Monitoring HTTPs URLs in FIPS-compliant mode
|
1 |
Launch a command shell on the Agent Manager machine, and navigate to the <fglam_home>/bin directory. |
Monitoring URLs that require a client certificate
|
1 |
Deploy the WebMonitor Agent to the Foglight Agent Manager. |
|
NOTE: Ensure you have read and write rights for the following path: {fglam_home}/state/default/certificates
|
The Microsoft® Internet Information Server (IIS) by default enables the TLSv1 and disables the TLSv1.2 protocols. The JDK 1.7+ (included in Foglight Agent Manager 5.7.4 and later) by default handles handshake with TLSv1.2. If the server side and the client side do not include the same supported TLS version, this causes the HTTPs request to fail. The following workarounds are available in this case:
|
1 |
|
1 |
Enable TLSv1.2 for your IIS server. (Refer to the best practice to configure IIS with SSL/TLS.) |
|
3 |
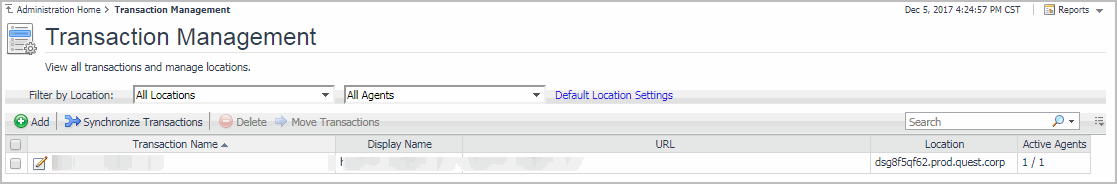
Exploring your collection of monitored Web sites
For complete details about the data appearing on this dashboard, see the Transaction Management table.
|
2 |
For more information, see the following topics:
Expanding your collection of monitored sites
This assumes that you already have the agent package deployed to the Foglight Agent Manager host, and one or more active Web Monitor Agent instances in place. For complete information on how to deploy an agent package, and to create and activate agent instances, see the Administration and Configuration Help.
|
2 |
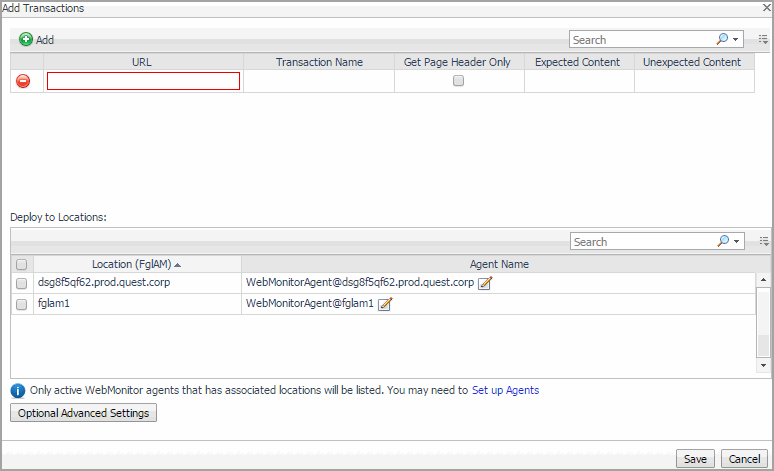
In the Add Transactions dialog box, provide information about the Web site whose transactions you want to start monitoring. |
|
• |
URL: The URL of the Web site that you want to monitor. |
|
• |
Transaction Name: The name you want to associate with the transactions with this Web site. |
|
• |
Get Page Header Only: Indicates whether you want to collect the page header only. |
|
• |
Expected Content: If content validation is enabled for the agent instance that you want to monitor this URL, and the expected content type is HTML-based, type html in this column. Also, a text string could be used such as “laptop” and type laptop into this column. In case the monitoring agent detects binary content or the text string at this address, the validation fails and the agent logs an error message. |
|
• |
Unexpected Content: If unexpected content validation is enabled for the agent instance that you want to monitor this URL, and the unexpected content type is HTML-based, type html in this column. Also, a text string could be used such as “laptop” and type laptop into this column. In case the monitoring agent detects binary content or the text string at this address, the validation fails and the agent logs an error message. If this column is empty, that means the agent is not required to perform unexpected content validation. |
|
3 |
To add more URLs to the list, click Add, and populate the row that appears. To remove a row from the list, click |
|
4 |
In the Deploy to Locations area, select one or more Web Monitor Agent locations that you want to use to monitor the transactions with the newly specified Web sites. |
|
5 |
Optional—Specify thresholds for alarm generation, authentication, and proxy settings. If the URL requires user authentication, you need to supply credentials for accessing that URL. |
|
a |
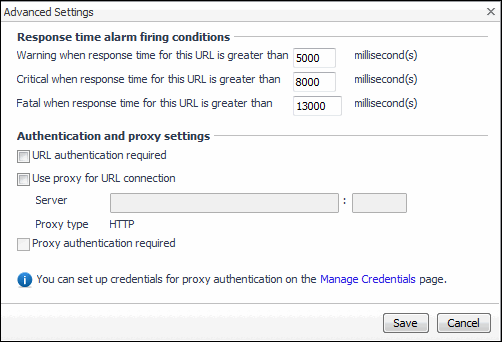
Click Optional Advanced Settings. |
|
b |
In the Advanced Settings dialog box, in the Response time alarm firing conditions area, review the thresholds for alarm generation, and edit them, if required. |
|
c |
In the Authentication and proxy settings area, specify the following information, as required. |
|
• |
URL authentication required: Select this check box only if the URL requires user authentication. If that is the case, you need to ensure that you have proper credentials in place to enable the Web Monitor Agent to access it. Click Manage Credentials to review the existing credentials, or to create new ones, as required. For more information, see Configuring credentials to access Web sites requiring user authentication. |
|
• |
Use proxy for URL connection: Select this check box only if the Web Monitor needs to use a proxy to access the specified URL. Click Manage Credentials to review the existing credentials, and create new ones, as required. For more information, see Configuring credentials to access Web sites requiring user authentication. |
|
• |
Server: If you need to configure proxy access, type the name of the proxy server followed by the port number. |
|
• |
Proxy authentication required: Select this check box if the proxy requires authentication. |
|
6 |