Quest GPOADmin Quick Start Guide
About this guide
Product overview
Security issues are becoming paramount within organizations. Within Active Directory, Group Policy Objects (GPOs) are at the forefront of an organization's ability to roll out functional security. Core aspects such as password policies, logon hours, software distribution, and other crucial security settings are handled through GPOs. Organizations need methods to control the settings of these GPOs and to deploy GPOs in a meaningful and safe manner with confidence. Since GPOs are so important to the proper operating of the Active Directory, organizations also need methods to restore GPOs when they are either incorrectly updated or corrupt. Windows Group Policy is powerful but difficult to manage. Uncontrolled changes can have disastrous consequences. For example, unplanned effects of a GPO change could prohibit hundreds of users from logging on, exclude access to critical software applications, or expose system settings. The Group Policy Management Console (GPMC) from Microsoft is a useful tool for the individual administrator, but additional functionality—such as GPO check in/check out, change control, and rollback—is needed to effectively manage GPOs across the enterprise.
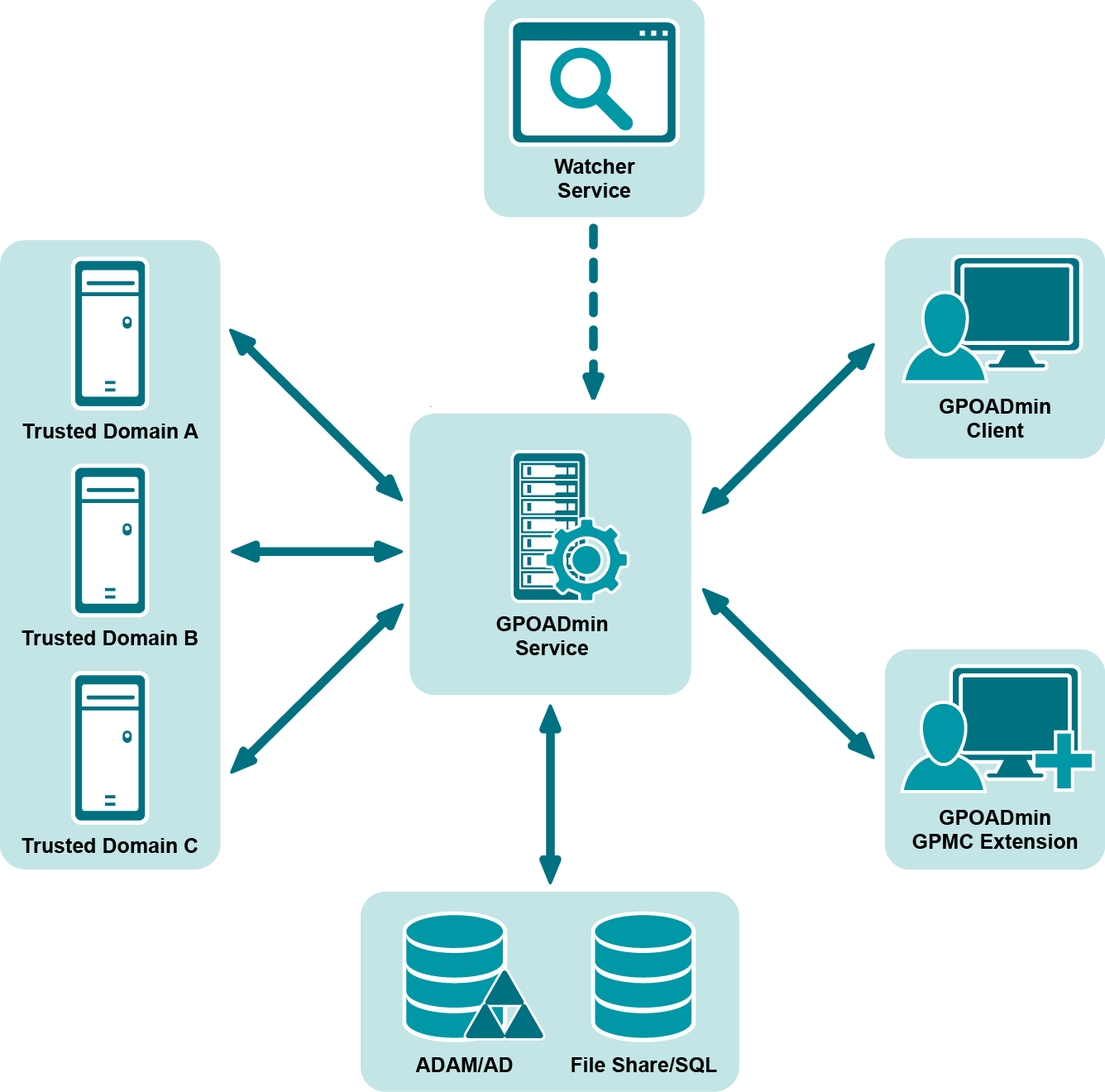
GPOADmin architecture
For all Active Directory deployments, the application information along with the GPOADmin Version Control System is stored in the configuration container of Active Directory in the following location:
CN=QGPM,CN=Quest,CN=Services,CN=Configuration,DC=Domain,DC=com
Where if you drilled down on the GPOADmin container you will find the following directories:
Active Directory Lightweight Directory Services (AD/LDS) deployments
- セルフ・サービス・ツール
- ナレッジベース
- 通知および警告
- 製品別サポート
- ソフトウェアのダウンロード
- 技術文書
- ユーザーフォーラム
- ビデオチュートリアル
- RSSフィード