Assigning a preferred DNS server during recovery
Before starting a forest recovery operation, you should specify a method for selecting a preferred DNS server for each domain controller in your recovery project.
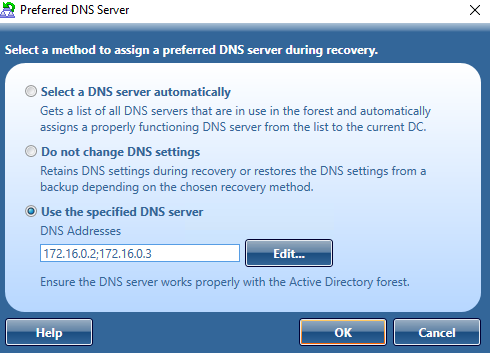
Select the General tab, then at the bottom see Additional Setting | Preferred DNS and click on the Change button.
You can choose one of the following DNS server selection methods:
-
Select a DNS server automatically
Let Recovery Manager for Active Directory automatically select a DNS server (used by default). -
Do not change DNS settings
Recovery Manager for Active Directory retains client DNS settings during recovery or restores the DNS settings from a backup depending on the chosen recovery method. -
Use the specified DNS server
Specify a DNS server manually - here you can specify one DNS address or a list of DNS servers separated by semicolons or using the Edit button.
For more information on how to specify a DNS server selection method, see Domain controller recovery settings and progress.
When you choose to select a DNS server automatically, Recovery Manager for Active Directory (RMAD) retrieves a list of DNS servers used by domain controllers. In live Active Directory, RMAD connects directly to domain controllers to get DNS servers that are currently in use. For Bare Metal Recovery, DNS servers are retrieved from computer settings that are stored in the RMAD BMR backup. For every recovery method that uses clean OS, current DNS client settings are ignored. With the exception of the Restore Active Directory on Clean OS recovery method which installs the DNS server on the target machine.
The automatic DNS selection method is recommended in the following cases:
-
Your DNS is not Active Directory-integrated.
-
Your DNS is Active Directory-integrated and you restore from backups the DNS servers (domain controllers) that act as the primary source for each DNS zone.
For DNS that is not Active Directory-integrated (external DNS), the list of automatic DNS servers is ordered. First come the IP addresses that are included in the DNS client settings on this domain controller. Then, the list includes preferred DNS addresses of other domain controllers in the same domain and their DNS client settings. Then, the same approach is used for domain controllers in the parent domain hierarchy, then in sibling domains, and finally, for direct child domains. Then, during recovery, RMAD automatically selects a properly working DNS server from the received list and assigns that DNS server to the domain controller.
For DNS that is Active Directory-integrated, RMAD first selects DNS servers that are in the same domain. The DNS servers are ordered based on the domain hierarchy from current domain up to root in domain hierarchy. The primary DNS server is selected based on client settings and the most used DNS server in the backup for the DNS zone. The preferred DNS server’s IP address client settings is set on all restored Domain Controllers as the preferred address of the DNS server for the zone the Domain Controller is hosted in. For alternate DNS servers, we obtain a list of other DNS servers which host the DNS zone.
For DNS zones which are forest wide replicated the preferred DNS Server is chosen from the root domain. The same DNS server which is selected as primary for root domain will also be the primary DNS server for any DNS zone which is configured for forest wide replicated.
If a domain controller is a DNS server itself, then a loopback address is included in the DNS server list (see the note below).
By default, the number of DNS servers that can be selected automatically is limited to 3. You can change that number using the MaxAutomaticDnsCount property in advanced settings.
| Important |
It is not recommended to uninstall or reinstall Active Directory on the DNS servers that act as a primary source for an Active Directory-integrated DNS zone. Also, it is not recommended to remove such DNS servers from Active Directory® during recovery . |
The Do not change DNS settings option lets you retain DNS settings during recovery so you do not need to reconfigure DNS settings for each domain controller within the forest after the recovery operation is completed.
When you specify a DNS server or list of DNS servers manually, Recovery Manager for Active Directory first tries to assign the specified DNS server(s) to the domain controller. If the specified DNS server does not function properly or is inaccessible, RMAD automatically selects DNS servers (primary and alternate) that were set on this domain controller before the recovery. If this action is also unsuccessful, RMAD selects DNS servers from a list of all DNS servers that are in use in the forest.
How does RMAD determine that the DNS server is available for use?
Recovery Manager for Active Directory (RMAD) sets a DNS server on all the network adapters on the domain controller and checks if it is enough to register DC Locator resource records and A-type (host) records. If the test succeeds, then this DNS server is set as the preferred DNS server on all network adapters.
| NOTE |
According to Microsoft recommendations, DNS servers should include their own IP addresses in the lists of DNS servers. The loopback address (127.0.0.1) should be configured only as a secondary or tertiary DNS server on a domain controller. If you specified the loopback address in the wrong sequence, the order will be corrected automatically when the list of DNS servers is configured on a domain controller. For more details, see DNS: DNS servers on <adapter name> should include the loopback address, but not as the first entry. |
If you want to use the manual DNS server selection method, it is recommended to make sure you have one or more DNS servers properly configured for working with the domain controllers being recovered. All these DNS servers must support dynamic updates and have DNS zones configured for each domain in the forest you want to recover. Make sure you specify one of these DNS servers for each domain controller in your recovery project.
Handling DNS servers during recovery
Active Directory® is tightly coupled with the DNS service. Each domain controller registers and constantly updates several Resource Records (RRs) in the DNS service. Each different type of domain controllers registers a separate set of RRs. During the forest recovery process, these records are adjusted by the Forest Recovery Console.
When you configure a Forest Recovery project, keep in mind the DNS infrastructure. In case of AD-integrated DNS, ensure that at least one DNS server per zone is restored from backup. The best practice is to restore as many DNS servers as possible from backup. You need to consider the Preferred DNS server option on every DC in the forest recovery project, in accordance with your DNS recovery strategy. For details, see Assigning a preferred DNS server during recovery. This DNS client configuration of restored DCs will be used to determine DNS infrastructure during recovery. Based on this information, Forest Recovery Console detects either AD-integrated DNS is used or external DNS and which DCs are used as DNS servers.
In case of AD-integrated DNS, you may have DNS infrastructure with the configured delegation and forwarding settings between parent and child domains. The Forest Recovery Console ensures that DNS zone information, delegation, forwarding settings, Forest and Domain DNS zone replication settings, and if applicable, Conditional Forwarders are restored during the forest recovery.
-
If a domain is removed from the restored forest, its delegation settings are removed as well.
-
If an external DNS is used, any inter-domain DNS relations are out of the Forest Recovery Console scope and are not affected by the forest recovery process.
-
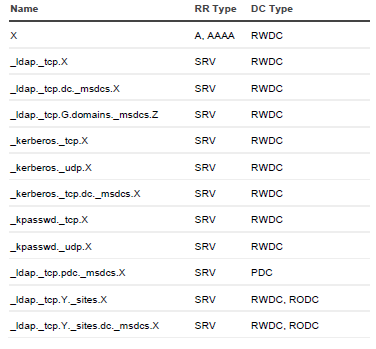
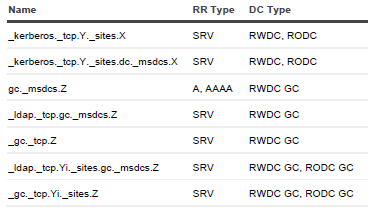
For DNS servers that have not been restored, its RRs associated with the DNS server are removed. This is performed during the Configure DNS server step. The following RRs are removed where Z is the forest FQDN, X is the domain default NC FQDN, Y is the site name.

- If the forest recovery project contains several DCs which are not restored, its RRs are removed from DNS. This is performed during the Clean up DNS records of removed domain controllers step. Note that if some DCs were excluded from the forest recovery process, but still running, and the DNS server accepts non-secure dynamic updates, then such DCs can still register its SRV records. The following RRs are removed where Z is the forest FQDN, X is the default NC FQDN, Y is the site name and G is the NC X's GUID.
-
When the forest recovery project contains several DCs with IP addresses other than the addresses they originally had (so-called re-IPing technique), then its host RRs are adjusted according to its new IP addresses.
-
For a DC with the "Reinstall Active Directory" recovery method, if such DC was AD-integrated DNS server, it will remain the DNS server after the reinstall.
-
For a DC with the "Install Active Directory" recovery method, the DC will not be the DNS server after the recovery even the AD-integrated DNS is configured for the domain.
Forest recovery approaches
Before you choose one of the recovery approaches described in this section, it is strongly recommended that you read Microsoft’s best-practice paper, Active Directory Forest Recovery Guide.
This section covers the following:
-
Recovery approach 1: Restore as many domain controllers from backups as possible
-
Recovery approach 2: Restore one domain controller from backup in each domain
Recovery approach 1: Restore as many domain controllers from backups as possible
To use this approach, you must have recent and trusted backups for as many domain controllers as possible in each domain in the forest. These backups must be created at a similar point in time to mitigate the risk of discrepancy after the forest is recovered.
At a high level, Approach 1 includes the following stages:
-
Recovery Manager for Active Directory restores as many domain controllers as possible in each domain from the recent and trusted backups you specify. The more domain controllers you restore from backups, the faster the forest recovery operation completes.
-
Recovery Manager for Active Directory uses Microsoft tools (Dcpromo.exe or the Uninstall-ADDSDomainController and Install-ADDSDomainController cmdlets) to automatically reinstall Active Directory on the domain controllers for which no backups are available.
-
The domain controllers where Active Directory was reinstalled replicate AD data from the domain controllers restored from reliable backups.
Approach 1 has the following advantages and limitations:
Advantages
-
Fast recovery of the entire forest. Since most domain controllers are simultaneously restored from backups, the forest recovery operation completes faster than in Approach 2.
-
Stability of the forest recovery process. Owing to the large number of backups used, the entire forest is recovered even if the restore of some domain controllers fails.
-
This approach allows you to retain the original forest infrastructure. Since many domain controllers are restored from backups, the recovered forest is close to its original pre-failure condition.
Limitations
- The risk of reintroducing corrupted or unwanted data is higher than in Approach 2. Because of the large number of backups used in this Approach, there is no guarantee that corrupted or unwanted data from the backups will not be reintroduced into the recovered forest.
For a step-by-step procedure on how to perform a forest recovery, Overview of steps to recover a forest
