Service accounts
Foglight® manages login credentials for the following service and user accounts:
|
• |
Foglight Users—Foglight supports both internal and external users. Internal users are defined within Foglight while external users are mapped from one of the LDAP-compatible directory services supported by Foglight (Active Directory®, Oracle® Directory Server Enterprise Edition, and OpenLDAP®). |
|
• |
LDAP Directory—For Foglight to access an LDAP directory, the customer needs to provide LDAP service-account credentials (user name and password for an account with read access to the directory). |
|
• |
Foglight Management Server Database Repository—Foglight supports using specific versions of MySQLTM, Oracle®, and Microsoft® SQL Server® databases for its storage repository. The login credentials for a database administrator account are specified during Foglight installation. For customers who do not provide a database administrator account, the creation of the external database may be delayed, as the database will require manual configuration. |
Agent credentials
When installing Foglight® cartridge agents it is typically necessary to enter credentials for the user accounts that are on the monitored resources, including the host and database. These credentials are entered through the agent configuration properties via the Foglight Administration Console and give an agent access to applications or operating systems on the monitored hosts.
The Management Server includes a central credential service that manages cartridge agent credentials. A lockbox contains a set of credentials and keys for their encryption and decryption. Releasing a lockbox to a credential client enables the client to release the credentials to the agent instances managed by that client, thereby granting the agent instances access to the monitored system. For more information, see Controlling remote system access with credentials.
Foglight users and groups
There are two types of users in Foglight: internal and external users. Internal users are created using the Foglight® Administration Console. External users are mapped from one of the LDAP-compatible directory services supported by Foglight. All Foglight users are authenticated upon login, based on their user names and passwords.
Foglight includes one default internal user (foglight) with administrative access, and four default internal groups (Cartridge Developers, Foglight Administrators, Foglight Operators, and Foglight Security Administrators), none of which cannot be deleted.
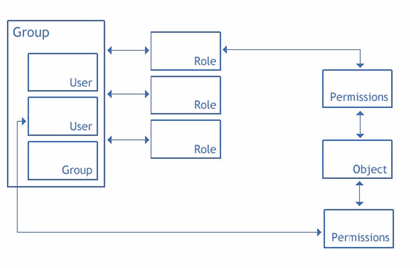
Role-based access control
Foglight® security model is based on a role-based access control system (RBAC).
|
A user has a username and a password and can belong to one or more groups. |
||
|
A group can contain one or more users or other groups. Roles are assigned to users through groups. |
||
Roles dictate the actions that a user can perform. There are two types of roles in Foglight: default roles (called built-in roles), and custom roles (called internal roles).