Advanced system configuration for WinRM
The advanced configuration for non-administrative users includes the following steps:
To add a non-administrative user to the above user groups:
|
1 |
Run lusrmgr.msc. |
|
2 |
From the Local Users and Groups (Local) > Users list, right click the non-administrative user who you want to add, and then click Properties from the context menu. |
|
3 |
|
4 |
Click Add. |
|
5 |
In the Select Groups dialog box, type Performance Monitor Users;Event Log Readers in the Enter the object names to select field, and then click Check Names. |
|
6 |
Click OK to return to the <non-administrative user> Properties dialog box. |
To grant the WinRM RootSDDL permission to a non-administrative user:
To grant the permission to the namespace for the current non-administrative user:
|
9 |
The following sample demonstrates how to grant permission to the SCMANAGER service:
|
3 |
Add “(A;;CCLCRPRC;;;S-1-5-32-558)” between “D:” and “(A;;CC;;;AU)”, and execute the sc sdset command to grant the permission to the SCMANAGER service. For example, execute the following command: |
|
• |
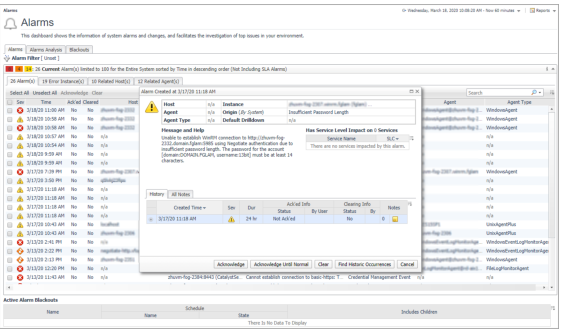
Access the Foglight Management Server’s Homes > Alarms dashboard and check if there is an “Insufficient Password Length” alarm related to your monitored host. See the example as below: |
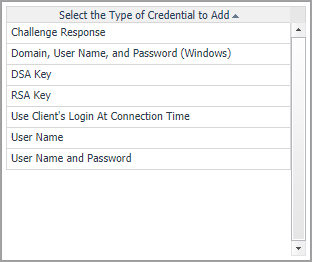
Configuring default local user credentials for Infrastructure Agents
|
2 |
|
3 |
|
4 |
|
5 |
|
6 |
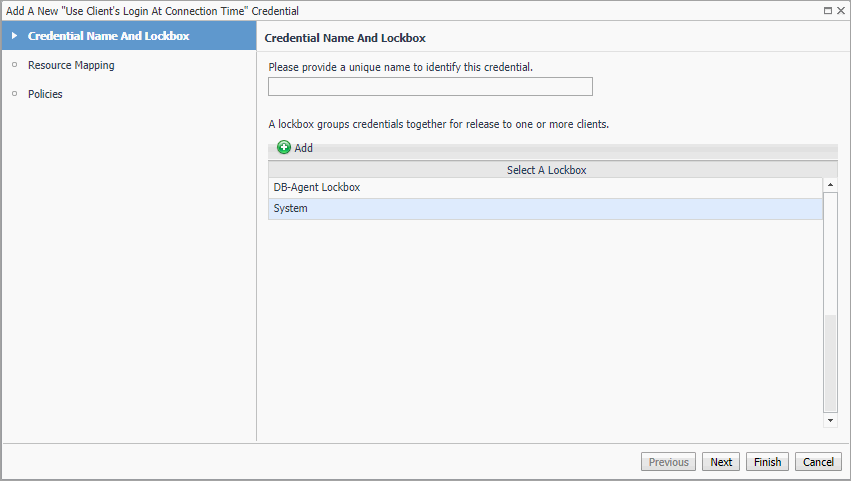
On the Credential Name and Lockbox page, select the lockbox in which you want to store the local user credential, and specify a unique credential name. Click Next. |
|
a |
|
b |
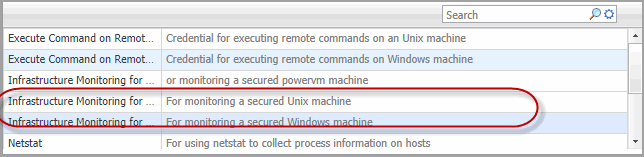
Select the appropriate Usage according to your operating system. To open the Usage drop-down list, click the down-facing arrow on the right. Select either of the following: |
|
• |
Local Unix machine - Infrastructure Monitoring for Unix |
|
• |
Local Windows machine - Infrastructure Monitoring for Windows |
|
c |
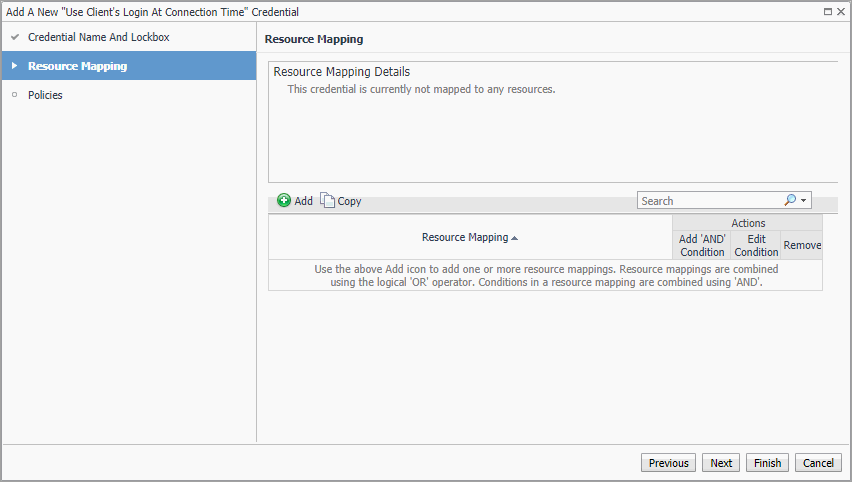
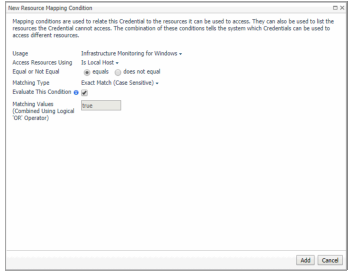
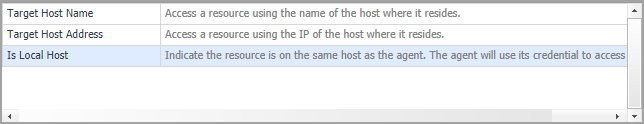
Click the down-facing arrow on the right to open the Access Resources Using drop-down list. Select the Is Local Host. |
|
d |
|
e |
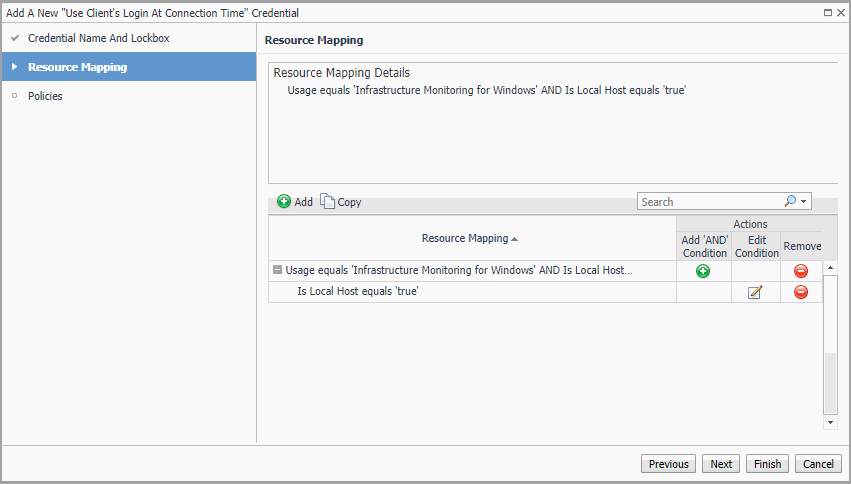
The New Resource Mapping Condition dialog box closes and the Resource Mapping page refreshes. The newly specified resource mapping is displayed. |
|
f |
Optional—you can refine your credential settings. For example, to specify the time during which the credential is valid, the number of failed attempts after which the credential will be locked, the number of times the credential can be used, or the period of time during which the credential data is cached on the server. For complete information, see the Administration and Configuration Help. |
|
8 |
Click Finish. |
Reference
For more details, see these topics:
|
• |
|
• |