Overview of Data Handled by Binary Tree Power365
Tenant-to-Tenant Migrations
Power365 Tenant-to-Tenant migrations collect data for a variety of Azure Active Directory objects. The directory locations and objects collected are configurable to ensure only the desired objects are processed.
-
Directory objects are processed using Microsoft Graph API and PowerShell.
-
Objects include users, groups, contacts, teams, and Microsoft 365 groups.
-
Properties include account name, email addresses, contact information, department, membership and more.
-
Access to Azure Active Directory is granted by the customer using the Microsoft Admin Consent process and requires administrative credentials. Customers can revoke Admin Consent at any time. See https://msdn.microsoft.com/en-us/skype/trusted-application-api/docs/tenantadminconsent for details.
-
Power365 does not store credentials for administrative accounts.
-
Power365 generates and manages dedicated service accounts in each Microsoft 365 tenant used for PowerShell queries. The service accounts password is randomly generated to be unique and highly complex. The password is also encrypted with AES 256-bit encryption using Azure Key Vault and is never stored unencrypted.
-
Power365 service accounts are assigned access to individual mailboxes that are in scope for content migration. This access is removed after migration, if configured from the user interface.
-
Messages for mailboxes, public folders and Team channels are temporarily stored during migration and deleted as soon as they are written to the target. The temporarily stored messages are encrypted using AES symmetric-key encryption with a 256-bit key that is unique per message, randomly generated and only held in memory.
-
OneDrive and other Teams content is streamed directly from the source to the target environment.
-
Power365 can be configured to migrate Outlook, Teams and OneDrive accounts when an end user downloads and runs the Power365 Desktop Agent. No data is collected by the agent. Settings related to Outlook, Teams and OneDrive are modified to redirect end users to their migrated account(s).
Email Rewrite Service
Power365 rewrites email message recipients to provide seamless message delivery during migration of users, groups, and domains.
-
Email messages are temporarily stored during processing and deleted as soon as they are written to the target. The temporarily stored messages are encrypted using AES symmetric-key encryption with a 256-bit key that is unique per message, randomly generated and only held in memory.
Directory Synchronization & Migration
Power365 Directory Synchronization collects data for a variety of on premises and Azure active directory objects. The directory locations, objects and properties collected are configurable to ensure only the desired objects and properties are processed.
Azure Active Directory
-
Directory objects are processed using Microsoft Graph API and PowerShell.
-
Objects include users, groups, contacts, teams, and Microsoft 365 groups.
-
Properties include account name, email addresses, contact information, department, membership and more.
-
Access to Azure Active Directory is granted by the customer using the Microsoft Admin Consent process and requires administrative credentials. Customers can revoke Admin Consent at any time. See https://msdn.microsoft.com/en-us/skype/trusted-application-api/docs/tenantadminconsent for details.
-
Power365 does not store credentials for administrative accounts.
-
Power365 generates and manages dedicated service accounts in each Microsoft 365 tenant used for PowerShell queries. The service accounts password is randomly generated to be unique and highly complex. The password is also encrypted with AES 256-bit encryption using Azure Key Vault and is never stored unencrypted.
On Premises Active Directory
-
On-premises directory sync agents, running within the customers network, process Active Directory objects using LDAP or LDAPS (TLS 1.2) as configured within the user interface. Objects include users, groups, contacts, computers, and servers. Object properties include account name, email addresses, contact information, department, membership and more.
-
When the optional password sync feature is enabled, the password hash of all user accounts in scope are collected and stored encrypted with AES256 in Azure SQL Storage. The AES256 bit key is stored in Azure Key Vault. Once co-existence is no longer required for a specific user, the customer should use the reconcile option to ensure that information is promptly deleted.
-
On-premises directory sync agents, running within the customers network, securely encrypt and store administrative credentials locally on the agent’s computer.
-
On-premises device agents running locally on the end user’s workstation collect device properties using WMI and PowerShell. Device properties include device name, domain name, user profile locations and more.
-
Power365 optionally stores credentials required for network share re-permission and Active Directory domain joins. These credentials are provided by migration operators, encrypted with AES 256-bit encryption using Azure Key Vault and are never stored unencrypted.
Admin Consent and Service Principals
Power365 requires access to the customer’s Azure Active Directory and Office 365 tenants. The customer grants that access using the Microsoft Admin Consent process, which will create a Service Principal in the customer's Azure Active Directory with minimum consents required. The Service Principal is created using Microsoft's OAuth auth code grant flow https://docs.microsoft.com/en-us/azure/active-directory/develop/v2-oauth2-auth-code-flow
Customers can revoke Admin Consent at any time. See https://docs.microsoft.com/en-us/azure/activedirectory/manage-apps/delete-application-portal and https://docs.microsoft.com/en-us/skype-sdk/trustedapplication-api/docs/tenantadminconsent for details.
Below is the Admin Consent screen, see Operational Security > Permissions Required to Configure and Operate for a complete list of permissions required by Power365.
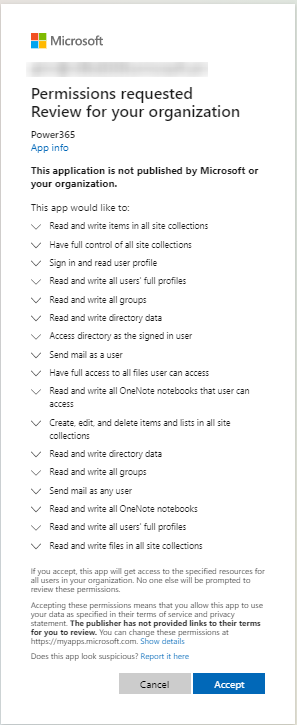
Location of Customer Data
When a customer signs up for Power365, they select the region in which to run their Power365 organization. All computation is performed in and all customer data is stored in the selected region. The currently supported regions are the United States, Australia, and European Union. Other regions may be added over time. Power365 customer data is stored in the selected region, entirely within Azure Services provided by Microsoft. For more information, see Achieving Compliant Data Residency and Security with Azure.
-
Customer data is stored in Azure SQL and is automatically replicated for failover using Azure SQL Active Geo replication. See this Microsoft reference for details: https://docs.microsoft.com/en-us/azure/azure-sql/database/active-geo-replication-overview
-
Application data and logs are stored in Azure storage tables. Windows Azure Storage, including the Blobs, Tables and Queues storage structures, by default get replicated three times in the same datacenter for resiliency against hardware failure. The data are replicated across different fault domains to increase availability. All replication datacenters reside with the geographic boundaries of the selected region. See this Microsoft reference for details: https://docs.microsoft.com/en-us/azure/storage/storageredundancy
-
DKIM and TLS certificates used by Power365 Email Rewrite Services are stored in Microsoft Key Vault.
Privacy and Protection of Customer Data
-
All data is secured at rest using SQL Transparent Data Encryption (TDE) with Microsoft managed keys. For more information see https://docs.microsoft.com/en-us/azure/azure-sql/database/transparent-data-encryption-tde-overview
-
Azure storage account data is secured at rest using storage service encryption with Microsoft managed keys. For more information see https://docs.microsoft.com/en-us/azure/storage/common/storage-service-encryption
-
Service account passwords and password hashes (while already encrypted at-rest) are additionally encrypted with AES 256-bit encryption using Azure Key Vault.
-
Power365 Migration encrypts mailbox and public folders messages using AES encryption and a unique, randomly generated 256-bit key that is unique per message and only held in memory.
-
Power365 Email Rewrite Services encrypts email messages using AES encryption and a unique, randomly generated 256-bit key that is unique per message and only held in memory.
