Configuring Multiple Instances for Monitoring using Silent Installation
|
1 |
|
3 |
|
• |
README.txt file |
|
• |
mssql_cli_installer.groovy — a groovy script file that runs the silent installation. This file should be copied to the <FMS_HOME>/bin directory. |
|
• |
silent_installer_input_template.csv — a template file that should serve as the basis for inserting contents into the input CSV file. This file can be copied to any folder of your choice, if the path indicated by the <csv_instances_file_name> parameter (see below) points to the selected path. For details about the contents of this file, see Contents of the Input CSV File . |
|
• |
MSSQLPermissionsCheck.sql — this file contains the SQL that the user should run on the monitored instance to check permissions needed for monitoring |
|
• |
MSSQLPermissionsGrant.sql — this file contains the SQL that the user should run on the monitored instance in order to grant the instance the required permissions for monitoring. |
|
5 |
Copy the mssql_cli_installer.groovy file to the <FMS_HOME>/bin directory. |
|
6 |
Go to the command line and run the command: <FMS_HOME>/bin/fglcmd -srv <fms_host_name> -port <fms_url_port> -usr <fms_user_name> -pwd <fms_user_password> -cmd script:run -f mssql_cli_installer.groovy fglam_name <fglam_name> instances_file_name <csv_instances_file_name> lockbox_name <lockbox_name> lockbox_password <lockbox_password> |
|
• |
A file with the input file's name and _status suffix (for example: if the input file is named input, this file is named **input_new_-_**). |
|
• |
A file with input file's name and _new suffix (for example: if the input file is named input, this file is named input_status). |
Contents of the Input CSV File
The input CSV file contains the following fields, which are used as columns in the resulting file:
Configuring the On Demand Data Port on the Agent Manager Concentrator
|
1 |
|
2 |
Click Create Agent. |
|
3 |
Select the agent type DB_SQL_Server_Concentrator. |
|
5 |
Click Create. |
|
2 |
Click Edit Properties. |
|
3 |
Click Modify properties for this agent only. |
|
6 |
Click Edit to edit the list of downstream Agent Managers. |
|
7 |
Click Add Row. |
|
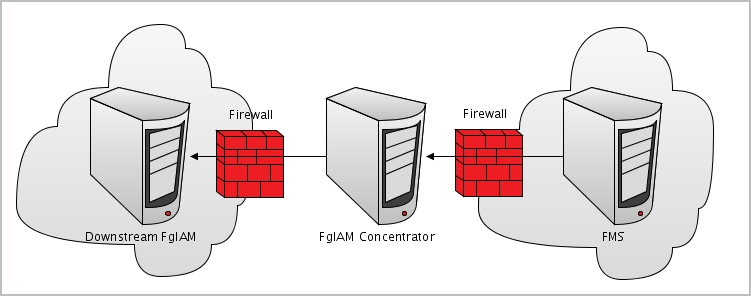
IMPORTANT: When editing the properties of the Foglight Agent Manager concentrator (Dashboards > Administration > Agents > Agent Status), the name of the Foglight Agent Manager should be entered in the Downstream FglAMs section exactly as it appears in the topology, under Home > Agents > All agents > <Agent name> > RMI data > FglAM host property. The <Agent name> parameter refers to the Foglight for SQL Server agents that reside on the selected Foglight Agent Manager. |
|
10 |
Click Save Changes. |
|
11 |
Click Save at the lower right corner of the screen. |
|
12 |
Click Back to Agent Status. |
|
14 |
Click Activate. |
|
15 |
Click OK to complete the process. |