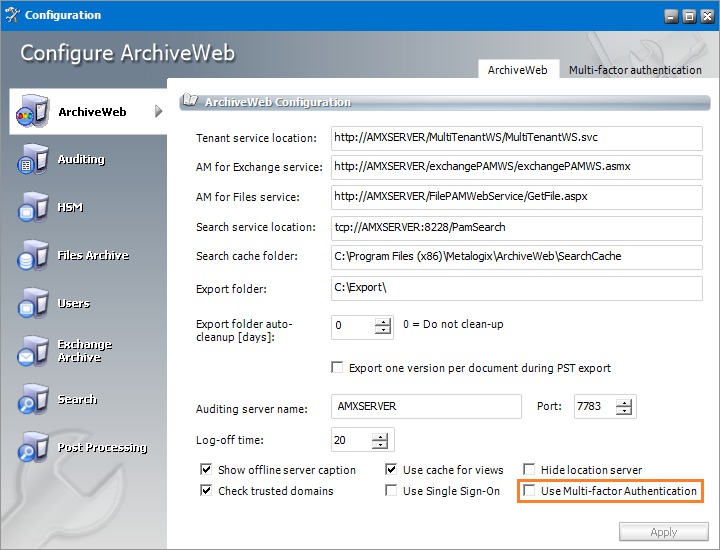
2.From the sidebar, click ArchiveWeb.
3.Click the ArchiveWeb tab. The ArchiveWeb Configuration page appears.
4.Select Use Multi-factor Authentication to activate the fields in the Multi-factor authentication Configuration window.
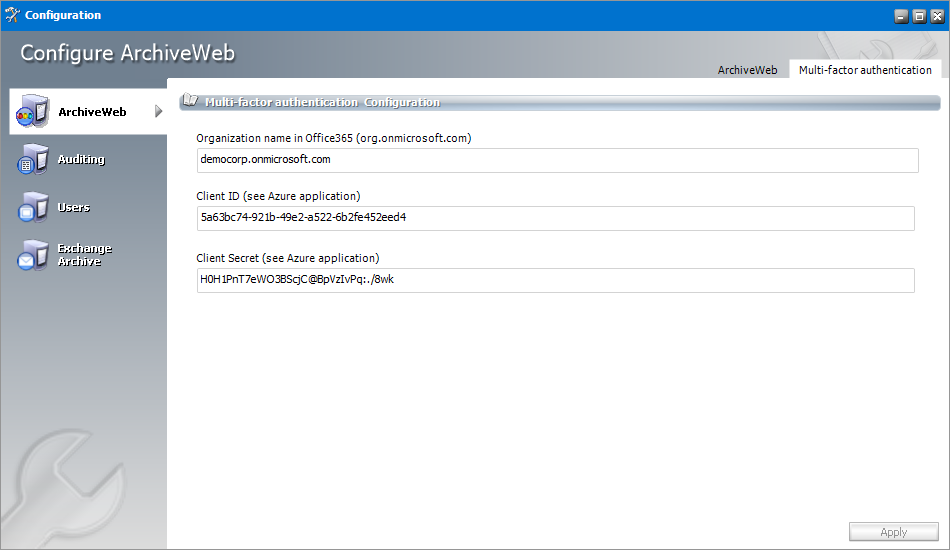
5.Click the Multi-factor authentication tab. The Multi-factor authentication Configuration window appears.
6.Enter the field values as described below:
a.Organization Name in Office365 - enter the name of your O365 organization URL. For example, democorp.onmicrosoft.com
b.Client ID - enter the Client Id that you saved from the Azure application registration steps.
c.Client Secret - enter the Client Secret that you saved from the Azure application registration steps.
7.Click Apply.
-
追加情報
IMPORTANT: When at least one user in an organization has MFA set, the Organization, Client ID and Client Secret should be set in Multi-factor authentication tab as a readiness exercise. If only a few users in your organization have MFA activated, the Use Multi-factor Authentication checkbox should remain unchecked. The settings in the Multi-factor authentication tab will persist when the Use Multi-factor Authentication checkbox is unchecked. The users who have MFA activated will be prompted to enter the credentials (user email and password) and then they will be redirected to the Microsoft site where the user has to authenticate again. After a successful authentication by Microsoft, the user will be redirected back to ArchiveWeb. When all users accounts in an organization have MFA activated, the Use Multi-factor Authentication checkbox can be selected. This will allow ArchiveWeb to use multi-factor authentication for all users that log in to ArchiveWeb. Users will be prompted to enter only the login email address and they will be redirected to the Microsoft login form to finish the login process.