Set-CAThreatDetectionConfiguration
Use this command to modify the list of allowed coordinators for the Threat Detection configuration.
|
A connection obtained by using the Connect-CAClient command. See Connecting to Change Auditor. | |
Example: Modifying a configuration
Example: To clear a previous list of allowed coordinators
Set-CAThreatDetectionConfiguration -Connection $connection -AllowedCoordinators @()
Remove-CAThreatDetectionConfiguration
Use this command to remove a Threat Detection configuration.
|
A connection obtained by using the Connect-CAClient command. See Connecting to Change Auditor. |
Example: Remove the Threat Detection configuration
Remove-CAThreatDetectionConfiguration -Connection $connection
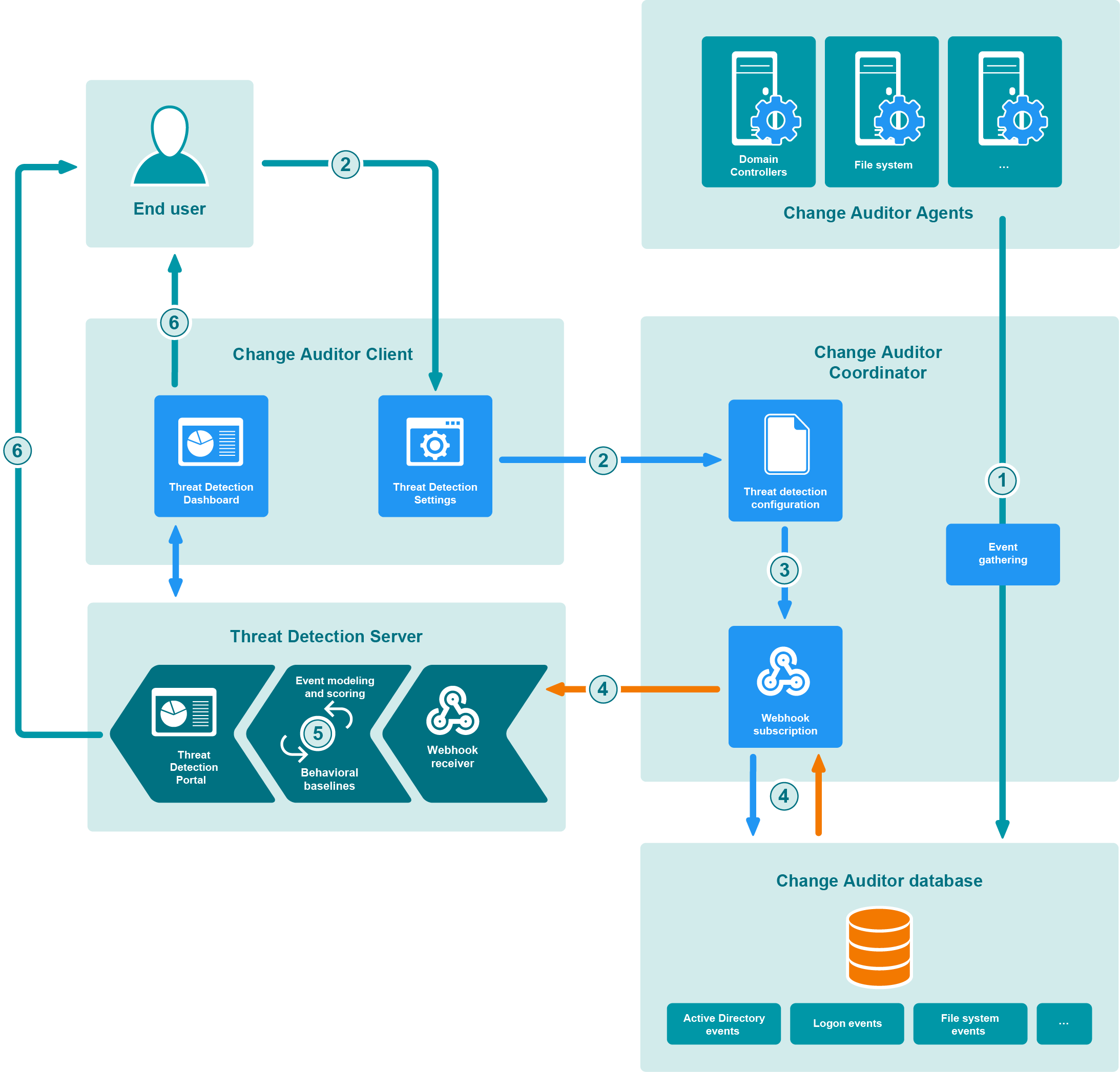
Appendix: System Architecture
Threat Detection system overview
The integration process to analyze events includes the following: