Selecting the encryption algorithm
Encrypting primary or secondary backups
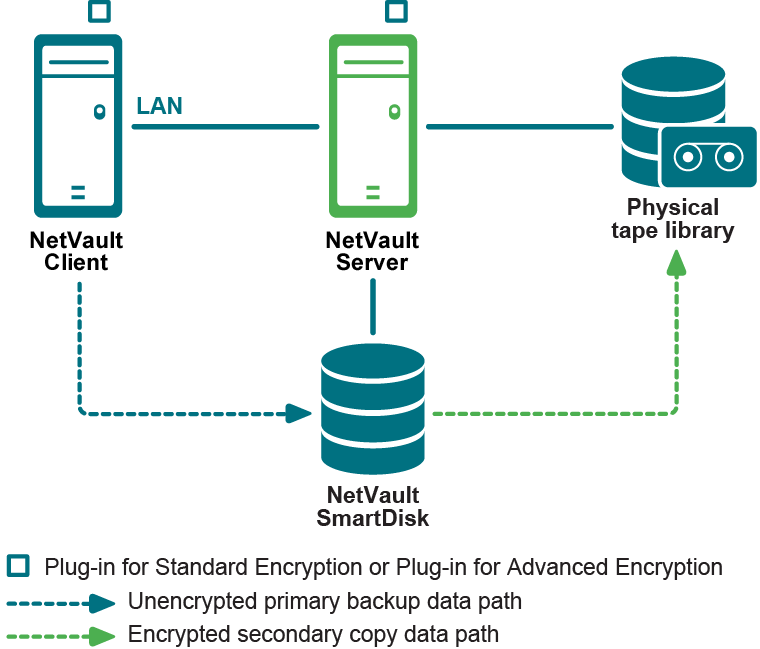
Encrypting all or specific backups
The Plug‑in for Encryption lets you enable encryption for all backups on the NetVault Server or Client where a plug-in is installed, or enable encryption only for specific jobs. Encryption can also be enabled only for the primary backup or the secondary copies. This approach lets you take advantage of both encryption and deduplication. For example, you can deduplicate the primary backup and encrypt the secondary copy.
The job-level encryption option can be used in the following situations:
|
• |
Configuring default settings
|
1 |
In the Navigation pane, click Change Settings. |
|
2 |
|
3 |
|
After the Plug‑in for Encryption is automatically installed with NetVault on a client, you can do either of the following: For more information about enabling encryption for specific backups, see Performing job-level encryption. | |
|
Type the string that serves as the encryption key for the NetVault machine. | |
|
Re-type the encryption string here to confirm that it is correct. | |